驅動開發:核心列舉Registry登入檔回撥
2022-10-21 15:00:32
在筆者上一篇文章《驅動開發:核心列舉LoadImage映像回撥》中LyShark教大家實現了列舉系統回撥中的LoadImage通知訊息,本章將實現對Registry登入檔通知訊息的列舉,與LoadImage訊息不同Registry訊息不需要解密只要找到CallbackListHead訊息回撥連結串列頭並解析為_CM_NOTIFY_ENTRY結構即可實現列舉。
我們來看一款閉源ARK工具是如何實現的:

登入檔系統回撥的列舉需要通過特徵碼搜尋來實現,首先我們可以定位到uf CmUnRegisterCallback核心函數上,在該核心函數下方存在一個CallbackListHead連結串列節點,取出這個連結串列地址。
當得到登入檔連結串列入口0xfffff8063a065bc0直接將其解析為_CM_NOTIFY_ENTRY即可得到資料,如果要遍歷下一個連結串列則只需要ListEntryHead.Flink向下移動指標即可。
// 署名權
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
// 登入檔回撥函數結構體定義
typedef struct _CM_NOTIFY_ENTRY
{
LIST_ENTRY ListEntryHead;
ULONG UnKnown1;
ULONG UnKnown2;
LARGE_INTEGER Cookie;
PVOID Context;
PVOID Function;
}CM_NOTIFY_ENTRY, *PCM_NOTIFY_ENTRY;
要想得到此處的連結串列地址,需要先通過MmGetSystemRoutineAddress()獲取到CmUnRegisterCallback函數基址,然後在該函數起始位置向下搜尋,找到這個連結串列節點,並將其後面的基地址取出來,在上一篇《驅動開發:核心列舉LoadImage映像回撥》文章中已經介紹了定位方式此處跳過介紹,具體實現程式碼如下。
// 署名權
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include <ntifs.h>
#include <windef.h>
// 指定記憶體區域的特徵碼掃描
// PowerBy: LyShark.com
PVOID SearchMemory(PVOID pStartAddress, PVOID pEndAddress, PUCHAR pMemoryData, ULONG ulMemoryDataSize)
{
PVOID pAddress = NULL;
PUCHAR i = NULL;
ULONG m = 0;
// 掃描記憶體
for (i = (PUCHAR)pStartAddress; i < (PUCHAR)pEndAddress; i++)
{
// 判斷特徵碼
for (m = 0; m < ulMemoryDataSize; m++)
{
if (*(PUCHAR)(i + m) != pMemoryData[m])
{
break;
}
}
// 判斷是否找到符合特徵碼的地址
if (m >= ulMemoryDataSize)
{
// 找到特徵碼位置, 獲取緊接著特徵碼的下一地址
pAddress = (PVOID)(i + ulMemoryDataSize);
break;
}
}
return pAddress;
}
// 根據特徵碼獲取 CallbackListHead 連結串列地址
// PowerBy: LyShark.com
PVOID SearchCallbackListHead(PUCHAR pSpecialData, ULONG ulSpecialDataSize, LONG lSpecialOffset)
{
UNICODE_STRING ustrFuncName;
PVOID pAddress = NULL;
LONG lOffset = 0;
PVOID pCmUnRegisterCallback = NULL;
PVOID pCallbackListHead = NULL;
// 先獲取 CmUnRegisterCallback 函數地址
RtlInitUnicodeString(&ustrFuncName, L"CmUnRegisterCallback");
pCmUnRegisterCallback = MmGetSystemRoutineAddress(&ustrFuncName);
if (NULL == pCmUnRegisterCallback)
{
return pCallbackListHead;
}
// 查詢 fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
/*
lyshark.com>
nt!CmUnRegisterCallback+0x6b:
fffff806`3a4271ab 4533c0 xor r8d,r8d
fffff806`3a4271ae 488d542438 lea rdx,[rsp+38h]
fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
fffff806`3a4271ba e855e2e2ff call nt!CmListGetNextElement (fffff806`3a255414)
fffff806`3a4271bf 488bf8 mov rdi,rax
fffff806`3a4271c2 4889442440 mov qword ptr [rsp+40h],rax
fffff806`3a4271c7 4885c0 test rax,rax
fffff806`3a4271ca 0f84c7000000 je nt!CmUnRegisterCallback+0x157 (fffff806`3a427297) Branch
*/
pAddress = SearchMemory(pCmUnRegisterCallback, (PVOID)((PUCHAR)pCmUnRegisterCallback + 0xFF), pSpecialData, ulSpecialDataSize);
if (NULL == pAddress)
{
return pCallbackListHead;
}
// 先獲取偏移再計算地址
lOffset = *(PLONG)((PUCHAR)pAddress + lSpecialOffset);
pCallbackListHead = (PVOID)((PUCHAR)pAddress + lSpecialOffset + sizeof(LONG) + lOffset);
return pCallbackListHead;
