分散式儲存系統之Ceph叢集RadosGW基礎使用
前文我們瞭解了MDS擴充套件相關話題,回顧請參考https://www.cnblogs.com/qiuhom-1874/p/16759585.html;今天我們來聊一聊RadosGW的基礎使用相關話題;
物件儲存系統概述
物件儲存系統(Object Storage System,簡稱OSS);物件儲存(Object Storage) 是無層次結構的資料儲存方法,通常用於雲端計算環境中;不同於其他資料儲存方法,基於物件的儲存不使用目錄樹;資料作為單獨的物件進行儲存;資料並不放置在目錄層次結構中,而是存在於平面地址空間內的同一級別;應用通過唯一地址來識別每個單獨的資料物件;每個物件可包含有助於檢索的後設資料;專為使用API在應用級別(而非使用者級別)進行存取而設計;
物件與物件儲存
物件是物件儲存系統中資料儲存的基本單位,每個Object是資料和資料屬性集的綜合體,資料屬性可以根據應用的需求進行設定,包括資料分佈、服務質量等;即每個物件都有單獨後設資料屬性等資訊(物件的大小可以不同,甚至可以包含整個資料結構,如檔案、資料庫表項等);為了簡化儲存系統管理任務,每個物件自我維護其屬性;物件儲存系統一般是一類智慧裝置,它具有自己的儲存媒介、處理器、記憶體以及網路系統等,負責管理原生的物件,是物件儲存系統的核心;如下所示

提示:儲存系統磁碟中儲存的每個物件,它不像傳統檔案系統,統一管理後設資料資訊;每個物件的後設資料資訊和物件屬性等都是物件自身負責管理;物件自身會拿出一部分空間來管理自身的後設資料資訊等資訊;
塊儲存、檔案儲存與物件儲存

提示:塊儲存就是通過scsi協定或rbd協定或儲存區域網路的方式(SAN)將對應儲存陣列中的磁碟裝置虛擬為多個塊裝置,供使用者端或應用程式使用;檔案儲存是將底層儲存系統提供的磁碟裝置抽象為一個檔案系統,然後通過網路的方式向用戶端或應用提供檔案系統介面服務;物件儲存是將底層儲存系統通過虛擬化的形式將底層儲存服務以RUSTful api向用戶端或參照提供儲存介面的方式,通常通過網際網路的形式將對應介面供程式存取資料使用;
物件儲存系統基礎術語
一般說來,一個物件儲存系統的核心資源型別應該包括使用者(User)、儲存桶(bucket)和物件(object);三者的關係是:使用者將物件儲存於物件儲存系統上的儲存桶中,儲存桶隸屬於使用者並能夠容納物件,一個使用者可以擁有一到多個儲存桶,而一個儲存桶常用於儲存多個物件;

提示:RadosGW相容亞馬遜的S3介面和openstack的swift介面,但是s3和swift這兩個介面並不完全相容;所以兩者的設計與設計上有所區別;但大多數物件儲存系統對外呈現的核心資源型別大同小異;
Amazon S3:提供了user、bucket和object分別表示使用者、儲存桶和物件,其中bucket隸屬於user,因此user名稱即可做為bucket的名稱空間,不同使用者允許使用相同名稱的bucket;
OpenStack Swift:提供了user、container和object分別對應於使用者、儲存桶和物件,不過它還額外為user提供了父級元件account,用於表示一個專案或租戶,因此一個account中可包含一到多個user,它們可共用使用同一組container,併為container提供名稱空間;
RadosGW:提供了user、subuser、bucket和object,其中的user對應於S3的user,而subuser則對應於Swift的user,不過user和subuser都不支援為bucket提供名稱空間,因此,不同使用者的儲存桶也不允許同名;不過,自Jewel版本起,RadosGW引入了tenant(租戶)用於為user和bucket提供名稱空間,但它是個可選元件; Jewel版本之前,radosgw的所有user位於同一名稱空間,它要求所有user的ID必須惟一,並且即便是不同user的bucket也不允許使用相同的bucket ID;
認證和授權
使用者賬號是認證(Authentication)、授權(Authorization)及儲存配額(Quota)功能的載體,RGW依賴它對RESTful API進行請求認證、控制資源(儲存桶和物件等)的存取許可權並設定可用儲存空間上限;S3和Swift使用了不同的認證機制; S3主要採用的是基於存取金鑰(access key)和私有金鑰(secret key)進行認證,RGW相容其V2和V4兩種認證機制,其中V2認證機制支援本地認證、LDAP認證和kerberos認證三種方式,所有未能通過認證的使用者統統被視為匿名使用者;Swift結合Swift私有金鑰(swift key)使用令牌(token)認證方式,它支援臨時URL認證、本地認證、OpenStack Keystone認證、第三方認證和匿名認證等方式;
通過身份認證後,RGW針對使用者的每次資源操作請求都會進行授權檢查,僅那些能夠滿足授權定義(ACL)的請求會被允許執行; S3使用bucket acl和object acl分別來控制bucket和object的存取控制許可權,一般用於向bucket或object屬主之外的其它使用者進行授權;Swift API中的許可權控制則分為user存取控制列表和bucket存取控制列表兩種,前一種針對user進行設定,而後一定則專用於bucket及內部的object,且只有read和write兩種許可權;RadosGW為了支援通用的雲端儲存功能,Ceph在RADOS叢集的基礎上提供了RGW(RADOS GateWay)資料抽象和管理層,它是原生相容S3和Swift API的物件儲存服務,支援資料壓縮和多站點(Multi-Site)多活機制,並支援NFS協定存取介面等特性; S3和Swift是RESTful風格的API,它們基於http/https協定完成通訊和資料交換; radosgw的http/https服務由內建的Civeweb提供,它同時也能支援多種主流的Web服務程式以代理的形式接收使用者請求並轉發至ceph-radosgw程序,這些Web服務程式包括nginx和haproxy等;
RGW的功能依賴於Ceph物件閘道器守護行程(ceph-radosgw)實現,它負責向用戶端提供REST API介面,並將資料操作請求轉換為底層RADOS儲存叢集的相關操作;出於冗餘及負載均衡的需要,一個Ceph叢集上的ceph-radosgw守護行程通常不止一個,這些支撐同一物件儲存服務的守護行程聯合起來構成一個zone(區域)用於代表一個獨立的儲存服務和儲存空間; 在容災設計的架構中,管理員會基於兩個或以上的Ceph叢集定義出多個zone,這些zone之間通過同步機制實現冗餘功能,並組成一個新的父級邏輯元件zonegroup;
