驅動開發:核心運用LoadImage遮蔽驅動
在筆者上一篇文章《驅動開發:核心監視LoadImage映像回撥》中LyShark簡單介紹瞭如何通過PsSetLoadImageNotifyRoutine函數註冊回撥來監視驅動模組的載入,注意我這裡用的是監視而不是監控之所以是監視而不是監控那是因為PsSetLoadImageNotifyRoutine無法實現引數控制,而如果我們想要控制特定驅動的載入則需要自己做一些事情來實現,如下LyShark將解密如何實現遮蔽特定驅動的載入。
要想實現驅動遮蔽其原理很簡單,通過ImageInfo->ImageBase得到映象基地址,然後呼叫GetDriverEntryByImageBase函數來得到程式的入口地址,找NT頭的OptionalHeader節點,該節點裡面就是被載入驅動入口,通過組合在驅動頭部寫入ret返回指令,即可實現遮蔽載入特定驅動檔案。
原理其實很容易理解,如果我們需要實現則只需要在《驅動開發:核心監視LoadImage映像回撥》這篇文章的程式碼上稍加改進即可,當檢測到lyshark.sys驅動載入時,直接跳轉到入口處快速寫入一個Ret讓驅動返回即可,至於如何寫出指令的問題如果不懂建議回頭看看《驅動開發:核心CR3切換讀寫記憶體》文章中是如何讀寫記憶體的,這段程式碼實現如下所示。
// 署名權
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include <ntddk.h>
#include <intrin.h>
#include <ntimage.h>
PVOID GetDriverEntryByImageBase(PVOID ImageBase)
{
PIMAGE_DOS_HEADER pDOSHeader;
PIMAGE_NT_HEADERS64 pNTHeader;
PVOID pEntryPoint;
pDOSHeader = (PIMAGE_DOS_HEADER)ImageBase;
pNTHeader = (PIMAGE_NT_HEADERS64)((ULONG64)ImageBase + pDOSHeader->e_lfanew);
pEntryPoint = (PVOID)((ULONG64)ImageBase + pNTHeader->OptionalHeader.AddressOfEntryPoint);
return pEntryPoint;
}
VOID UnicodeToChar(PUNICODE_STRING dst, char *src)
{
ANSI_STRING string;
RtlUnicodeStringToAnsiString(&string, dst, TRUE);
strcpy(src, string.Buffer);
RtlFreeAnsiString(&string);
}
// 使用開關防寫需要在[C/C++]->[優化]->啟用內部函數
// 關閉防寫
KIRQL WPOFFx64()
{
KIRQL irql = KeRaiseIrqlToDpcLevel();
UINT64 cr0 = __readcr0();
cr0 &= 0xfffffffffffeffff;
_disable();
__writecr0(cr0);
return irql;
}
// 開啟防寫
void WPONx64(KIRQL irql)
{
UINT64 cr0 = __readcr0();
cr0 |= 0x10000;
_enable();
__writecr0(cr0);
KeLowerIrql(irql);
}
BOOLEAN DenyLoadDriver(PVOID DriverEntry)
{
UCHAR fuck[] = "\xB8\x22\x00\x00\xC0\xC3";
KIRQL kirql;
/* 在模組開頭寫入以下組合指令
Mov eax,c0000022h
ret
*/
if (DriverEntry == NULL) return FALSE;
kirql = WPOFFx64();
memcpy(DriverEntry, fuck, sizeof(fuck) / sizeof(fuck[0]));
WPONx64(kirql);
return TRUE;
}
VOID MyLySharkComLoadImageNotifyRoutine(PUNICODE_STRING FullImageName, HANDLE ModuleStyle, PIMAGE_INFO ImageInfo)
{
PVOID pDrvEntry;
char szFullImageName[256] = { 0 };
// MmIsAddress 驗證地址可用性
if (FullImageName != NULL && MmIsAddressValid(FullImageName))
{
// ModuleStyle為零表示載入sys
if (ModuleStyle == 0)
{
pDrvEntry = GetDriverEntryByImageBase(ImageInfo->ImageBase);
UnicodeToChar(FullImageName, szFullImageName);
if (strstr(_strlwr(szFullImageName), "lyshark.sys"))
{
DbgPrint("[LyShark] 攔截SYS核心模組:%s", szFullImageName);
DenyLoadDriver(pDrvEntry);
}
}
}
}
VOID UnDriver(PDRIVER_OBJECT driver)
{
PsRemoveLoadImageNotifyRoutine((PLOAD_IMAGE_NOTIFY_ROUTINE)MyLySharkComLoadImageNotifyRoutine);
