BinaryBombs(二進位制炸彈實驗)
實驗介紹
- 使用所學知識拆除Binary Bombs來增強對程式的機器級表示、組合語言、偵錯程式和逆向工程等理解。
- Binary Bombs(二進位制炸彈)是一個可執行程式,是C語言編譯連結成的,包含phase1~phase6共6個階段(還有隱藏階段)。
- 各階段要求輸入一個答案,若正確,該階段炸彈被拆除,否則爆炸。
- 你需要拆除儘可能多的炸彈
- 實驗提供一個bomb.c和bomb可執行檔案,但是,bomb.c中只有主函數,和一些彩蛋。
- bomb有一個命令列引數,為讀入的檔案。所以你可以將答案寫入到一個txt檔案,每個答案一行。
實驗技巧
gdb偵錯
(gdb)info reg檢視所有暫存器的資訊(gdb)info frame檢視棧的資訊(gdb)b * 0x405040在0x405040處設定斷點(gdb)b phase_1在函數phase_1處設定斷點(gdb)x/2s 0x405010輸出0x405010開始的兩個字串(gdb)stepi執行一條指令(gdb)nexti類似於stepi,但以函數呼叫為單位(gdb)c繼續(遇到斷點後)(gdb)run ans.txt命令列引數執行(gdb)q退出(gdb)finish執行到當前函數返回(gdb)delete刪除所有斷點(gdb)delete 5刪除斷點 5(gdb)layout asm展示當前的組合語言(非常的好用,ctrl + L 重新整理)(gdb)p *(int *) 0x405012輸出位於地址0x405012的整數(gdb)p $rax輸出%rax的值(gdb)p /x $rax以十六進位制輸出%rax的值(gdb)p *(int *)($rbp + 0x8)輸出地址%rbp + 0x8的整數(gdb)disas phase_1反組合phase_1函數
我的實驗經驗
- 先反組合
objdump -d bomb > asm.txt。然後把asm.txt的內容複製貼上到word。用word來看組合語言,方便塗色標註 - 一邊分析組合語言,一邊利用gdb偵錯。
- 先熟讀CSAPP第三章,最好把習題做完
phase_1
密碼如下:I am not part of the problem. I am a Republican.
破解過程:

-
在phase_1函數處設定斷點。
-
隨便輸出一個答案,如 abcdef。
-
觀察斷點資訊,input_strings可知,答案確實是一個字串。
-
反組合觀察到 strings_not_equal,推測是在判斷字串是否相等。然後,test命令測試返回值,如果非0,則爆炸。
-
0為真,1為假,那麼非0對於strings_not_equal,應該是字串不等,所以現在要找到那個與輸出的字串匹配的字串。
-
觀察到,傳遞給暫存器%esi的值0x403150
-
列印此處的字串:
x/2s 0x403150 -
得到答案
組合程式碼:
點選檢視程式碼
00000000004013f9 <phase_1>:
4013f9: 55 push %rbp
4013fa: 48 89 e5 mov %rsp,%rbp
4013fd: be 50 31 40 00 mov $0x403150,%esi
401402: e8 3d 04 00 00 callq 401844 <strings_not_equal>
401407: 85 c0 test %eax,%eax
401409: 75 02 jne 40140d <phase_1+0x14>
40140b: 5d pop %rbp
40140c: c3 retq
40140d: e8 2e 05 00 00 callq 401940 <explode_bomb>
401412: eb f7 jmp 40140b <phase_1+0x12>****
phase_2
密碼如下:0 1 3 6 10 15
破解過程:
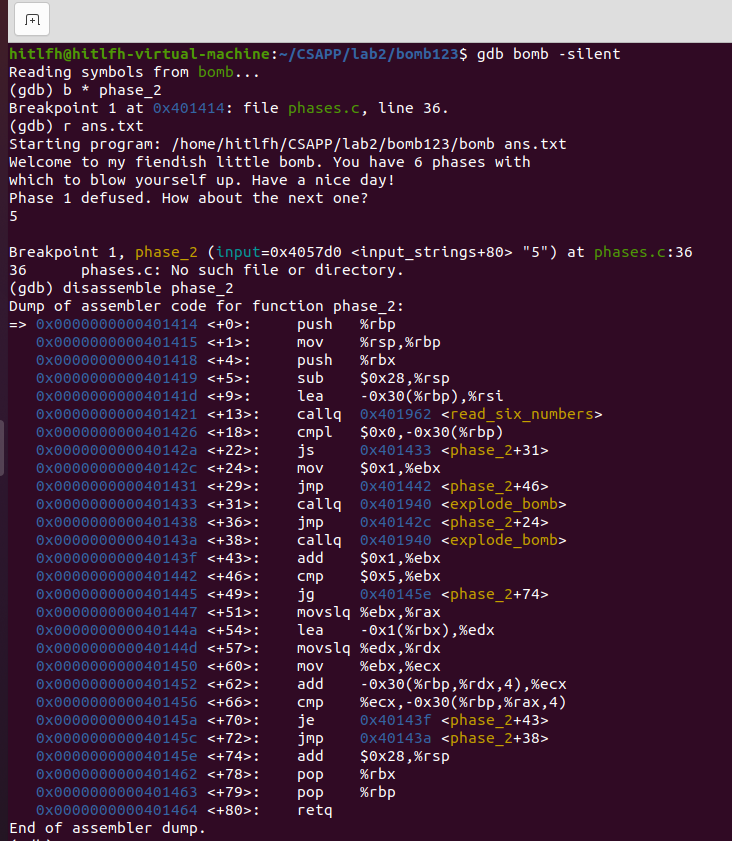
-
在phase_2設定斷點。
-
執行,引數為ans.txt,其中寫有剛剛得到的第一個的答案。
-
先隨便輸入,這裡輸入一個數 5。
-
反組合觀察,一開始呼叫了<read_six_numbers>函數,那麼可以先把輸入改為6個數
-
繼續觀察下面的組合語言,發現 -30(%rbp)不就是存放第一個數的位置嗎?這裡判斷第一個數必須為0,否則炸彈爆炸
-
在後面,%ebx先賦值為1,然後判斷是否大於5,是一個迴圈,然後根據輸入的6個數,每輪列印發現規律。
-
得出程式碼:
for(int i = 1; i <= 5; i ++) a[i] = a[i - 1] + i;。 -
則得出答案。
組合程式碼:
點選檢視程式碼
0000000000401414 <phase_2>:
401414: 55 push %rbp
401415: 48 89 e5 mov %rsp,%rbp
401418: 53 push %rbx
401419: 48 83 ec 28 sub $0x28,%rsp
40141d: 48 8d 75 d0 lea -0x30(%rbp),%rsi
401421: e8 3c 05 00 00 callq 401962 <read_six_numbers>