多站點(Mutli-Sites)
zonegroup負責定義其下的各個zone之間的合作模式(active/passive或active/active)、呼叫的資料儲存策略和同步機制等,並且能夠為一個更大級別的應用通過多個zonegroup完成跨地域的共同作業,實現提升使用者端接入的服務質量等功能,這也通常稱為多站點(Mutli-Sites);為Ceph儲存叢集啟用radosgw服務之後,它會預設生成一個名為default的zonegroup,其內含一個名為default的zone,管理員可按需擴充套件使用更多的zone或zonegroup;更進一步地,zonegroup還有其父級元件realm,用於界定跨地理位置進行復制時的邊界;
設定Citeweb
自0.80版本起,Ceph放棄了基於apache和fastcgi提供radosgw服務的傳統而代之以預設嵌入在ceph-radosgw程序中的Citeweb,這種新的實現方式更加輕便和簡潔,但直到Ceph 11.0.1版本,Citeweb才開始支援SSL協定;Citeweb預設監聽於TCP協定的7480埠提供http服務,修改設定需要編輯ceph.conf組態檔,以如下格式進行定義
[client.rgw.<gateway-node>] rgw_host = <hostname OR ipaddr> rgw_frontends = "civetweb port=80"
範例:設定rgw監聽在ceph-mon01的8080埠
[cephadm@ceph-admin ceph-cluster]$ cat ceph.conf [global] fsid = 7fd4a619-9767-4b46-9cee-78b9dfe88f34 mon_initial_members = ceph-mon01 mon_host = 192.168.0.71 public_network = 192.168.0.0/24 cluster_network = 172.16.30.0/24 auth_cluster_required = cephx auth_service_required = cephx auth_client_required = cephx [mds.ceph-mon03] mds_standby_replay = true mds_standby_for_name = ceph-mon01 [client.rgw.ceph-mon01] rgw_host = ceph-mon01 rgw_frontends = "civetweb port=8080" [cephadm@ceph-admin ceph-cluster]$
推播設定至ceph-mon01
[cephadm@ceph-admin ceph-cluster]$ ceph-deploy --overwrite-conf config push ceph-mon01
[ceph_deploy.conf][DEBUG ] found configuration file at: /home/cephadm/.cephdeploy.conf
[ceph_deploy.cli][INFO ] Invoked (2.0.1): /bin/ceph-deploy --overwrite-conf config push ceph-mon01
[ceph_deploy.cli][INFO ] ceph-deploy options:
[ceph_deploy.cli][INFO ] username : None
[ceph_deploy.cli][INFO ] verbose : False
[ceph_deploy.cli][INFO ] overwrite_conf : True
[ceph_deploy.cli][INFO ] subcommand : push
[ceph_deploy.cli][INFO ] quiet : False
[ceph_deploy.cli][INFO ] cd_conf : <ceph_deploy.conf.cephdeploy.Conf instance at 0x7f327dce58c0>
[ceph_deploy.cli][INFO ] cluster : ceph
[ceph_deploy.cli][INFO ] client : ['ceph-mon01']
[ceph_deploy.cli][INFO ] func : <function config at 0x7f327df14cf8>
[ceph_deploy.cli][INFO ] ceph_conf : None
[ceph_deploy.cli][INFO ] default_release : False
[ceph_deploy.config][DEBUG ] Pushing config to ceph-mon01
[ceph-mon01][DEBUG ] connection detected need for sudo
[ceph-mon01][DEBUG ] connected to host: ceph-mon01
[ceph-mon01][DEBUG ] detect platform information from remote host
[ceph-mon01][DEBUG ] detect machine type
[ceph-mon01][DEBUG ] write cluster configuration to /etc/ceph/{cluster}.conf
[cephadm@ceph-admin ceph-cluster]$
重啟ceph-radosgw@rgw程序生效新設定
[cephadm@ceph-admin ceph-cluster]$ ssh ceph-mon01 'sudo systemctl restart ceph-radosgw@rgw' [cephadm@ceph-admin ceph-cluster]$ ssh ceph-mon01 'sudo ss -tnl|grep 8080' LISTEN 0 128 *:8080 *:* [cephadm@ceph-admin ceph-cluster]$
測試:ceph-mon01的8080是否可存取?