DbgPrint("驅動解除安裝完成...");
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
{
DbgPrint("hello lyshark.com \n");
PsSetLoadImageNotifyRoutine((PLOAD_IMAGE_NOTIFY_ROUTINE)MyLySharkComLoadImageNotifyRoutine);
DbgPrint("驅動載入完成...");
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
首先執行我們的驅動,然後我們接著載入lyshark.sys則你會發現驅動被攔截了。
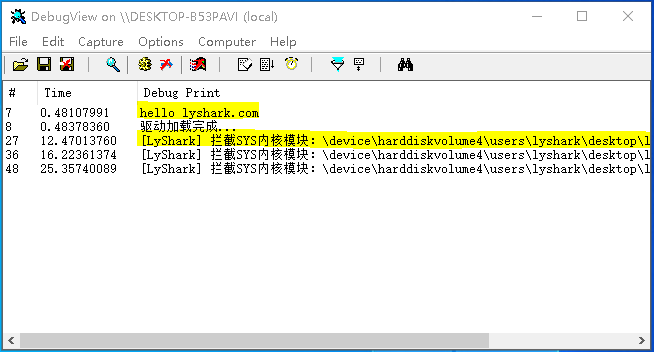
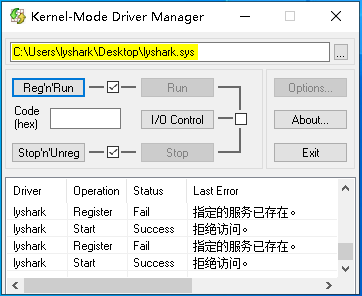
我們看下驅動載入器,提示的資訊是拒絕存取,因為這個驅動其實是載入了的,只是入口處被填充了返回而已。
除了使用Ret強制返回的方法意外,遮蔽驅動載入還可以使用另一種方式實現禁用模組載入,例如當驅動被載入首先回撥函數內可以接收到,當接收到以後直接呼叫MmUnmapViewOfSection函數強制解除安裝掉即可,如果使用這種方法實現則這段程式碼需要改進成如下樣子。
// 署名權
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include <ntifs.h>
#include <ntimage.h>
#include <intrin.h>
NTSTATUS MmUnmapViewOfSection(PEPROCESS Process, PVOID BaseAddress);
NTSTATUS SetNotifyRoutine();
NTSTATUS RemoveNotifyRoutine();
VOID LoadImageNotifyRoutine(PUNICODE_STRING FullImageName, HANDLE ProcessId, PIMAGE_INFO ImageInfo);
NTSTATUS U2C(PUNICODE_STRING pustrSrc, PCHAR pszDest, ULONG ulDestLength);
VOID ThreadProc(_In_ PVOID StartContext);
// 拒絕載入驅動
NTSTATUS DenyLoadDriver(PVOID pImageBase);
// 拒絕載入DLL模組
NTSTATUS DenyLoadDll(HANDLE ProcessId, PVOID pImageBase);
typedef struct _MY_DATA
{
HANDLE ProcessId;
PVOID pImageBase;
}MY_DATA, *PMY_DATA;
// 設定訊息回撥
NTSTATUS SetNotifyRoutine()
{
NTSTATUS status = STATUS_SUCCESS;
status = PsSetLoadImageNotifyRoutine(LoadImageNotifyRoutine);
return status;
}
// 關閉訊息回撥
NTSTATUS RemoveNotifyRoutine()
{
NTSTATUS status = STATUS_SUCCESS;
status = PsRemoveLoadImageNotifyRoutine(LoadImageNotifyRoutine);
return status;
}
VOID LoadImageNotifyRoutine(PUNICODE_STRING FullImageName, HANDLE ProcessId, PIMAGE_INFO ImageInfo)
{
DbgPrint("PID: %d --> 完整路徑: %wZ --> 大小: %d --> 基地址: 0x%p \n", ProcessId, FullImageName, ImageInfo->ImageSize, ImageInfo->ImageBase);
HANDLE hThread = NULL;
CHAR szTemp[1024] = { 0 };
U2C(FullImageName, szTemp, 1024);
if (NULL != strstr(szTemp, "lyshark.sys"))
{
// EXE或者DLL
if (0 != ProcessId)
{
// 建立多執行緒 延時1秒鐘後再解除安裝模組
PMY_DATA pMyData = ExAllocatePool(NonPagedPool, sizeof(MY_DATA));
pMyData->ProcessId = ProcessId;
pMyData->pImageBase = ImageInfo->ImageBase;
PsCreateSystemThread(&hThread, 0, NULL, NtCurrentProcess(), NULL, ThreadProc, pMyData);
DbgPrint("[LyShark] 禁止載入DLL檔案 \n");
}
// 驅動
else
{
DenyLoadDriver(ImageInfo->ImageBase);
DbgPrint("[LyShark] 禁止載入SYS驅動檔案 \n");
}
}
}
// 拒絕載入驅動
NTSTATUS DenyLoadDriver(PVOID pImageBase)
{
NTSTATUS status = STATUS_SUCCESS;
PMDL pMdl = NULL;
PVOID pVoid = NULL;