401426: 83 7d d0 00 cmpl $0x0,-0x30(%rbp)
40142a: 78 07 js 401433 <phase_2+0x1f>
40142c: bb 01 00 00 00 mov $0x1,%ebx
401431: eb 0f jmp 401442 <phase_2+0x2e>
401433: e8 08 05 00 00 callq 401940 <explode_bomb>
401438: eb f2 jmp 40142c <phase_2+0x18>
40143a: e8 01 05 00 00 callq 401940 <explode_bomb>
40143f: 83 c3 01 add $0x1,%ebx
401442: 83 fb 05 cmp $0x5,%ebx
401445: 7f 17 jg 40145e <phase_2+0x4a>
401447: 48 63 c3 movslq %ebx,%rax
40144a: 8d 53 ff lea -0x1(%rbx),%edx
40144d: 48 63 d2 movslq %edx,%rdx
401450: 89 d9 mov %ebx,%ecx
401452: 03 4c 95 d0 add -0x30(%rbp,%rdx,4),%ecx
401456: 39 4c 85 d0 cmp %ecx,-0x30(%rbp,%rax,4)
40145a: 74 e3 je 40143f <phase_2+0x2b>
40145c: eb dc jmp 40143a <phase_2+0x26>
40145e: 48 83 c4 28 add $0x28,%rsp
401462: 5b pop %rbx
401463: 5d pop %rbp
401464: c3 retq
phase_3
密碼如下:1 -1199
破解過程:
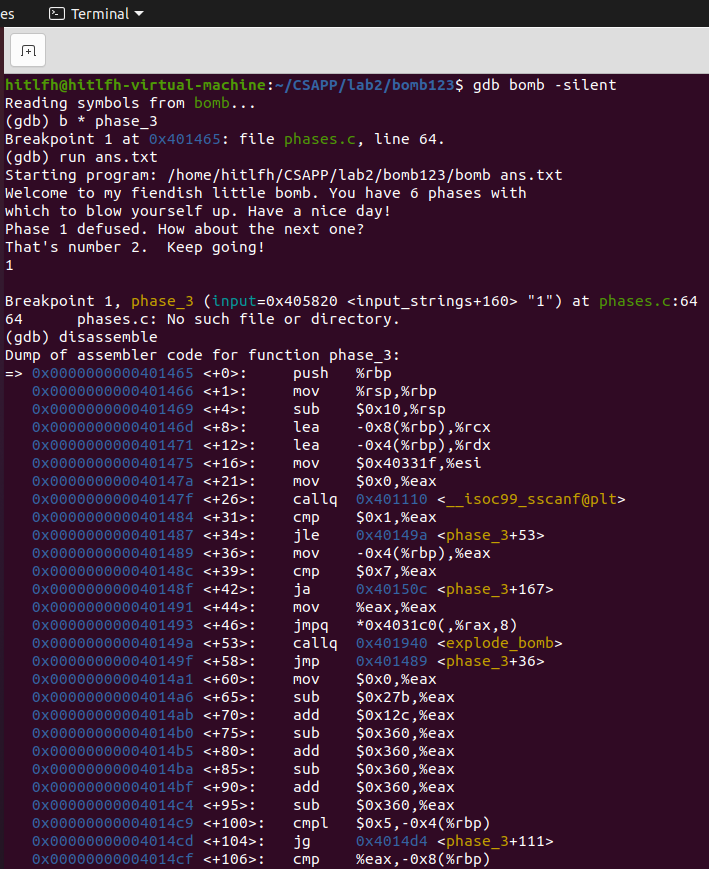
-
設定斷點,執行,反組合。
-
發現線索:
401475:be 1f 33 40 00 mov $0x40331f,%esi。 -
列印0x40331f處的字串,得到:
-

-
結合後邊的
40147f:e88cfcff ff callq 401110 <__isoc99_sscanf@plt>可知,本題答案為兩個整型變數
401489: 8b 45 fc mov -0x4(%rbp),%eax
40148c: 83 f8 07 cmp $0x7,%eax
40148f: 77 7b ja 40150c <phase_3+0xa7>
第一個輸入的數不能大於7
結合後面的可猜測,是一個根據第一個輸入的數的switch語句
-
那就輸入 1 2 進行偵錯測試
-
觀察到
4014cf: 39 45 f8 cmp %eax,-0x8(%rbp)
4014d2: 74 05 je 4014d9 <phase_3+0x74>
4014d4: e8 67 04 00 00 callq 401940 <explode_bomb>
4014d9: c9 leaveq
是函數不爆炸的出口
在這裡設定斷點,列印出%eax,得到-1199。
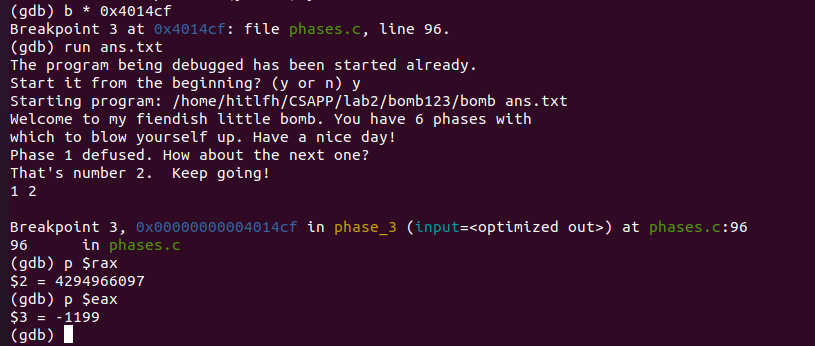
- 得到答案,1 -1199。答案不唯一。
組合程式碼:
點選檢視程式碼
0000000000401465 <phase_3>:
401465: 55 push %rbp
401466: 48 89 e5 mov %rsp,%rbp
401469: 48 83 ec 10 sub $0x10,%rsp
40146d: 48 8d 4d f8 lea -0x8(%rbp),%rcx
401471: 48 8d 55 fc lea -0x4(%rbp),%rdx
401475: be 1f 33 40 00 mov $0x40331f,%esi
40147a: b8 00 00 00 00 mov $0x0,%eax
40147f: e8 8c fc ff ff callq 401110 <__isoc99_sscanf@plt>
401484: 83 f8 01 cmp $0x1,%eax
401487: 7e 11 jle 40149a <phase_3+0x35>
401489: 8b 45 fc mov -0x4(%rbp),%eax
40148c: 83 f8 07 cmp $0x7,%eax
40148f: 77 7b ja 40150c <phase_3+0xa7>
401491: 89 c0 mov %eax,%eax
401493: ff 24 c5 c0 31 40 00 jmpq *0x4031c0(,%rax,8)
40149a: e8 a1 04 00 00 callq 401940 <explode_bomb>
40149f: eb e8 jmp 401489 <phase_3+0x24>
4014a1: b8 00 00 00 00 mov $0x0,%eax
4014a6: 2d 7b 02 00 00 sub $0x27b,%eax
4014ab: 05 2c 01 00 00 add $0x12c,%eax