[cephadm@ceph-admin ceph-cluster]$ curl ceph-mon01:8080 <?xml version="1.0" encoding="UTF-8"?><ListAllMyBucketsResult xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><Owner><ID>anonymous</ID><DisplayName></DisplayName></Owner><Buckets></Buckets></ListAllMyBucketsResult>[cephadm@ceph-admin ceph-cluster]$
設定rgw以https的方式提供服務
1、準備證書
生成key
[root@ceph-mon01 ~]# mkdir /etc/ceph/ssl [root@ceph-mon01 ~]# cd /etc/ceph/ssl [root@ceph-mon01 ssl]# openssl genrsa -out /etc/ceph/ssl/ceph.test.key Generating RSA private key, 2048 bit long modulus ............+++ ................................+++ e is 65537 (0x10001) [root@ceph-mon01 ssl]# cat /etc/ceph/ssl/ceph.test.key -----BEGIN RSA PRIVATE KEY----- MIIEogIBAAKCAQEAth2CA5M9psyG7Nmq4pWK8CMfgQpCfaQdKHU6qyQKq4/TflnB khrWlz2sANEUQpLkzhjAeto7PU+ykgpMN3J8a3TZu3SIsKC/MBB1yDHx6raU33R0 I6hbdtumjvP4XVWDcY0Zod4zkRH/iCkQKMw2RhjVEaKT+0KnHAle5RxLojcrqIz9 iibmUqdH35T8aM8EIAwRcJx0QBYDlQJmqdhuHGt41ujqSpWcZEoGfsODxYuisZlk wOgTzTlfMcjOesPoSSqJ2X8zXzdbcMI6kEJb/xPa8ByTVOR8OAQJILezg2T5T6rM o3J9WVcGmDwqSczpzcyirRk+OavfawL3JJHsAQIDAQABAoIBAEphbOum5KROnsD3 +gqHR3Li9YgPt653LA2NK8QgeVcu7BOL9zqESacF4k2HF35FXrwqcdr7bPySo31w RUbUNKry08bzRqzVSqEH6AM3GvZhUhaeCp1RsuGtvq5eSM9eEMx8874f8fHLZxGm q9nt5jDlDYkhXM1foL8buK1czCtZKqekhtFF9k5xis1d+QPeA0Pp/u94L0srzemh JDBcu52lw1kipnYWTn2jvfPoh0Ob/Bwm53Pl8ZhweD3peyxGpRZd41gY6LRzbFGG 6QqG5syXzNeE9p5ozJjA3w0En1XwPOGnOcrrjCvY/Jk1mYkd9ERBpFDaPMIM52Ar bIE84kECgYEA4bbxi0We62rwGOFJvPQ54O5hMEhxaYNxqcEDhwEBFUAU9f7Y6FFT k36obztXFjwhte3H9raIPuZjHpkZ+UZG4R1eESbWX1C3UvfFHHQFHqaS8l+sG1xh jVbyhif9wJwx8Wu4gAsdzmGXYQ1NzNXkucLX9Tn6xoAM6X7qbaBDkYkCgYEAzoz5 EGkdmoPeYlV2aBgsvrcVQH8CHDdsg+8vgigq7WBsRO/lZPHRwdsjI60QJJ6RJkqJ Y01Rk5hOYSEqAckE8FKSS9ynFHxomAncvO0ZRpvH2aQr+Ecr5oi4mzyOt1LRVgxw guEGDBku0vXYaJQTXZM3FaeLLQ5aDrE9pg8fwLkCgYBOEgUB8xbAvsBFGsdyf9b1 If6jwKrZoAlUedpKe+JwAzY8z+UeleKehZSkxJWerzXJw3ECuKfveaiXEMWXHuOt QYcjz5ceaMDABcs7yDVtIJh7FPRmklF7nbNNC9ANKvlrU6MBRtcMZ10AyKU8UE9I oUgpHeDLf8b3jFpxiJlWYQKBgBhC8tZ8ol+N8cc3Jqtfe5IDS1nCEWtjDzoIFFqD gVdUpiMK0rUiunK83MnKAEVs4rvOsYiagmSF1V8PWDHRfOUFre1/Q5jibB6/uc/v QbLLhZQI9qk5Iuz3Tkfdux3JepFS8LxO1jkBlEBvZDYUfpnVOvkuLujh8K4dH5Kr 4BzxAoGAKVyF4cBthBBZ0d7hKLGjBLr0mNLPmroGbYnzLfqwz2OZiudvIrA1EDFP sQwJGHgkYd9tWhIvrp1orfOtRxocFYCUyBDba5yZjTplSKbYQ+muBHCmNsurc/KM UreFCZGVU/oEG0ebGVbavG8lAVKs17+tr/Ct2UpsgO99+XxeP5Y= -----END RSA PRIVATE KEY----- [root@ceph-mon01 ssl]#
自簽證書籤署
[root@ceph-mon01 ssl]# openssl req -new -x509 -key /etc/ceph/ssl/ceph.test.key -out /etc/ceph/ssl/ceph.test.pem -days 365 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:SICHUAN Locality Name (eg, city) [Default City]:GY Organization Name (eg, company) [Default Company Ltd]:TEST Organizational Unit Name (eg, section) []:TEST Common Name (eg, your name or your server's hostname) []:ceph-mon01.ilinux.io Email Address []: [root@ceph-mon01 ssl]# ls ceph.test.key ceph.test.pem [root@ceph-mon01 ssl]#
合併key和自簽名證書到一個檔案
[root@ceph-mon01 ssl]# cat ceph.test.key ceph.test.pem > ceph.test.crt [root@ceph-mon01 ssl]# cat ceph.test.crt -----BEGIN RSA PRIVATE KEY----- MIIEogIBAAKCAQEAth2CA5M9psyG7Nmq4pWK8CMfgQpCfaQdKHU6qyQKq4/TflnB khrWlz2sANEUQpLkzhjAeto7PU+ykgpMN3J8a3TZu3SIsKC/MBB1yDHx6raU33R0 I6hbdtumjvP4XVWDcY0Zod4zkRH/iCkQKMw2RhjVEaKT+0KnHAle5RxLojcrqIz9 iibmUqdH35T8aM8EIAwRcJx0QBYDlQJmqdhuHGt41ujqSpWcZEoGfsODxYuisZlk wOgTzTlfMcjOesPoSSqJ2X8zXzdbcMI6kEJb/xPa8ByTVOR8OAQJILezg2T5T6rM o3J9WVcGmDwqSczpzcyirRk+OavfawL3JJHsAQIDAQABAoIBAEphbOum5KROnsD3 +gqHR3Li9YgPt653LA2NK8QgeVcu7BOL9zqESacF4k2HF35FXrwqcdr7bPySo31w RUbUNKry08bzRqzVSqEH6AM3GvZhUhaeCp1RsuGtvq5eSM9eEMx8874f8fHLZxGm q9nt5jDlDYkhXM1foL8buK1czCtZKqekhtFF9k5xis1d+QPeA0Pp/u94L0srzemh JDBcu52lw1kipnYWTn2jvfPoh0Ob/Bwm53Pl8ZhweD3peyxGpRZd41gY6LRzbFGG 6QqG5syXzNeE9p5ozJjA3w0En1XwPOGnOcrrjCvY/Jk1mYkd9ERBpFDaPMIM52Ar bIE84kECgYEA4bbxi0We62rwGOFJvPQ54O5hMEhxaYNxqcEDhwEBFUAU9f7Y6FFT k36obztXFjwhte3H9raIPuZjHpkZ+UZG4R1eESbWX1C3UvfFHHQFHqaS8l+sG1xh jVbyhif9wJwx8Wu4gAsdzmGXYQ1NzNXkucLX9Tn6xoAM6X7qbaBDkYkCgYEAzoz5 EGkdmoPeYlV2aBgsvrcVQH8CHDdsg+8vgigq7WBsRO/lZPHRwdsjI60QJJ6RJkqJ Y01Rk5hOYSEqAckE8FKSS9ynFHxomAncvO0ZRpvH2aQr+Ecr5oi4mzyOt1LRVgxw guEGDBku0vXYaJQTXZM3FaeLLQ5aDrE9pg8fwLkCgYBOEgUB8xbAvsBFGsdyf9b1 If6jwKrZoAlUedpKe+JwAzY8z+UeleKehZSkxJWerzXJw3ECuKfveaiXEMWXHuOt QYcjz5ceaMDABcs7yDVtIJh7FPRmklF7nbNNC9ANKvlrU6MBRtcMZ10AyKU8UE9I oUgpHeDLf8b3jFpxiJlWYQKBgBhC8tZ8ol+N8cc3Jqtfe5IDS1nCEWtjDzoIFFqD gVdUpiMK0rUiunK83MnKAEVs4rvOsYiagmSF1V8PWDHRfOUFre1/Q5jibB6/uc/v QbLLhZQI9qk5Iuz3Tkfdux3JepFS8LxO1jkBlEBvZDYUfpnVOvkuLujh8K4dH5Kr 4BzxAoGAKVyF4cBthBBZ0d7hKLGjBLr0mNLPmroGbYnzLfqwz2OZiudvIrA1EDFP sQwJGHgkYd9tWhIvrp1orfOtRxocFYCUyBDba5yZjTplSKbYQ+muBHCmNsurc/KM UreFCZGVU/oEG0ebGVbavG8lAVKs17+tr/Ct2UpsgO99+XxeP5Y= -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIDpTCCAo2gAwIBAgIJAKiSRxIiMIwAMA0GCSqGSIb3DQEBCwUAMGkxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdTSUNIVUFOMQswCQYDVQQHDAJHWTENMAsGA1UECgwE VEVTVDENMAsGA1UECwwEVEVTVDEdMBsGA1UEAwwUY2VwaC1tb24wMS5pbGludXgu aW8wHhcNMjIxMDA4MDcyMzI1WhcNMjMxMDA4MDcyMzI1WjBpMQswCQYDVQQGEwJD TjEQMA4GA1UECAwHU0lDSFVBTjELMAkGA1UEBwwCR1kxDTALBgNVBAoMBFRFU1Qx DTALBgNVBAsMBFRFU1QxHTAbBgNVBAMMFGNlcGgtbW9uMDEuaWxpbnV4LmlvMIIB IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAth2CA5M9psyG7Nmq4pWK8CMf gQpCfaQdKHU6qyQKq4/TflnBkhrWlz2sANEUQpLkzhjAeto7PU+ykgpMN3J8a3TZ u3SIsKC/MBB1yDHx6raU33R0I6hbdtumjvP4XVWDcY0Zod4zkRH/iCkQKMw2RhjV EaKT+0KnHAle5RxLojcrqIz9iibmUqdH35T8aM8EIAwRcJx0QBYDlQJmqdhuHGt4 1ujqSpWcZEoGfsODxYuisZlkwOgTzTlfMcjOesPoSSqJ2X8zXzdbcMI6kEJb/xPa 8ByTVOR8OAQJILezg2T5T6rMo3J9WVcGmDwqSczpzcyirRk+OavfawL3JJHsAQID AQABo1AwTjAdBgNVHQ4EFgQUeeRFLKn76P9N7GzquqLSjfC1gwswHwYDVR0jBBgw FoAUeeRFLKn76P9N7GzquqLSjfC1gwswDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0B AQsFAAOCAQEAqHQ8hCz5bYmXqtJW6Uk1h0T8nHirrkUovLIp0xB6GhK9wsLh8bZz e7FXQfgMCmTFIzOmsBJZGLuoqwfWwNtBuy7XfTRJBh1yWY3lvf3Bmd/5W+6tpZlG CfVyj1q6gOE1W2yZC0JAK+BRQyHTvG3dDosOZnIxw111IHkLWxJruz+Z8L7+FGCy e+As6hUPNB/yrrmjTTCJDkqUSY6Haw1prLZqVlA3JinnQqFSNbc92/cX1frUkHsg wp2d5KCCQ6WSRxbXUfi1ZPEDfHftg6Xzfac+FRXu46ht8PfcDh4XNT0uDZYjtXrN RSOcnEiftc2pxDxLEo6Ilt3Zb53sdYtq4A== -----END CERTIFICATE----- [root@ceph-mon01 ssl]#
設定ceph-mon01以https提供服務

提示:我們需要在rgw_frontends裡新增port=埠s,然後用ssl_certificate來指定證書即可
驗證:重啟服務,看看對應8443是否監聽?
[root@ceph-mon01 ssl]# systemctl restart ceph-radosgw@rgw [root@ceph-mon01 ssl]# ss -tnl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 172.16.30.71:6800 *:* LISTEN 0 128 192.168.0.71:6800 *:* LISTEN 0 128 172.16.30.71:6801 *:* LISTEN 0 128 192.168.0.71:6801 *:* LISTEN 0 128 172.16.30.71:6802 *:* LISTEN 0 128 192.168.0.71:6802 *:* LISTEN 0 128 172.16.30.71:6803 *:* LISTEN 0 128 192.168.0.71:6803 *:* LISTEN 0 128 192.168.0.71:6804 *:* LISTEN 0 128 *:22 *:* LISTEN 0 100 127.0.0.1:25 *:* LISTEN 0 128 *:8443 *:* LISTEN 0 128 192.168.0.71:6789 *:* LISTEN 0 128 [::]:22 [::]:* LISTEN 0 100 [::1]:25 [::]:* [root@ceph-mon01 ssl]#
提示:可以看到重啟服務以後對應8443埠處於正常監聽;
驗證:用使用者端瀏覽器存取ceph-mon01的8443埠,看看是否能存取?
