監控Kubernetes叢集證書過期時間的三種方案
前言
Kubernetes 中大量用到了證書, 比如 ca證書、以及 kubelet、apiserver、proxy、etcd等元件,還有 kubeconfig 檔案。
如果證書過期,輕則無法登入 Kubernetes 叢集,重則整個叢集異常。
為了解決證書過期的問題,一般有以下幾種方式:
- 大幅延長證書有效期,短則 10年,長則 100 年;
- 證書快過期是自動輪換,如 Rancher 的 K3s,RKE2 就採用這種方式;
- 增加證書過期的監控,便於提早發現證書過期問題並人工介入
本次主要介紹關於 Kubernetes 叢集證書過期的監控,這裡提供 3 種監控方案:
- 使用 Blackbox Exporter 通過 Probe 監控 Kubernetes apiserver 證書過期時間;
- 使用 kube-prometheus-stack 通過 apiserver 和 kubelet 元件監控獲取相關證書過期時間;
- 使用 enix 的 x509-certificate-exporter監控叢集所有node的
/etc/kubernetes/pki和/var/lib/kubelet下的證書以及 kubeconfig 檔案
方案一: Blackbox Exporter 監控 Kubernetes apiserver 證書過期時間
Blackbox Exporter 用於探測 HTTPS、HTTP、TCP、DNS、ICMP 和 grpc 等 Endpoint。在你定義 Endpoint 後,Blackbox Exporter 會生成指標,可以使用 Grafana 等工具進行視覺化。Blackbox Exporter 最重要的功能之一是測量 Endpoint 的可用性。
當然, Blackbox Exporter 探測 HTTPS 後就可以獲取到證書的相關資訊, 就是利用這種方式實現對 Kubernetes apiserver 證書過期時間的監控.
設定步驟
-
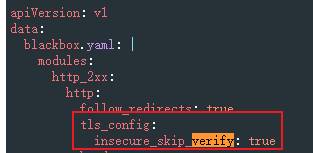
調整 Blackbox Exporter 的設定, 增加
insecure_tls_verify: true, 如下:
-
重啟 blackbox exporter:
kubectl rollout restart deploy ... -
增加對 Kubernetes APIServer 內部端點https://kubernetes.default.svc.cluster.local/readyz的監控.
-
如果你沒有使用 Prometheus Operator, 使用的是原生的 Prometheus, 則需要修改 Prometheus 組態檔的 configmap 或 secret, 新增 scrape config, 範例如下:
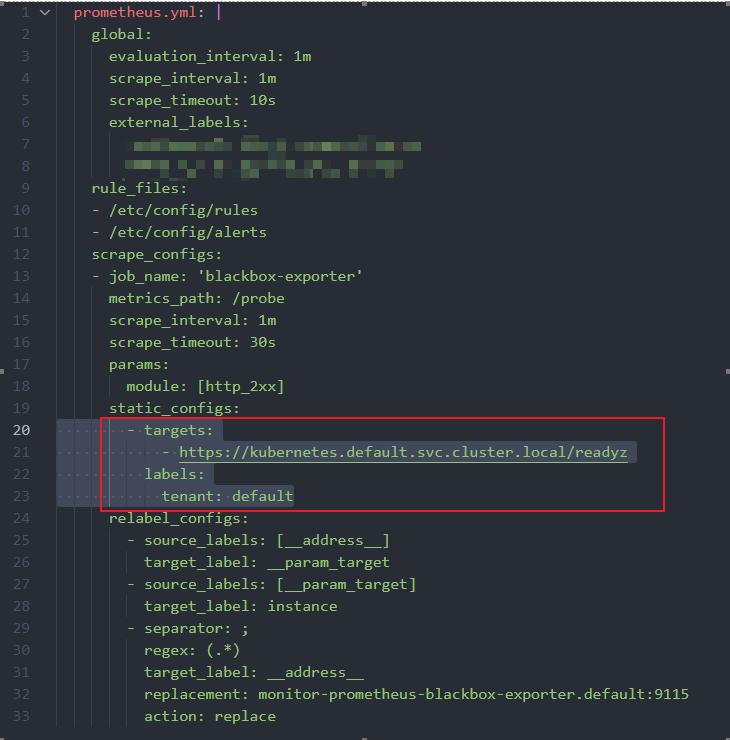
-
如果在使用 Prometheus Operator, 則可以增加如下 Probe CRD, Prometheus Operator 會自動將其轉換並 merge 到 Prometheus 中.
