K8S部署前端視覺化dashboard外掛(坑已踩完)
部署Dashboard
官方參考文件:
https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/
github專案地址:
https://github.com/kubernetes/dashboard
當前部署dashboard版本:v2.0.0,注意檢查dashboard版本與kubernetes版本相容性:
https://github.com/kubernetes/dashboard/releases
方法一:不推薦(新手找不到yaml的本地路徑)
執行yaml檔案直接部署:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.3/aio/deploy/recommended.yaml
檢視dashboard執行狀態,以deployment方式部署,執行2個pod及2個service:
[root@master ~]# kubectl -n kubernetes-dashboard get pods
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-694557449d-wfv4b 1/1 Running 0 4m50s
kubernetes-dashboard-9774cc786-v9ltx 1/1 Running 0 4m50s
[root@master ~]# kubectl -n kubernetes-dashboard get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.100.165.238 <none> 8000/TCP 4m52s
kubernetes-dashboard ClusterIP 10.109.218.125 <none> 443/TCP 4m52s
存取dashboard
這裏作爲演示,使用nodeport方式將dashboard服務暴露在叢集外,指定使用30443埠,可自定義:
kubectl patch svc kubernetes-dashboard -n kubernetes-dashboard \
-p '{"spec":{"type":"NodePort","ports":[{"port":443,"targetPort":8443,"nodePort":30443}]}}'
檢視暴露的service,已修改爲nodeport型別:
# kubectl -n kubernetes-dashboard get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.102.18.37 <none> 8000/TCP 69s
kubernetes-dashboard NodePort 10.110.118.188 <none> 443:30443/TCP 69s
方法二:推薦
下載yaml檔案手動修改service部分
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.3/aio/deploy/recommended.yaml
yaml檔案會下載到當前路徑下
修改yaml檔案
vi recommended.yaml
修改Service部分
-----------------------------------------------
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30443
selector:
k8s-app: kubernetes-dashboard
----------------------------------------------
注意如果這裏的nodePort寫成nodeport或者存在其他書寫問題,就會報如下的錯
[root@ks-allinone k8s-ui]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard unchanged
serviceaccount/kubernetes-dashboard unchanged