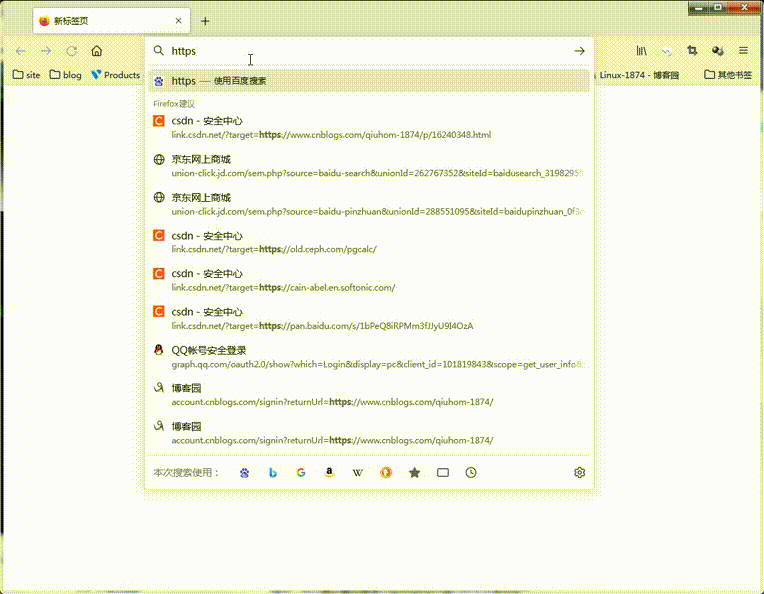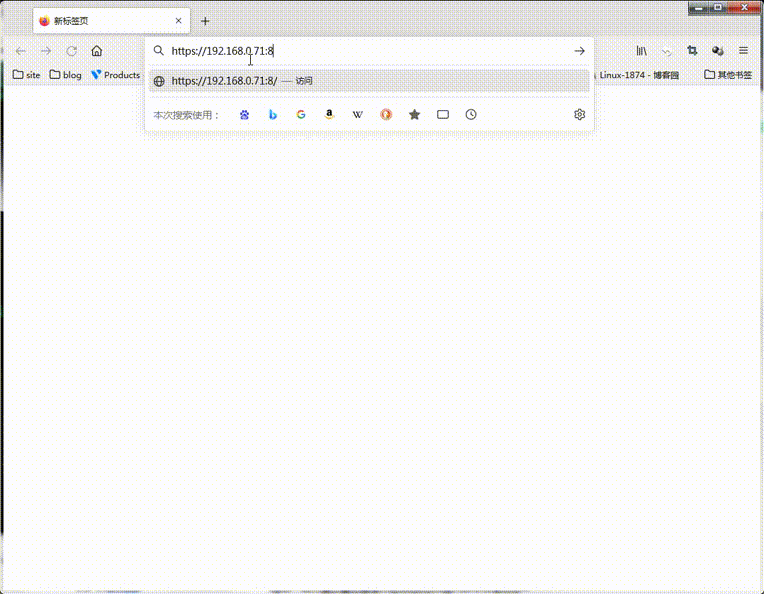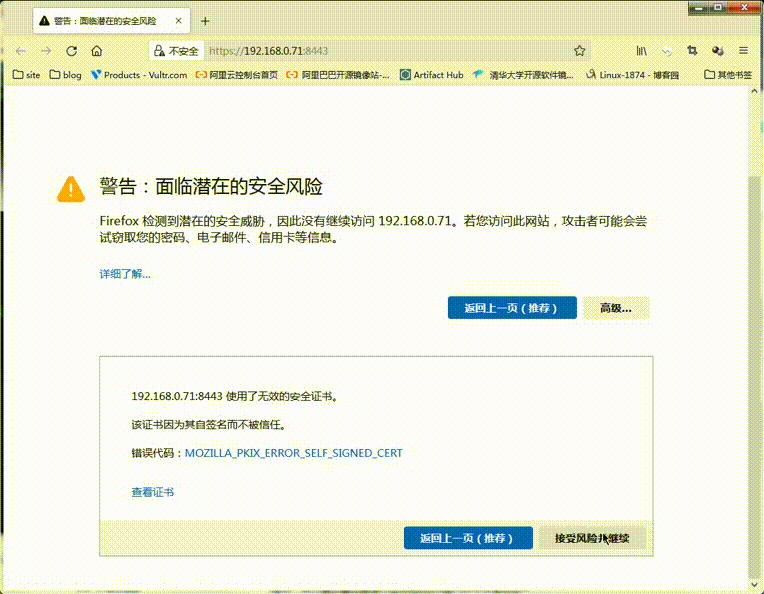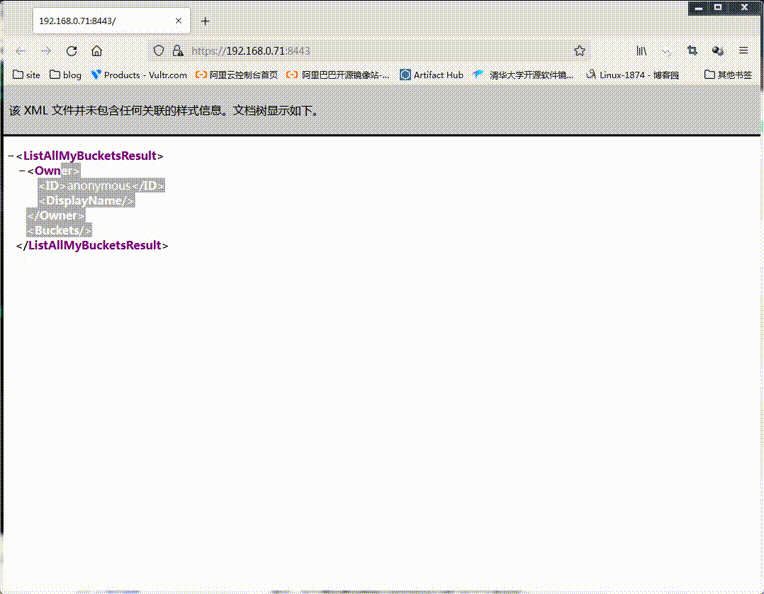
提示:可以看到用瀏覽器存取ceph-mon01的8443埠,會有一個證書安全提示;對應介面也是可以正常存取的;
設定rgw以http和https提供服務

提示:我們只需要在port後面寫上對應http監聽埠+https監聽埠s即可監聽對應協定的埠;
驗證:重啟服務,看看對應7480和8443是否正常處於監聽狀態?