-
apiVersion: monitoring.coreos.com/v1
kind: Probe
metadata:
name: kubernetes-apiserver
spec:
interval: 60s
module: http_2xx
prober:
path: /probe
url: monitor-prometheus-blackbox-exporter.default.svc.cluster.local:9115
targets:
staticConfig:
static:
- https://kubernetes.default.svc.cluster.local/readyz
最後, 可以增加 Prometheus 告警 Rule, 這裡就直接用 Prometheus Operator 建立 PrometheusRule CRD 做範例了, 範例如下:
apiVersion: monitoring.coreos.com/v1
kind: PrometheusRule
metadata:
name: prometheus-blackbox-exporter
spec:
groups:
- name: prometheus-blackbox-exporter
rules:
- alert: BlackboxSslCertificateWillExpireSoon
expr: probe_ssl_earliest_cert_expiry - time() < 86400 * 30
for: 0m
labels:
severity: warning
- alert: BlackboxSslCertificateWillExpireSoon
expr: probe_ssl_earliest_cert_expiry - time() < 86400 * 14
for: 0m
labels:
severity: critical
- alert: BlackboxSslCertificateExpired
annotations:
description: |-
SSL certificate has expired already
VALUE = {{ $value }}
LABELS = {{ $labels }}
summary: SSL certificate expired (instance {{ $labels.instance }})
expr: probe_ssl_earliest_cert_expiry - time() <= 0
for: 0m
labels:
severity: emergency
效果

方案二: kube-prometheus-stack 通過 apiserver 和 kubelet 元件監控證書過期時間
這裡可以參考我的文章:Prometheus Operator 與 kube-prometheus 之二 - 如何監控 1.23+ kubeadm 叢集, 安裝完成後, 開箱即用.
開箱即用內容包括:
- 抓取 apiserver 和 kubelet 指標;(即 serviceMonitor)
- 設定證書過期時間的相關告警; (即 PrometheusRule)
這裡用到的指標有:
- apiserver
apiserver_client_certificate_expiration_seconds_countapiserver_client_certificate_expiration_seconds_bucket
- kubelet
kubelet_certificate_manager_client_expiration_renew_errorskubelet_server_expiration_renew_errorskubelet_certificate_manager_client_ttl_secondskubelet_certificate_manager_server_ttl_seconds
監控效果
對應的 Prometheus 告警規則如下:
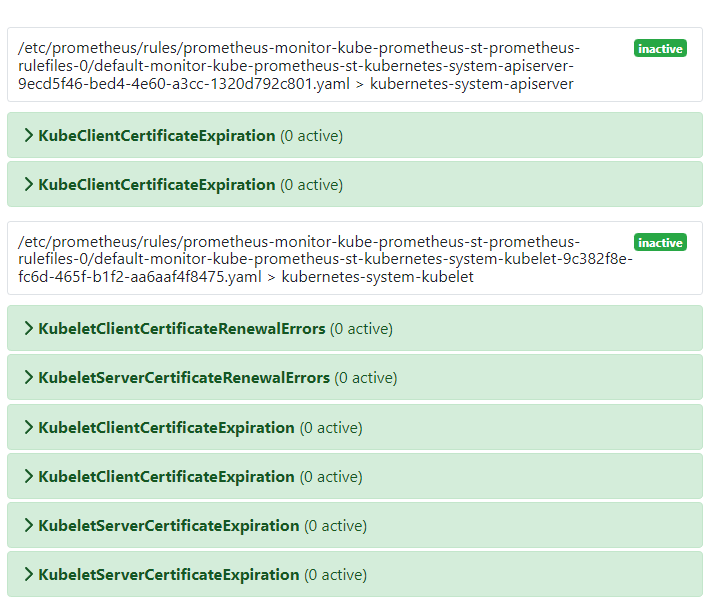
方案三: 使用 enix 的 x509-certificate-exporter
監控手段
該 Exporter 是通過監控叢集所有node的指定目錄或 path 下的證書檔案以及 kubeconfig 檔案來獲取證書資訊.