ULONG ulShellcodeLength = 16;
UCHAR pShellcode[16] = { 0xB8, 0x22, 0x00, 0x00, 0xC0, 0xC3, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90 };
PIMAGE_DOS_HEADER pDosHeader = pImageBase;
PIMAGE_NT_HEADERS pNtHeaders = (PIMAGE_NT_HEADERS)((PUCHAR)pDosHeader + pDosHeader->e_lfanew);
PVOID pDriverEntry = (PVOID)((PUCHAR)pDosHeader + pNtHeaders->OptionalHeader.AddressOfEntryPoint);
pMdl = MmCreateMdl(NULL, pDriverEntry, ulShellcodeLength);
MmBuildMdlForNonPagedPool(pMdl);
pVoid = MmMapLockedPages(pMdl, KernelMode);
RtlCopyMemory(pVoid, pShellcode, ulShellcodeLength);
MmUnmapLockedPages(pVoid, pMdl);
IoFreeMdl(pMdl);
return status;
}
// 呼叫 MmUnmapViewOfSection 函數來解除安裝已經載入的 DLL 模組
NTSTATUS DenyLoadDll(HANDLE ProcessId, PVOID pImageBase)
{
NTSTATUS status = STATUS_SUCCESS;
PEPROCESS pEProcess = NULL;
status = PsLookupProcessByProcessId(ProcessId, &pEProcess);
if (!NT_SUCCESS(status))
{
return status;
}
// 解除安裝模組
status = MmUnmapViewOfSection(pEProcess, pImageBase);
if (!NT_SUCCESS(status))
{
return status;
}
return status;
}
VOID ThreadProc(_In_ PVOID StartContext)
{
PMY_DATA pMyData = (PMY_DATA)StartContext;
LARGE_INTEGER liTime = { 0 };
// 延時 1 秒 負值表示相對時間
liTime.QuadPart = -10 * 1000 * 1000;
KeDelayExecutionThread(KernelMode, FALSE, &liTime);
// 解除安裝
DenyLoadDll(pMyData->ProcessId, pMyData->pImageBase);
ExFreePool(pMyData);
}
NTSTATUS U2C(PUNICODE_STRING pustrSrc, PCHAR pszDest, ULONG ulDestLength)
{
NTSTATUS status = STATUS_SUCCESS;
ANSI_STRING strTemp;
RtlZeroMemory(pszDest, ulDestLength);
RtlUnicodeStringToAnsiString(&strTemp, pustrSrc, TRUE);
if (ulDestLength > strTemp.Length)
{
RtlCopyMemory(pszDest, strTemp.Buffer, strTemp.Length);
}
RtlFreeAnsiString(&strTemp);
return status;
}
VOID UnDriver(PDRIVER_OBJECT driver)
{
PsRemoveLoadImageNotifyRoutine((PLOAD_IMAGE_NOTIFY_ROUTINE)RemoveNotifyRoutine);
DbgPrint("驅動解除安裝完成...");
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
{
DbgPrint("hello lyshark.ocm \n");
PsSetLoadImageNotifyRoutine((PLOAD_IMAGE_NOTIFY_ROUTINE)SetNotifyRoutine);
DbgPrint("驅動載入完成...");
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
載入這段驅動程式,當有DLL檔案被載入後,則會強制彈出,從而實現遮蔽模組載入的作用。
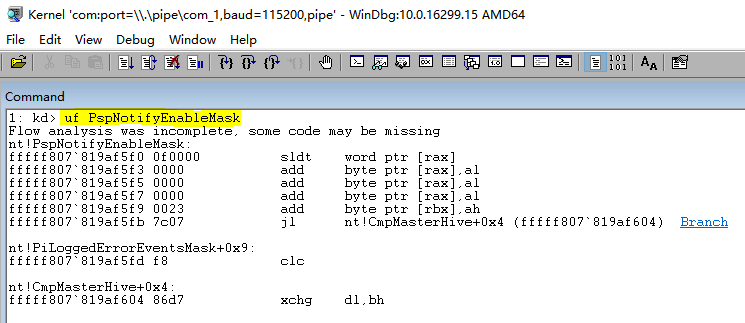
當然用LoadImage回撥做監控並不靠譜,因為它很容易被繞過,其實系統裡存在一個開關,叫做PspNotifyEnableMask如果它的值被設定為0,那麼所有的相關操作都不會經過回撥,所有回撥都會失效。
文章出處:https://www.cnblogs.com/LyShark/p/16819188.html
版權宣告:本部落格文章與程式碼均為學習時整理的筆記,文章 [均為原創] 作品,轉載請 [新增出處] ,您新增出處是我創作的動力!
轉載文章請遵守《中華人民共和國著作權法》相關法律規定或遵守《署名CC BY-ND 4.0國際》規範,合理合規攜帶原創出處轉載,如果不攜帶文章出處,並惡意轉載多篇原創文章被本人發現,本人保留起訴權!