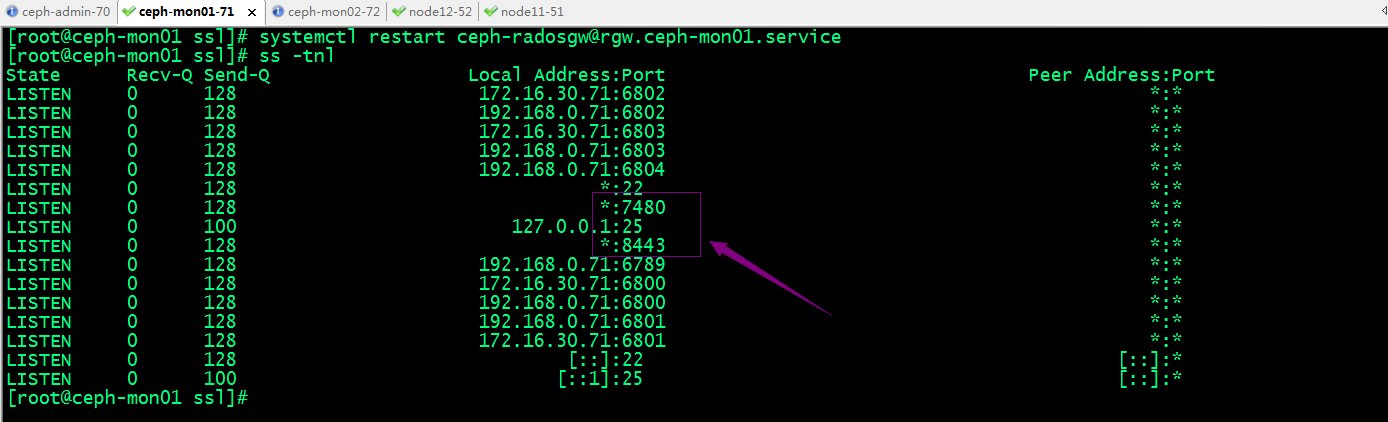
提示:可以看到7480和8443都處於監聽狀態;
其它設定引數
num_threads:Citeweb以執行緒模型處理使用者端請求,它為每個連線請求分配一個專用執行緒,因而此引數定義了其支援的最大並行連線數,預設值為50;
request_timeout_ms:網路傳送與接收操作的超時時長,以ms為單位,預設值為30000;可以在必要時通過增大此值實現長連線的效果;
access_log_file:存取紀錄檔的檔案路徑,預設為空;
error_log_file:錯誤紀錄檔的檔案路徑,預設為空;
設定泛域名解析
S3的儲存桶是用於儲存物件的容器,每個物件都必須儲存在一個特定的儲存桶中,且每個物件都要直接通過RESTful API基於URL進行存取,URL格式為http(s)://bucket-name.radowgw-host[:port]/key;例如,對於儲存在rgw01.ilinux.io上的S3 API物件儲存系統上eshop儲存桶中的名為images/commodity1.jpg 的物件,可通過http://eshop.rgw01.ilinux.io/images/commodity1.jpg對其進行定址;因此,radosgw的S3 API介面的功能強依賴於DNS的泛域名解析服務,它必須能夠正常解析任何「<bucket-name>.<radowgw-host>」格式的名稱至radosgw主機;
部署內網dns伺服器
安裝bind
[root@node12 ~]# yum install bind -y
bind基礎設定
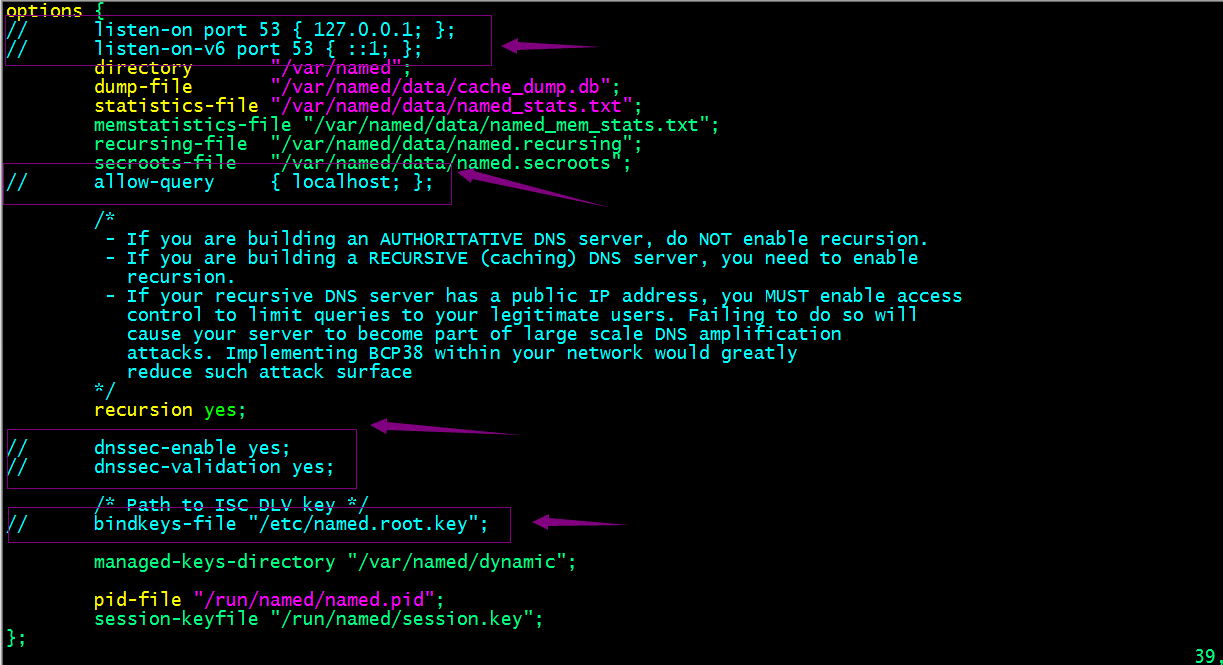
提示:在/etc/named.conf中我們把上面標識的地方給註釋掉即可;
設定解析泛域名的解析檔案
[root@node12 named]# tail /etc/named.rfc1912.zones
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "ilinux.io" IN {
type master;
file "ilinux.io.zone";
};
[root@node12 named]#
檢查組態檔
[root@node12 ~]# named-checkconf [root@node12 ~]#
提示:如果沒有任何提示,說明我們的組態檔沒有問題;
區域組態檔
[root@node12 named]# cat /var/named/ilinux.io.zone
$TTL 1D
@ IN SOA ns.ilinux.io. admin.ilinux.io. ( 0 1D 1H 1W 3H );
IN NS ns
ns IN A 192.168.0.52
ceph-mon01 IN A 192.168.0.71
ceph-mon02 IN A 192.168.0.72
*.ceph-mon01 IN CNAME ceph-mon01
*.ceph-mon02 IN CNAME ceph-mon02
[root@node12 named]#
檢查區域檔案許可權問題
[root@node12 named]# ll /var/named/ total 20 drwxrwx--- 2 named named 23 Oct 8 17:03 data drwxrwx--- 2 named named 60 Oct 8 17:04 dynamic -rw-r--r-- 1 root root 225 Oct 8 16:52 ilinux.io.zone -rw-r----- 1 root named 2253 Apr 5 2018 named.ca -rw-r----- 1 root named 152 Dec 15 2009 named.empty -rw-r----- 1 root named 152 Jun 21 2007 named.localhost -rw-r----- 1 root named 168 Dec 15 2009 named.loopback drwxrwx--- 2 named named 6 Oct 4 15:06 slaves [root@node12 named]# chown :named /var/named/ilinux.io.zone [root@node12 named]# ll /var/named/ total 20 drwxrwx--- 2 named named 23 Oct 8 17:03 data drwxrwx--- 2 named named 60 Oct 8 17:04 dynamic -rw-r--r-- 1 root named 225 Oct 8 16:52 ilinux.io.zone -rw-r----- 1 root named 2253 Apr 5 2018 named.ca -rw-r----- 1 root named 152 Dec 15 2009 named.empty -rw-r----- 1 root named 152 Jun 21 2007 named.localhost -rw-r----- 1 root named 168 Dec 15 2009 named.loopback drwxrwx--- 2 named named 6 Oct 4 15:06 slaves [root@node12 named]#
提示:我們剛才建立的區域檔案是root宿主,root屬組,需要修改為root宿主,named屬組;
檢查區域檔案格式是否錯誤?
[root@node12 named]# named-checkzone ilinux.io /var/named/ilinux.io.zone zone ilinux.io/IN: loaded serial 0 OK [root@node12 named]#
提示:顯示ok,表示區域組態檔沒有問題;
啟動named程序,看看對應解析是否可域名是否可解析?
[root@node12 named]# systemctl start named [root@node12 named]# ss -tnul Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port udp UNCONN 0 0 192.168.0.52:53 *:* udp UNCONN 0 0 127.0.0.1:53 *:* udp UNCONN 0 0 127.0.0.1:323 *:* udp UNCONN 0 0 ::1:323 :::* tcp LISTEN 0 10 192.168.0.52:53 *:* tcp LISTEN 0 10 127.0.0.1:53 *:* tcp LISTEN 0 128 *:22 *:* tcp LISTEN 0 128 127.0.0.1:953 *:* tcp LISTEN 0 100 127.0.0.1:25 *:* tcp LISTEN 0 128 *:16379 *:* tcp LISTEN 0 128 *:27017 *:* tcp LISTEN 0 50 *:3306 *:* tcp LISTEN 0 128 :::22 :::* tcp LISTEN 0 128 ::1:953 :::* tcp LISTEN 0 100 ::1:25 :::* [root@node12 named]#