4014b0: 2d 60 03 00 00 sub $0x360,%eax
4014b5: 05 60 03 00 00 add $0x360,%eax
4014ba: 2d 60 03 00 00 sub $0x360,%eax
4014bf: 05 60 03 00 00 add $0x360,%eax
4014c4: 2d 60 03 00 00 sub $0x360,%eax
4014c9: 83 7d fc 05 cmpl $0x5,-0x4(%rbp)
4014cd: 7f 05 jg 4014d4 <phase_3+0x6f>
4014cf: 39 45 f8 cmp %eax,-0x8(%rbp)
4014d2: 74 05 je 4014d9 <phase_3+0x74>
4014d4: e8 67 04 00 00 callq 401940 <explode_bomb>
4014d9: c9 leaveq
4014da: c3 retq
4014db: b8 95 02 00 00 mov $0x295,%eax
4014e0: eb c4 jmp 4014a6 <phase_3+0x41>
4014e2: b8 00 00 00 00 mov $0x0,%eax
4014e7: eb c2 jmp 4014ab <phase_3+0x46>
4014e9: b8 00 00 00 00 mov $0x0,%eax
4014ee: eb c0 jmp 4014b0 <phase_3+0x4b>
4014f0: b8 00 00 00 00 mov $0x0,%eax
4014f5: eb be jmp 4014b5 <phase_3+0x50>
4014f7: b8 00 00 00 00 mov $0x0,%eax
4014fc: eb bc jmp 4014ba <phase_3+0x55>
4014fe: b8 00 00 00 00 mov $0x0,%eax
401503: eb ba jmp 4014bf <phase_3+0x5a>
401505: b8 00 00 00 00 mov $0x0,%eax
40150a: eb b8 jmp 4014c4 <phase_3+0x5f>
40150c: e8 2f 04 00 00 callq 401940 <explode_bomb>
401511: b8 00 00 00 00 mov $0x0,%eax
401516: eb b1 jmp 4014c9 <phase_3+0x64>
phase_4
密碼如下:10 5
破解過程:
-
設定斷點,執行,反組合
-
觀察到
401562: be 1f 33 40 00 mov $0x40331f,%esi 401567: b8 00 00 00 00 mov $0x0,%eax 40156c: e8 9f fb ff ff callq 401110 <__isoc99_sscanf@plt>
呼叫scanf讀入,那麼先列印下0x40331f是什麼
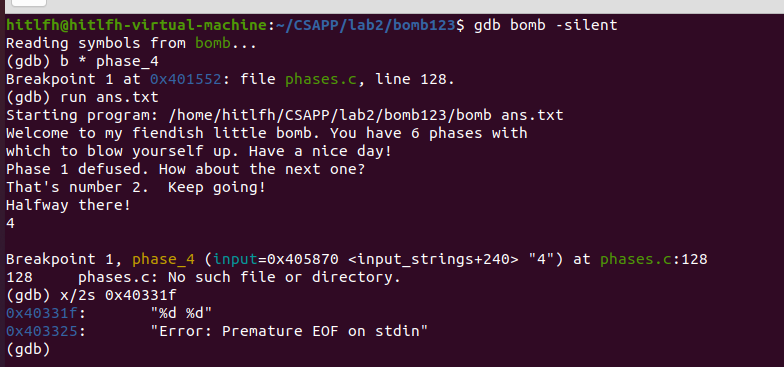
答案是兩個整型變數
- 再根據下面這段組合語言
401576:8b 45 fc mov -0x4(%rbp),%eax
401579:85 c0 test %eax,%eax
40157b:78 05 js 401582 <phase_4+0x30>
40157d:83 f8 0e cmp $0xe,%eax
401580:7e 05 jle 401587 <phase_4+0x35>
401582:e8 b9 03 00 00 callq 401940 <explode_bomb>
401587:ba 0e 00 00 00 mov $0xe,%edx
得出,輸入的第一個數範圍:[0, 14]
- 由
401594: e8 7f ff ff ff callq 401518 <func4>
401599: 83 f8 05 cmp $0x5,%eax
40159c: 75 06 jne 4015a4 <phase_4+0x52>
可知func4的返回值必須為5
- 由
40159e: 83 7d f8 05 cmpl $0x5,-0x8(%rbp)
4015a2: 74 05 je 4015a9 <phase_4+0x57>
4015a4: e8 97 03 00 00 callq 401940 <explode_bomb>
可知,輸入的第二個數必須為5
-
下面分析遞迴函數func4。
func4裡每次都用到 %edi, %esi,%edx,%eax。
而我們輸入的第一個數在一開始便是%edi 的值,%esi 一開始為0,%edx一開始為0xe,即為14。
不妨,將這四個暫存器, 記為 a,b,c,res
看看這幾段
40151c: 89 d1 mov %edx,%ecx
40151e: 29 f1 sub %esi,%ecx
401520: 89 c8 mov %ecx,%eax
401522: c1 e8 1f shr $0x1f,%eax// 邏輯右移31
401525:01c8 add %ecx,%eax 401527: d1 f8 sar %eax //算術右移
401529: 01 f0 add %esi,%eax