如果是使用 kubeadm 搭建的 Kubernetes 叢集, 則可以監控如下包含證書的檔案和 kubeconfig:
watchFiles:
- /var/lib/kubelet/pki/kubelet-client-current.pem
- /etc/kubernetes/pki/apiserver.crt
- /etc/kubernetes/pki/apiserver-etcd-client.crt
- /etc/kubernetes/pki/apiserver-kubelet-client.crt
- /etc/kubernetes/pki/ca.crt
- /etc/kubernetes/pki/front-proxy-ca.crt
- /etc/kubernetes/pki/front-proxy-client.crt
- /etc/kubernetes/pki/etcd/ca.crt
- /etc/kubernetes/pki/etcd/healthcheck-client.crt
- /etc/kubernetes/pki/etcd/peer.crt
- /etc/kubernetes/pki/etcd/server.crt
watchKubeconfFiles:
- /etc/kubernetes/admin.conf
- /etc/kubernetes/controller-manager.conf
- /etc/kubernetes/scheduler.conf
安裝設定
編輯 values.yaml:
kubeVersion: ''
extraLabels: {}
nameOverride: ''
fullnameOverride: ''
imagePullSecrets: []
image:
registry: docker.io
repository: enix/x509-certificate-exporter
tag:
pullPolicy: IfNotPresent
psp:
create: false
rbac:
create: true
secretsExporter:
serviceAccountName:
serviceAccountAnnotations: {}
clusterRoleAnnotations: {}
clusterRoleBindingAnnotations: {}
hostPathsExporter:
serviceAccountName:
serviceAccountAnnotations: {}
clusterRoleAnnotations: {}
clusterRoleBindingAnnotations: {}
podExtraLabels: {}
podAnnotations: {}
exposePerCertificateErrorMetrics: false
exposeRelativeMetrics: false
metricLabelsFilterList: null
secretsExporter:
enabled: true
debugMode: false
replicas: 1
restartPolicy: Always
strategy: {}
resources:
limits:
cpu: 200m
memory: 150Mi
requests:
cpu: 20m
memory: 20Mi
nodeSelector: {}
tolerations: []
affinity: {}
podExtraLabels: {}
podAnnotations: {}
podSecurityContext: {}
securityContext:
runAsUser: 65534
runAsGroup: 65534
readOnlyRootFilesystem: true
capabilities:
drop:
- ALL
secretTypes:
- type: kubernetes.io/tls
key: tls.crt
includeNamespaces: []
excludeNamespaces: []
includeLabels: []
excludeLabels: []
cache:
enabled: true
maxDuration: 300
hostPathsExporter:
debugMode: false
restartPolicy: Always
updateStrategy: {}
resources:
limits:
cpu: 100m
memory: 40Mi
requests:
cpu: 10m
memory: 20Mi
nodeSelector: {}
tolerations: []
affinity: {}
podExtraLabels: {}
podAnnotations: {}
podSecurityContext: {}
securityContext:
runAsUser: 0
runAsGroup: 0
readOnlyRootFilesystem: true
capabilities:
drop:
- ALL
watchDirectories: []
watchFiles: []
watchKubeconfFiles: []
daemonSets:
cp:
nodeSelector:
node-role.kubernetes.io/master: ''
tolerations:
- effect: NoSchedule