}
VOID UnDriver(PDRIVER_OBJECT Driver)
{
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
{
PVOID pCallbackListHeadAddress = NULL;
RTL_OSVERSIONINFOW osInfo = { 0 };
UCHAR pSpecialData[50] = { 0 };
ULONG ulSpecialDataSize = 0;
LONG lSpecialOffset = 0;
DbgPrint("hello lyshark.com \n");
// 查詢 fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
/*
lyshark.com>
nt!CmUnRegisterCallback+0x6b:
fffff806`3a4271ab 4533c0 xor r8d,r8d
fffff806`3a4271ae 488d542438 lea rdx,[rsp+38h]
fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
fffff806`3a4271ba e855e2e2ff call nt!CmListGetNextElement (fffff806`3a255414)
fffff806`3a4271bf 488bf8 mov rdi,rax
fffff806`3a4271c2 4889442440 mov qword ptr [rsp+40h],rax
fffff806`3a4271c7 4885c0 test rax,rax
fffff806`3a4271ca 0f84c7000000 je nt!CmUnRegisterCallback+0x157 (fffff806`3a427297) Branch
*/
pSpecialData[0] = 0x48;
pSpecialData[1] = 0x8D;
pSpecialData[2] = 0x0D;
ulSpecialDataSize = 3;
// 根據特徵碼獲取地址
pCallbackListHeadAddress = SearchCallbackListHead(pSpecialData, ulSpecialDataSize, lSpecialOffset);
DbgPrint("[LyShark.com] CallbackListHead => %p \n", pCallbackListHeadAddress);
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
執行這段程式碼,並可得到登入檔回撥入口地址,輸出效果如下所示:
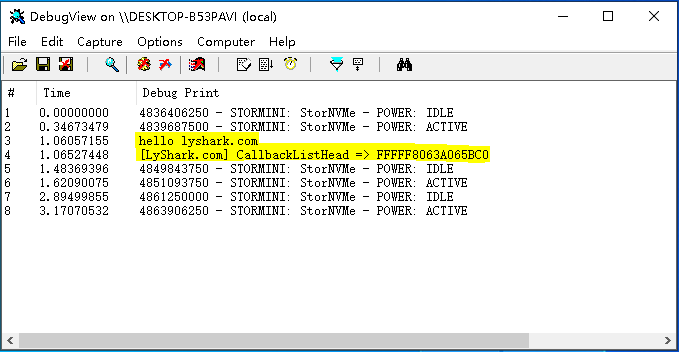
得到了登入檔回撥入口地址,接著直接回圈遍歷輸出這個連結串列即可得到所有的登入檔回撥。
// 署名權
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include <ntifs.h>
#include <windef.h>
// 指定記憶體區域的特徵碼掃描
// PowerBy: LyShark.com
PVOID SearchMemory(PVOID pStartAddress, PVOID pEndAddress, PUCHAR pMemoryData, ULONG ulMemoryDataSize)
{
PVOID pAddress = NULL;
PUCHAR i = NULL;
ULONG m = 0;
// 掃描記憶體
for (i = (PUCHAR)pStartAddress; i < (PUCHAR)pEndAddress; i++)
{
// 判斷特徵碼
for (m = 0; m < ulMemoryDataSize; m++)
{
if (*(PUCHAR)(i + m) != pMemoryData[m])
{
break;
}
}
// 判斷是否找到符合特徵碼的地址
if (m >= ulMemoryDataSize)
{
// 找到特徵碼位置, 獲取緊接著特徵碼的下一地址
pAddress = (PVOID)(i + ulMemoryDataSize);
break;
}
}
return pAddress;
}
// 根據特徵碼獲取 CallbackListHead 連結串列地址
// PowerBy: LyShark.com
PVOID SearchCallbackListHead(PUCHAR pSpecialData, ULONG ulSpecialDataSize, LONG lSpecialOffset)
{
UNICODE_STRING ustrFuncName;
PVOID pAddress = NULL;
LONG lOffset = 0;
PVOID pCmUnRegisterCallback = NULL;
PVOID pCallbackListHead = NULL;
// 先獲取 CmUnRegisterCallback 函數地址
RtlInitUnicodeString(&ustrFuncName, L"CmUnRegisterCallback");
pCmUnRegisterCallback = MmGetSystemRoutineAddress(&ustrFuncName);
if (NULL == pCmUnRegisterCallback)
{
return pCallbackListHead;
}
// 查詢 fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
/*
lyshark.com>
nt!CmUnRegisterCallback+0x6b:
fffff806`3a4271ab 4533c0 xor r8d,r8d
fffff806`3a4271ae 488d542438 lea rdx,[rsp+38h]
fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
fffff806`3a4271ba e855e2e2ff call nt!CmListGetNextElement (fffff806`3a255414)
fffff806`3a4271bf 488bf8 mov rdi,rax
fffff806`3a4271c2 4889442440 mov qword ptr [rsp+40h],rax
fffff806`3a4271c7 4885c0 test rax,rax