提示:可以看到udp53號埠已經正常啟動;
設定使用者端主機,將對應dns指向192.168.0.52,看看對應域名是否可解析?
[root@node11 ~]# cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.0.52 [root@node11 ~]#
使用dig命令解析ceph-mon01.ilinux.io看看是否能正常解析?
[root@node11 ~]# dig ceph-mon01.ilinux.io ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.10 <<>> ceph-mon01.ilinux.io ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56820 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;ceph-mon01.ilinux.io. IN A ;; ANSWER SECTION: ceph-mon01.ilinux.io. 86400 IN A 192.168.0.71 ;; AUTHORITY SECTION: ilinux.io. 86400 IN NS ns.ilinux.io. ;; ADDITIONAL SECTION: ns.ilinux.io. 86400 IN A 192.168.0.52 ;; Query time: 1 msec ;; SERVER: 192.168.0.52#53(192.168.0.52) ;; WHEN: Sat Oct 08 17:26:18 CST 2022 ;; MSG SIZE rcvd: 98 [root@node11 ~]# dig ceph-mon02.ilinux.io ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.10 <<>> ceph-mon02.ilinux.io ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50240 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;ceph-mon02.ilinux.io. IN A ;; ANSWER SECTION: ceph-mon02.ilinux.io. 86400 IN A 192.168.0.72 ;; AUTHORITY SECTION: ilinux.io. 86400 IN NS ns.ilinux.io. ;; ADDITIONAL SECTION: ns.ilinux.io. 86400 IN A 192.168.0.52 ;; Query time: 1 msec ;; SERVER: 192.168.0.52#53(192.168.0.52) ;; WHEN: Sat Oct 08 17:26:28 CST 2022 ;; MSG SIZE rcvd: 98 [root@node11 ~]# dig file.ceph-mon02.ilinux.io ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.10 <<>> file.ceph-mon02.ilinux.io ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37815 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;file.ceph-mon02.ilinux.io. IN A ;; ANSWER SECTION: file.ceph-mon02.ilinux.io. 86400 IN CNAME ceph-mon02.ilinux.io. ceph-mon02.ilinux.io. 86400 IN A 192.168.0.72 ;; AUTHORITY SECTION: ilinux.io. 86400 IN NS ns.ilinux.io. ;; ADDITIONAL SECTION: ns.ilinux.io. 86400 IN A 192.168.0.52 ;; Query time: 1 msec ;; SERVER: 192.168.0.52#53(192.168.0.52) ;; WHEN: Sat Oct 08 17:26:38 CST 2022 ;; MSG SIZE rcvd: 117 [root@node11 ~]#
提示:可以看到在使用者端主機上將對應dns指向192.168.0.52以後,對應使用dig命令是可以正常解析ceph-mon01.ilinux.io;泛域名解析也是沒有問題,到此我們的dns服務就搭建完成了;
設定每個radowgw守護行程的rgw_dns_name為其DNS名稱

提示:我這裡將ceph-mon02也啟動了Radosgw,所以連同ceph-mon2一遍設定了;我們可以使用ceph-deploy將設定推播給叢集各主機,然後再到每個主機上重啟程序就好;
測試使用S3 API介面
使用radosgw-admin工具建立使用者
[root@ceph-mon01 ssl]# radosgw-admin user create --uid=s3user --display-name="s3 test user"
{
"user_id": "s3user",
"display_name": "s3 test user",
"email": "",
"suspended": 0,
"max_buckets": 1000,
"auid": 0,
"subusers": [],
"keys": [
{
"user": "s3user",
"access_key": "433ZGVH2EJTJMG5EDP1B",
"secret_key": "K0V73EieP8Wh6mng9xu9jA6iDbJGzfTXi2q3XQOU"
}
],
"swift_keys": [],
"caps": [],
"op_mask": "read, write, delete",
"default_placement": "",
"placement_tags": [],
"bucket_quota": {
"enabled": false,
"check_on_raw": false,
"max_size": -1,
"max_size_kb": 0,
"max_objects": -1
},
"user_quota": {
"enabled": false,
"check_on_raw": false,
"max_size": -1,
"max_size_kb": 0,
"max_objects": -1
},
"temp_url_keys": [],
"type": "rgw",
"mfa_ids": []
}
[root@ceph-mon01 ssl]# radosgw-admin user list
[
"s3user"
]
[root@ceph-mon01 ssl]#
提示:建立賬號在叢集節點都可以建立,建議在admin host上建立;
在使用者端主機上安裝s3cmd工具
[root@node11 ~]# yum install -y s3cmd