error: error validating "recommended.yaml": error validating data: ValidationError(Service.spec.ports[0]): unknown field "nodeport" in io.k8s.api.core.v1.ServicePort; if you choose to ignore these errors, turn validation off with --validate=false
更新設定
kubectl apply -f recommended.yaml
登錄dashboard
瀏覽器存取dashboard:
https://<any_node_ip>:30443
出現如下頁面
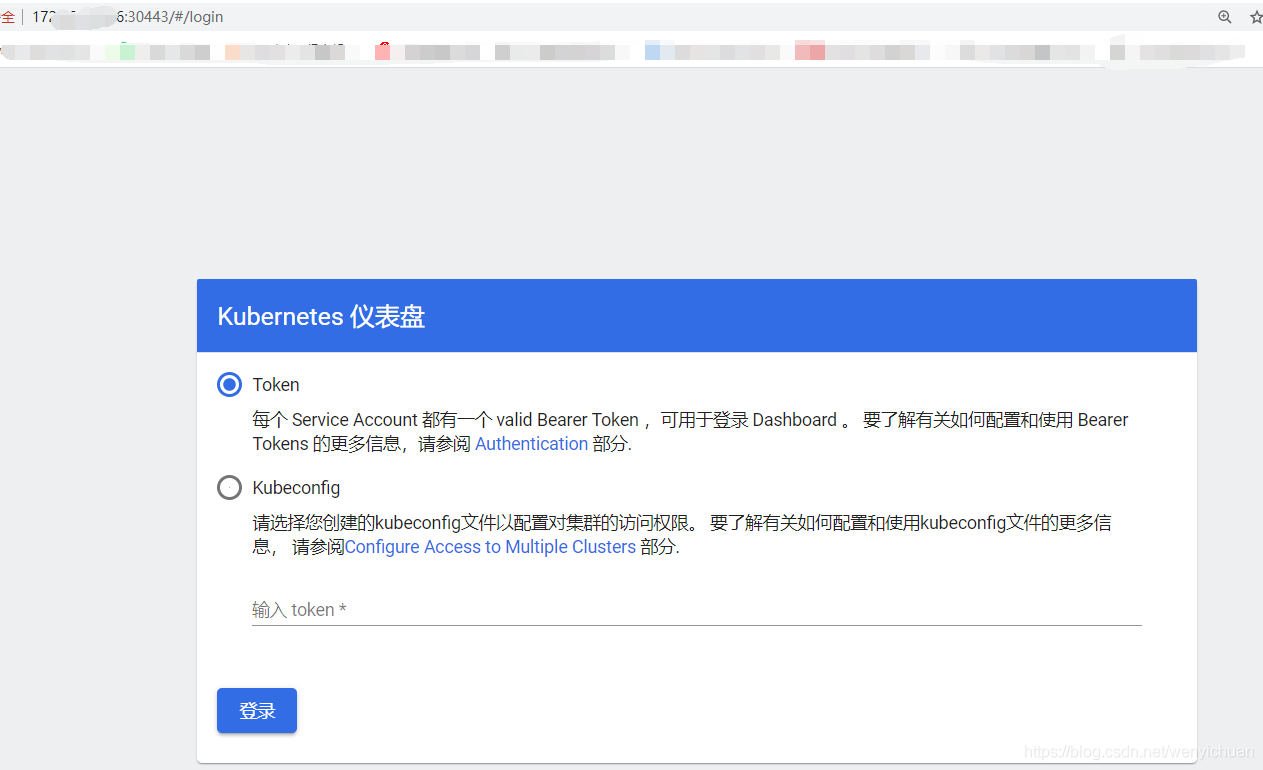
Dashboard 支援 Kubeconfig 和 Token 兩種認證方式,我們這裏選擇Token認證方式登錄。
官方參考文件:
https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md
建立dashboard-adminuser.yaml:
[root@ks-allinone k8s-ui]# cat > dashboard-adminuser.yaml << EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
> EOF
建立登錄使用者
[root@ks-allinone k8s-ui]# kubectl apply -f dashboard-adminuser.yaml
serviceaccount/admin-user created
clusterrolebinding.rbac.authorization.k8s.io/admin-user created
說明:上面建立了一個叫admin-user的服務賬號,並放在kubernetes-dashboard 名稱空間下,並將cluster-admin角色系結到admin-user賬戶,這樣admin-user賬戶就有了管理員的許可權。預設情況下,kubeadm建立叢集時已經建立了cluster-admin角色,我們直接系結即可。
檢視admin-user賬戶的token
kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}')
[root@ks-allinone k8s-ui]# kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}')
Name: admin-user-token-k42wt
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: 77d89b66-c70c-4784-8b8d-b18a2dc203a8
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjZUQU44UXNLREhCVm05RWZhb2h3TGRQQk5ZdF9jQjdfcnNXRVkzWldnbWcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLWs0Mnd0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI3N2Q4OWI2Ni1jNzBjLTQ3ODQtOGI4ZC1iMThhMmRjMjAzYTgiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.Z6Pn_bf9yi9a9wAGRe71dlAUgNqaH9gU5IksRCk0exfA-RokeU03NTNVd9ZqpH-_6w-rfeozsvDS2IymMqtIuH1F3RqNWORc9_aLw-6xTL-X8HaupGZgR5M0v3J286KjHTyU-ZqJ0Zoq1T0gGHdPSJTfwzV9WTz-tniOSjvjkkGuC-CLADmadLrdOprKfIMQ0HmkHIxOzlRX6WJc1f5vbbB0K72A_dZxXI94bRs6TtLAilBU_F3MffPiLLgHPV1GJPOwKD2AAkGz1hNrLAuxpMGlEelDsjqxWZJnRARnZ97gpma0oSkmZg7-hkYHN4dcNTmwWLhbmkhWycOXZpFEYw
把獲取到的Token複製到登錄介面的Token輸入框中,登陸成功。