寫為公式:\(res = [(c - b) >> 31 + (c - b)] / 2 + b\).
化簡一下,\(res = (c - b) / 2 + b\).
再看後面的分支,和分支的執行:
if(a < res) func4(a, b, res – 1, res), res *= 2, return res
else if(a > res) func(a, res + 1, c, res), res = res * 2 + 1; return res
else return 0
- 現在從最終返回值5倒推一下:
-
\(5 = 2 * 2 + 1\) , \(res = (14 - 0) / 2 + 0 = 7\) 當前func4(a, 0, 14, 7) 則遞迴func4(a, 8, 14, 7)
-
\(2 = 2 * 1\) , \(res = (14 - 8) / 2 + 8 = 11\) 當前func4(a, 8, 14, 11) 則遞迴func4(a, 8, 10, 11)
-
\(1 = 2 * 0 + 1\) , \(res = (10 - 8) / 2 + 8 = 9\) 當前func4(a, 8, 10, 9) 則遞迴func4(a, 10, 10, 9)
-
\(0 = 0\) ,遞迴終止條件,此時$ res = (10 - 10) / 2 + 10 = 10$
好,那麼可以得出 a = 10
- 則答案為 10, 5
組合程式碼:
點選檢視程式碼
0000000000401518 <func4>:
401518: 55 push %rbp
401519: 48 89 e5 mov %rsp,%rbp
40151c: 89 d1 mov %edx,%ecx
40151e: 29 f1 sub %esi,%ecx
401520: 89 c8 mov %ecx,%eax
401522: c1 e8 1f shr $0x1f,%eax
401525: 01 c8 add %ecx,%eax
401527: d1 f8 sar %eax
401529: 01 f0 add %esi,%eax
40152b: 39 f8 cmp %edi,%eax
40152d: 7f 09 jg 401538 <func4+0x20>
40152f: 7c 13 jl 401544 <func4+0x2c>
401531: b8 00 00 00 00 mov $0x0,%eax
401536: 5d pop %rbp
401537: c3 retq
401538: 8d 50 ff lea -0x1(%rax),%edx
40153b: e8 d8 ff ff ff callq 401518 <func4>
401540: 01 c0 add %eax,%eax
401542: eb f2 jmp 401536 <func4+0x1e>
401544: 8d 70 01 lea 0x1(%rax),%esi
401547: e8 cc ff ff ff callq 401518 <func4>
40154c: 8d 44 00 01 lea 0x1(%rax,%rax,1),%eax
401550: eb e4 jmp 401536 <func4+0x1e>
0000000000401552 <phase_4>:
401552: 55 push %rbp
401553: 48 89 e5 mov %rsp,%rbp
401556: 48 83 ec 10 sub $0x10,%rsp
40155a: 48 8d 4d f8 lea -0x8(%rbp),%rcx
40155e: 48 8d 55 fc lea -0x4(%rbp),%rdx
401562: be 1f 33 40 00 mov $0x40331f,%esi
401567: b8 00 00 00 00 mov $0x0,%eax
40156c: e8 9f fb ff ff callq 401110 <__isoc99_sscanf@plt>
401571: 83 f8 02 cmp $0x2,%eax
401574: 75 0c jne 401582 <phase_4+0x30>
401576: 8b 45 fc mov -0x4(%rbp),%eax
401579: 85 c0 test %eax,%eax
40157b: 78 05 js 401582 <phase_4+0x30>
40157d: 83 f8 0e cmp $0xe,%eax
401580: 7e 05 jle 401587 <phase_4+0x35>
401582: e8 b9 03 00 00 callq 401940 <explode_bomb>
401587: ba 0e 00 00 00 mov $0xe,%edx
40158c: be 00 00 00 00 mov $0x0,%esi
401591: 8b 7d fc mov -0x4(%rbp),%edi
401594: e8 7f ff ff ff callq 401518 <func4>
401599: 83 f8 05 cmp $0x5,%eax
40159c: 75 06 jne 4015a4 <phase_4+0x52>