提示:該工具來自epel源,安裝前請設定好epel源;
設定s3cmd工具
[root@node11 ~]# s3cmd --configure Enter new values or accept defaults in brackets with Enter. Refer to user manual for detailed description of all options. Access key and Secret key are your identifiers for Amazon S3. Leave them empty for using the env variables. Access Key: 433ZGVH2EJTJMG5EDP1B Secret Key: K0V73EieP8Wh6mng9xu9jA6iDbJGzfTXi2q3XQOU Default Region [US]: Use "s3.amazonaws.com" for S3 Endpoint and not modify it to the target Amazon S3. S3 Endpoint [s3.amazonaws.com]: ceph-mon01.ilinux.io:7480 Use "%(bucket)s.s3.amazonaws.com" to the target Amazon S3. "%(bucket)s" and "%(location)s" vars can be used if the target S3 system supports dns based buckets. DNS-style bucket+hostname:port template for accessing a bucket [%(bucket)s.s3.amazonaws.com]: [%(bucket)s.ceph-mon01.ilinux.io:7480 Encryption password is used to protect your files from reading by unauthorized persons while in transfer to S3 Encryption password: Path to GPG program [/usr/bin/gpg]: When using secure HTTPS protocol all communication with Amazon S3 servers is protected from 3rd party eavesdropping. This method is slower than plain HTTP, and can only be proxied with Python 2.7 or newer Use HTTPS protocol [Yes]: No On some networks all internet access must go through a HTTP proxy. Try setting it here if you can't connect to S3 directly HTTP Proxy server name: New settings: Access Key: 433ZGVH2EJTJMG5EDP1B Secret Key: K0V73EieP8Wh6mng9xu9jA6iDbJGzfTXi2q3XQOU Default Region: US S3 Endpoint: ceph-mon01.ilinux.io:7480 DNS-style bucket+hostname:port template for accessing a bucket: [%(bucket)s.ceph-mon01.ilinux.io:7480 Encryption password: Path to GPG program: /usr/bin/gpg Use HTTPS protocol: False HTTP Proxy server name: HTTP Proxy server port: 0 Test access with supplied credentials? [Y/n] Y Please wait, attempting to list all buckets... Success. Your access key and secret key worked fine :-) Now verifying that encryption works... Not configured. Never mind. Save settings? [y/N] y Configuration saved to '/root/.s3cfg' [root@node11 ~]#
提示:access key和secret key這兩項在我們建立使用者時,就會返回;把對應資訊複製過來就好;s3 endport是用來指定rgw站點的域名和埠;dns-style是指定泛域名解析格式;上述設定資訊儲存在當前使用者的.s3cfg檔案中,我們也可以直接修改該檔案來設定s3cmd工具;
用s3user建立bucket
[root@node11 ~]# s3cmd mb s3://images Bucket 's3://images/' created [root@node11 ~]#
列出bucket
[root@node11 ~]# s3cmd ls 2022-10-08 11:18 s3://images [root@node11 ~]#
上傳檔案
[root@node11 ~]# s3cmd put /usr/share/backgrounds/morning.jpg s3://images/test/test.jpg
upload: '/usr/share/backgrounds/morning.jpg' -> 's3://images/test/test.jpg' [1 of 1]
980265 of 980265 100% in 1s 491.31 KB/s done
[root@node11 ~]# s3cmd ls
2022-10-08 11:18 s3://images
[root@node11 ~]# s3cmd ls s3://images
DIR s3://images/test/
[root@node11 ~]# s3cmd ls s3://images/test/
2022-10-08 11:25 980265 s3://images/test/test.jpg
[root@node11 ~]#
下載檔案
[root@node11 ~]# ls alldatabase index.html oplog_rs [root@node11 ~]# s3cmd get s3://images/test/test.jpg download: 's3://images/test/test.jpg' -> './test.jpg' [1 of 1] 980265 of 980265 100% in 0s 67.25 MB/s done [root@node11 ~]# ls alldatabase index.html oplog_rs test.jpg [root@node11 ~]#
ok,基於s3cmd測試使用S3 API介面就到此結束了;更多radosgw的設定使用,請參考官方檔案;