fffff806`3a4271ca 0f84c7000000 je nt!CmUnRegisterCallback+0x157 (fffff806`3a427297) Branch
*/
pAddress = SearchMemory(pCmUnRegisterCallback, (PVOID)((PUCHAR)pCmUnRegisterCallback + 0xFF), pSpecialData, ulSpecialDataSize);
if (NULL == pAddress)
{
return pCallbackListHead;
}
// 先獲取偏移再計算地址
lOffset = *(PLONG)((PUCHAR)pAddress + lSpecialOffset);
pCallbackListHead = (PVOID)((PUCHAR)pAddress + lSpecialOffset + sizeof(LONG) + lOffset);
return pCallbackListHead;
}
// 登入檔回撥函數結構體定義
typedef struct _CM_NOTIFY_ENTRY
{
LIST_ENTRY ListEntryHead;
ULONG UnKnown1;
ULONG UnKnown2;
LARGE_INTEGER Cookie;
PVOID Context;
PVOID Function;
}CM_NOTIFY_ENTRY, *PCM_NOTIFY_ENTRY;
VOID UnDriver(PDRIVER_OBJECT Driver)
{
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
{
PVOID pCallbackListHeadAddress = NULL;
RTL_OSVERSIONINFOW osInfo = { 0 };
UCHAR pSpecialData[50] = { 0 };
ULONG ulSpecialDataSize = 0;
LONG lSpecialOffset = 0;
DbgPrint("hello lyshark.com \n");
// 查詢 fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
/*
lyshark.com>
nt!CmUnRegisterCallback+0x6b:
fffff806`3a4271ab 4533c0 xor r8d,r8d
fffff806`3a4271ae 488d542438 lea rdx,[rsp+38h]
fffff806`3a4271b3 488d0d06eac3ff lea rcx,[nt!CallbackListHead (fffff806`3a065bc0)]
fffff806`3a4271ba e855e2e2ff call nt!CmListGetNextElement (fffff806`3a255414)
fffff806`3a4271bf 488bf8 mov rdi,rax
fffff806`3a4271c2 4889442440 mov qword ptr [rsp+40h],rax
fffff806`3a4271c7 4885c0 test rax,rax
fffff806`3a4271ca 0f84c7000000 je nt!CmUnRegisterCallback+0x157 (fffff806`3a427297) Branch
*/
pSpecialData[0] = 0x48;
pSpecialData[1] = 0x8D;
pSpecialData[2] = 0x0D;
ulSpecialDataSize = 3;
// 根據特徵碼獲取地址
pCallbackListHeadAddress = SearchCallbackListHead(pSpecialData, ulSpecialDataSize, lSpecialOffset);
DbgPrint("[LyShark.com] CallbackListHead => %p \n", pCallbackListHeadAddress);
// 遍歷連結串列結構
ULONG i = 0;
PCM_NOTIFY_ENTRY pNotifyEntry = NULL;
if (NULL == pCallbackListHeadAddress)
{
return FALSE;
}
// 開始遍歷雙向連結串列
pNotifyEntry = (PCM_NOTIFY_ENTRY)pCallbackListHeadAddress;
do
{
// 判斷pNotifyEntry地址是否有效
if (FALSE == MmIsAddressValid(pNotifyEntry))
{
break;
}
// 判斷回撥函數地址是否有效
if (MmIsAddressValid(pNotifyEntry->Function))
{
DbgPrint("[LyShark.com] 回撥函數地址: 0x%p | 回撥函數Cookie: 0x%I64X \n", pNotifyEntry->Function, pNotifyEntry->Cookie.QuadPart);
}
// 獲取下一連結串列
pNotifyEntry = (PCM_NOTIFY_ENTRY)pNotifyEntry->ListEntryHead.Flink;
} while (pCallbackListHeadAddress != (PVOID)pNotifyEntry);
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
最終執行這個驅動程式,輸出如下效果:

目前系統中有兩個回撥函數,這一點在第一張圖片中也可以得到,列舉是正確的。
文章作者:lyshark (王瑞)
文章出處:https://www.cnblogs.com/LyShark/p/16813069.html
版權宣告:本部落格文章與程式碼均為學習時整理的筆記,文章 [均為原創] 作品,轉載請 [新增出處] ,您新增出處是我創作的動力!
轉載文章請遵守《中華人民共和國著作權法》相關法律規定或遵守《署名CC BY-ND 4.0國際》規範,合理合規攜帶原創出處轉載,如果不攜帶文章出處,並惡意轉載多篇原創文章被本人發現,本人保留起訴權!
文章出處:https://www.cnblogs.com/LyShark/p/16813069.html
版權宣告:本部落格文章與程式碼均為學習時整理的筆記,文章 [均為原創] 作品,轉載請 [新增出處] ,您新增出處是我創作的動力!
轉載文章請遵守《中華人民共和國著作權法》相關法律規定或遵守《署名CC BY-ND 4.0國際》規範,合理合規攜帶原創出處轉載,如果不攜帶文章出處,並惡意轉載多篇原創文章被本人發現,本人保留起訴權!