40159e: 83 7d f8 05 cmpl $0x5,-0x8(%rbp)
4015a2: 74 05 je 4015a9 <phase_4+0x57>
4015a4: e8 97 03 00 00 callq 401940 <explode_bomb>
4015a9: c9 leaveq
4015aa: c3 retq
phase_5
密碼如下:ionefg
破解過程:
-
設定斷點,執行,反組合
-
觀察到
4015b7: e8 74 02 00 00 callq 401830 <string_length>
4015bc: 83 f8 06 cmp $0x6,%eax
4015bf: 75 24 jne 4015e5 <phase_5+0x3a>
推測輸入為字串,且長度為6
- 再看接下來一段
4015c1: b8 00 00 00 00 mov $0x0,%eax
4015c6: 83 f8 05 cmp $0x5,%eax//迴圈了6次
4015c9: 7f 21 jg 4015ec <phase_5+0x41>
4015cb: 48 63 c8 movslq %eax,%rcx
4015ce: 0f b6 14 0b movzbl (%rbx,%rcx,1),%edx
// 逐個取你輸的字元
4015d2: 83 e2 0f and $0xf,%edx // 轉為[0,15]
4015d5: 0f b6 92 00 32 40 00 movzbl 0x403200(%rdx),%edx
4015dc: 88 54 0d e9 mov %dl,-0x17(%rbp,%rcx,1)
4015e0: 83 c0 01 add $0x1,%eax
可以看出,它取出字串中每一個字元,然後轉為[0, 15]的一個數,然後從地址0x403200 加這個數的偏移量,然後取出一個東西,再把它放入棧的記憶體中,注意!這裡的%dl說明是一個位元組,那不還是字元嘛
好,先列印下0x403200處的字串
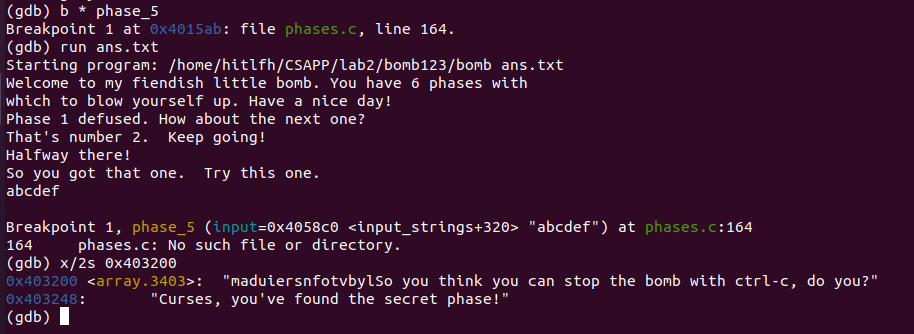
發現列印出的一段奇怪的字串。
但是,根據剛剛分析出的[0,15]的偏移量,我們取出前16個字元
得到:maduiersnfotvbyl
-
再將斷點設在迴圈內,每次列印出%dl , 發現對於輸入的abcdef,得到了aduier的ASCII碼,再聯絡一下ASCII碼的十六進位制,a 為0x61。和0xf做與運算得到 0x1 。
-
發現,輸出的字串中的字元的ASCII碼對0x60的偏移量 與 原字串的字元的下標是相等的。
-
繼續向下看
4015f0: be ae 31 40 00 mov $0x4031ae,%esi
4015f5: 48 8d 7d e9 lea -0x17(%rbp),%rdi
4015f9: e8 46 02 00 00 callq 401844 <strings_not_equal>
4015fe: 85 c0 test %eax,%eax
401600: 75 07 jne 401609 <phase_5+0x5e>
發現又是字串匹配,先看看0x4031ae處的字串
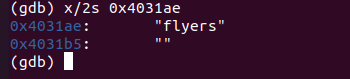
根據前面得到的結論。先取出這些字元,看在原字串中的下標。
得到:9 15 14 5 6 7,然後加上0x60, 查閱ASCII碼
得到:ionefg
組合程式碼:
點選檢視程式碼
00000000004015ab <phase_5>:
4015ab: 55 push %rbp
4015ac: 48 89 e5 mov %rsp,%rbp
4015af: 53 push %rbx
4015b0: 48 83 ec 18 sub $0x18,%rsp
4015b4: 48 89 fb mov %rdi,%rbx
4015b7: e8 74 02 00 00 callq 401830 <string_length>
4015bc: 83 f8 06 cmp $0x6,%eax
4015bf: 75 24 jne 4015e5 <phase_5+0x3a>
4015c1: b8 00 00 00 00 mov $0x0,%eax
// 迴圈6次 0~5
4015c6: 83 f8 05 cmp $0x5,%eax
4015c9: 7f 21 jg 4015ec <phase_5+0x41>
4015cb: 48 63 c8 movslq %eax,%rcx
4015ce: 0f b6 14 0b movzbl (%rbx,%rcx,1),%edx // 逐個取你輸的字元
4015d2: 83 e2 0f and $0xf,%edx // 轉為[0,15]
4015d5: 0f b6 92 00 32 40 00 movzbl 0x403200(%rdx),%edx
4015dc: 88 54 0d e9 mov %dl,-0x17(%rbp,%rcx,1)
4015e0: 83 c0 01 add $0x1,%eax
4015e3: eb e1 jmp 4015c6 <phase_5+0x1b>
4015e5: e8 56 03 00 00 callq 401940 <explode_bomb>
4015ea: eb d5 jmp 4015c1 <phase_5+0x16>