key: node-role.kubernetes.io/master
operator: Exists
watchFiles:
- /var/lib/kubelet/pki/kubelet-client-current.pem
- /etc/kubernetes/pki/apiserver.crt
- /etc/kubernetes/pki/apiserver-etcd-client.crt
- /etc/kubernetes/pki/apiserver-kubelet-client.crt
- /etc/kubernetes/pki/ca.crt
- /etc/kubernetes/pki/front-proxy-ca.crt
- /etc/kubernetes/pki/front-proxy-client.crt
- /etc/kubernetes/pki/etcd/ca.crt
- /etc/kubernetes/pki/etcd/healthcheck-client.crt
- /etc/kubernetes/pki/etcd/peer.crt
- /etc/kubernetes/pki/etcd/server.crt
watchKubeconfFiles:
- /etc/kubernetes/admin.conf
- /etc/kubernetes/controller-manager.conf
- /etc/kubernetes/scheduler.conf
nodes:
watchFiles:
- /var/lib/kubelet/pki/kubelet-client-current.pem
- /etc/kubernetes/pki/ca.crt
rbacProxy:
enabled: false
podListenPort: 9793
hostNetwork: false
service:
create: true
port: 9793
annotations: {}
extraLabels: {}
prometheusServiceMonitor:
create: true
scrapeInterval: 60s
scrapeTimeout: 30s
extraLabels: {}
relabelings: {}
prometheusPodMonitor:
create: false
prometheusRules:
create: true
alertOnReadErrors: true
readErrorsSeverity: warning
alertOnCertificateErrors: true
certificateErrorsSeverity: warning
certificateRenewalsSeverity: warning
certificateExpirationsSeverity: critical
warningDaysLeft: 30
criticalDaysLeft: 14
extraLabels: {}
alertExtraLabels: {}
rulePrefix: ''
disableBuiltinAlertGroup: false
extraAlertGroups: []
extraDeploy: []
通過 Helm Chart 安裝:
helm repo add enix https://charts.enix.io
helm install x509-certificate-exporter enix/x509-certificate-exporter
通過這個 Helm Chart 也會自動安裝:
- ServiceMonitor
- PrometheusRule
其監控指標為:
x509_cert_not_after
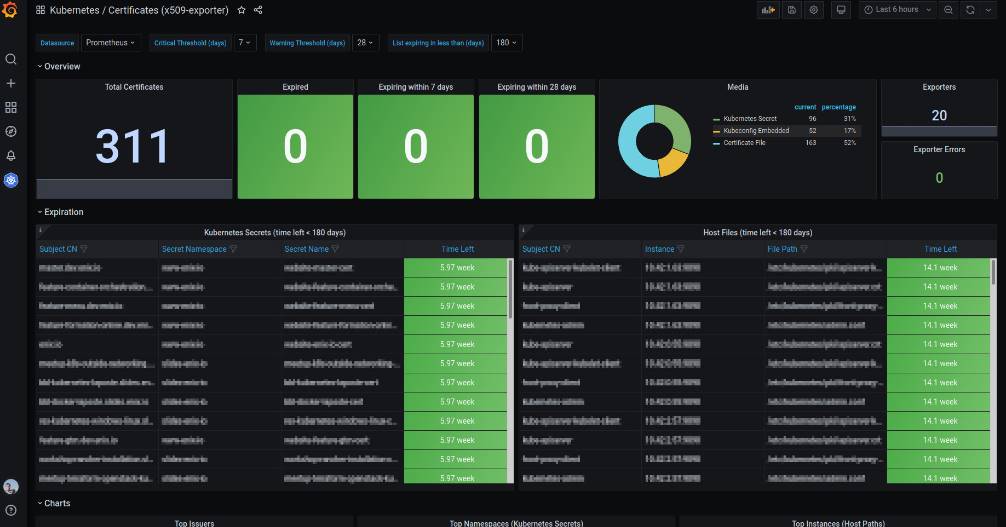
監控效果
該 Exporter 還提供了一個比較花哨的 Grafana Dashboard, 如下:
Alert Rules 如下:
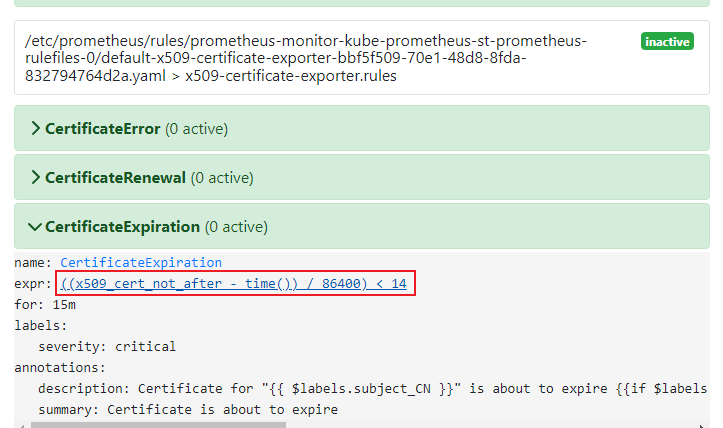
總結
為了監控 Kubernetes 叢集的證書過期時間, 我們提供了 3 種方案, 各有優劣:
- 使用 Blackbox Exporter 通過 Probe 監控 Kubernetes apiserver 證書過期時間;
- 優勢: 實現簡單;
- 劣勢: 只能監控 https 的證書;
- 使用 kube-prometheus-stack 通過 apiserver 和 kubelet 元件監控獲取相關證書過期時間;
- 優勢: 開箱即用, 安裝 kube-prometheus-stack 後無需額外安裝其他 exporter
- 劣勢: 只能監控 apiserver 和 kubelet 的證書;
- 使用 enix 的 x509-certificate-exporter監控叢集所有node的
/etc/kubernetes/pki和/var/lib/kubelet下的證書以及 kubeconfig 檔案- 優勢: 可以監控所有 node, 所有 kubeconfig 檔案, 以及 所有 tls 格式的 secret 證書, 如果要監控 Kubernetes 叢集以外的證書, 也可以如法炮製; 範圍廣而全;
- 需要額外安裝: x509-certificate-exporter, 對應有 1 個 Deployment 和 多個 DaemonSet, 對 Kubernetes 叢集的資源消耗不少.
可以根據您的實際情況靈活進行選擇.