4015ec: c6 45 ef 00 movb $0x0,-0x11(%rbp)
4015f0: be ae 31 40 00 mov $0x4031ae,%esi
4015f5: 48 8d 7d e9 lea -0x17(%rbp),%rdi
4015f9: e8 46 02 00 00 callq 401844 <strings_not_equal>
4015fe: 85 c0 test %eax,%eax
401600: 75 07 jne 401609 <phase_5+0x5e>
401602: 48 83 c4 18 add $0x18,%rsp
401606: 5b pop %rbx
401607: 5d pop %rbp
401608: c3 retq
401609: e8 32 03 00 00 callq 401940 <explode_bomb>
40160e: eb f2 jmp 401602 <phase_5+0x57>
phase_6
密碼如下:2 6 4 3 1 5
破解過程:
-
設定斷點,執行,反組合
-
解讀組合程式碼知:
- 讀6個數
- 二重回圈,判斷是否每個數大於6,判斷是否和其他數相等。即,輸入的應該為1~6的排列
- 將每個數i轉化為\(j = 7 – i\)
- 取出連結串列的第j個元素的值,放入棧中
- 遍歷一遍放入棧的6個連結串列元素,判斷是否為降序
-
連結串列的發現:
4016be: ba d0 52 40 00 mov $0x4052d0,%edx // 連結串列頭
4016c9: 48 89 d9 mov %rbx,%rcx
4016db: 48 89 51 08 mov %rdx,0x8(%rcx) //next指標
發現是鏈式結構,設定斷點,列印出:
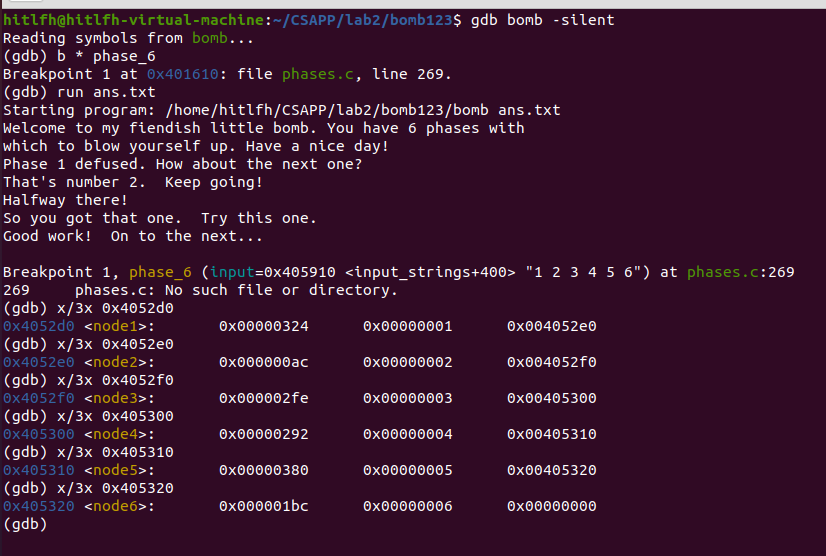
發現nodej也是在提示
第一個為連結串列值,第二個為連結串列遊標,第三個為next指標
-
那麼,將連結串列值按降序排序,得到遊標為5 1 3 4 6 2
-
再,由 \(j = 7 – i\), 得到答案 2 6 4 3 1 5
組合程式碼:
點選檢視程式碼
0000000000401610 <phase_6>:
401610: 55 push %rbp
401611: 48 89 e5 mov %rsp,%rbp
401614: 41 55 push %r13
401616: 41 54 push %r12
401618: 53 push %rbx
401619: 48 83 ec 58 sub $0x58,%rsp
40161d: 48 8d 75 c0 lea -0x40(%rbp),%rsi
401621: e8 3c 03 00 00 callq 401962 <read_six_numbers>
401626: 41 bc 00 00 00 00 mov $0x0,%r12d // %r12d = 0
40162c: eb 29 jmp 401657 <phase_6+0x47>
40162e: e8 0d 03 00 00 callq 401940 <explode_bomb>
401633: eb 37 jmp 40166c <phase_6+0x5c>
401635: e8 06 03 00 00 callq 401940 <explode_bomb>
40163a: 83 c3 01 add $0x1,%ebx
===============================================================
------------------------------------------------------------
40163d: 83 fb 05 cmp $0x5,%ebx // if(%ebx > 5)
401640: 7f 12 jg 401654 <phase_6+0x44>
401642: 49 63 c4 movslq %r12d,%rax // %rax = %r12d
401645: 48 63 d3 movslq %ebx,%rdx // %rdx = %ebx
401648: 8b 7c 95 c0 mov -0x40(%rbp,%rdx,4),%edi
40164c: 39 7c 85 c0 cmp %edi,-0x40(%rbp,%rax,4)
401650: 75 e8 jne 40163a <phase_6+0x2a>
-----------------------------------------------------------
401652: eb e1 jmp 401635 <phase_6+0x25>
401654: 45 89 ec mov %r13d,%r12d
401657: 41 83 fc 05 cmp $0x5,%r12d // cmp %r12d 5
40165b: 7f 19 jg 401676 <phase_6+0x66> // >
40165d: 49 63 c4 movslq %r12d,%rax // %rax = %r12d
401660: 8b 44 85 c0 mov -0x40(%rbp,%rax,4),%eax
401664: 83 e8 01 sub $0x1,%eax // %rax -= 1
401667: 83 f8 05 cmp $0x5,%eax // if rax > 5
40166a: 77 c2 ja 40162e <phase_6+0x1e>
40166c: 45 8d 6c 24 01 lea 0x1(%r12),%r13d
// %r13d=(%r12d+1)
401671: 44 89 eb mov %r13d,%ebx // %ebx = %r13d
401674: eb c7 jmp 40163d <phase_6+0x2d>
================================================================
401676: b8 00 00 00 00 mov $0x0,%eax // %eax = 0
40167b: eb 13 jmp 401690 <phase_6+0x80>
// j = 7 - i
==========================================================
40167d: 48 63 c8 movslq %eax,%rcx
401680: ba 07 00 00 00 mov $0x7,%edx
401685: 2b 54 8d c0 sub -0x40(%rbp,%rcx,4),%edx
從第一個數開始
401689: 89 54 8d c0 mov %edx,-0x40(%rbp,%rcx,4)
40168d: 83 c0 01 add $0x1,%eax
401690: 83 f8 05 cmp $0x5,%eax
401693: 7e e8 jle 40167d <phase_6+0x6d>
==========================================================
401695: be 00 00 00 00 mov $0x0,%esi
40169a: eb 18 jmp 4016b4 <phase_6+0xa4>
40169c: 48 8b 52 08 mov 0x8(%rdx),%rdx
4016a0: 83 c0 01 add $0x1,%eax
//二重回圈,尋找第j個連結串列元素
==============================================================
4016a3: 48 63 ce movslq %esi,%rcx
4016a6: 39 44 8d c0 cmp %eax,-0x40(%rbp,%rcx,4)
4016aa: 7f f0 jg 40169c <phase_6+0x8c>
4016ac: 48 89 54 cd 90 mov %rdx,-0x70(%rbp,%rcx,8)
4016b1: 83 c6 01 add $0x1,%esi
4016b4: 83 fe 05 cmp $0x5,%esi
4016b7: 7f 0c jg 4016c5 <phase_6+0xb5>
4016b9: b8 01 00 00 00 mov $0x1,%eax
4016be: ba d0 52 40 00 mov $0x4052d0,%edx // 連結串列頭
4016c3: eb de jmp 4016a3 <phase_6+0x93>
4016c5: 48 8b 5d 90 mov -0x70(%rbp)
4016c9: 48 89 d9 mov %rbx,%rcx //%rcx = %rbx
4016cc: b8 01 00 00 00 mov $0x1,%eax // eax = 1
4016d1: eb 12 jmp 4016e5 <phase_6+0xd5>
4016d3: 48 63 d0 movslq %eax,%rdx // rdx = eax
4016d6: 48 8b 54 d5 90 mov -0x70(%rbp,%rdx,8),%rdx
4016db: 48 89 51 08 mov %rdx,0x8(%rcx)
4016df: 83 c0 01 add $0x1,%eax
4016e2: 48 89 d1 mov %rdx,%rcx // rcx = rdx
4016e5: 83 f8 05 cmp $0x5,%eax // while 迴圈
4016e8: 7e e9 jle 4016d3 <phase_6+0xc3>
=========================================================
4016ea: 48 c7 41 08 00 00 00 movq $0x0,0x8(%rcx)
4016f1: 00
4016f2: 41 bc 00 00 00 00 mov $0x0,%r12d
4016f8: eb 08 jmp 401702 <phase_6+0xf2>
4016fa: 48 8b 5b 08 mov 0x8(%rbx),%rbx
4016fe: 41 83 c4 01 add $0x1,%r12d
401702: 41 83 fc 04 cmp $0x4,%r12d
401706: 7f 11 jg 401719 <phase_6+0x109>
401708: 48 8b 43 08 mov 0x8(%rbx),%rax
40170c: 8b 00 mov (%rax),%eax
40170e: 39 03 cmp %eax,(%rbx)
401710: 7d e8 jge 4016fa <phase_6+0xea>
// 這裡是一重回圈,判斷是否前個元素大於等於後一個元素,即降序
// 否則爆炸
401712: e8 29 02 00 00 callq 401940 <explode_bomb>
401717: eb e1 jmp 4016fa <phase_6+0xea>
401719: 48 83 c4 58 add $0x58,%rsp
40171d: 5b pop %rbx
40171e: 41 5c pop %r12
401720: 41 5d pop %r13
401722: 5d pop %rbp
401723: c3 retq
secret_phase
密碼如下:47
破解過程:
- 首先要找到入口,看phase_defused函數
0000000000401ac9 <phase_defused>:
401ac9: 83 3d 9c 3c 00 00 06 cmpl $0x6,0x3c9c(%rip) \#40576c <num_input_strings>
401ad0: 74 01 je 401ad3 <phase_defused+0xa>
在0x401ad0處設定斷點,然後列印出0x3c9c(%rip)
發現分別為 1 2 3 4 5 6
則可以推斷出,要在6個炸彈都拆後才可以進入後邊。
401ae7: be 69 33 40 00 mov $0x403369,%esi
401aec: bf 70 58 40 00 mov $0x405870,%edi
----
401b0c: be 72 33 40 00 mov $0x403372,%esi
401b11: 48 8d 7d b0 lea -0x50(%rbp),%rdi
401b15: e8 2a fd ff ff callq 401844 <strings_not_equal>
先列印出這三個地址的字串:

可以推斷出,輸入為兩個整型變數和一個字串。
且這個字串必須為DrEvil。但是,phase_4和phase_3的輸入都是兩個整數
那麼我們在判斷字串相等處,設定斷點,列印出值觀察:
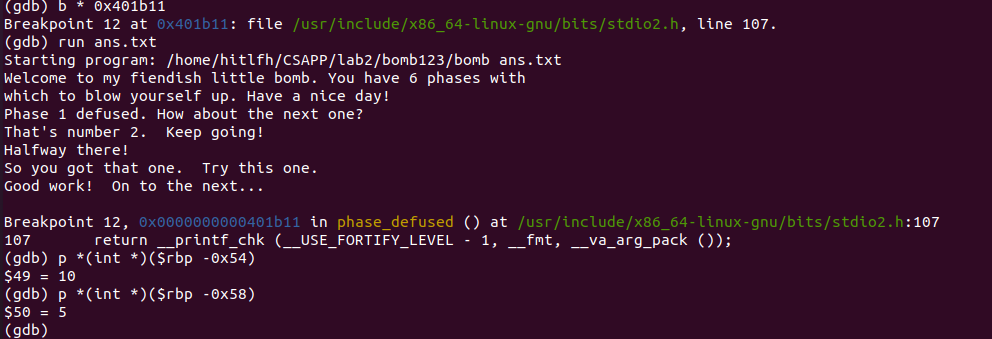
10 和 5!
那麼就確定為phase_4的答案後加上DrEvil
-
成功進入隱藏關。
-
看secret_phase函數
000000000040175e <secret_phase>:
401767: e8 32 02 00 00 callq 40199e <read_line>
40176f: e8 cc f9 ff ff callq 401140 <atoi@plt
發現了readline函數和atoi函數,說明是輸一個數位。(atoi函數作用為將字串轉為整型)
401776: 8d 40 ff lea -0x1(%rax),c%eax
401779: 3d e8 03 00 00 cmp $0x3e8,%eax //1000
40177e: 77 27 ja 4017a7 <secret_phase+0x49>
401780: 89 de mov %ebx,%esi
401782: bf f0 50 40 00 mov $0x4050f0,%edi//此處地址的值為36
401787: e8 98 ff ff ff callq 401724 <fun7>
40178c: 83 f8 05 cmp $0x5,%eax //返回值得為5
則輸出值不超1001
輸入進func7後,返回值必須為5
-
再看func7函數又是一個分支+遞迴。
直接寫出虛擬碼:
記%rdi 為 p,%rax 為 res, %esi為 x,
則func7(* p, int res, int x) 。
一開始,\(*p = 36\), x為你輸入的數。
if(x < *p)
p = *(p + 8),func7(p, res, x), res *= 2,return res;
else if(x > *p)
p = *(p + 10),func7(p, res, x), res = res * 2 + 1,return res;
else
return 0;
那麼現在由返回值5逆推
5 = 2 * 2 + 1 p = *p + 10
2 = 2 * 1 p = *p + 8
1 = 2 * 0 + 1 p = *p + 10
0 = 0 *p == x
則可以偵錯列印出:
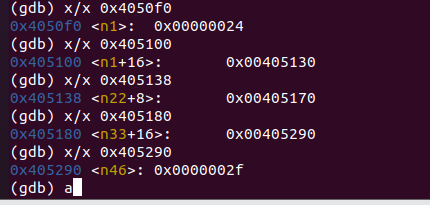
- \(0x2f = 47\)
組合程式碼:
點選檢視程式碼
0000000000401724 <fun7>:
401724: 48 85 ff test %rdi,%rdi
401727: 74 2f je 401758 <fun7+0x34>
401729: 55 push %rbp
40172a: 48 89 e5 mov %rsp,%rbp
40172d: 8b 07 mov (%rdi),%eax
40172f: 39 f0 cmp %esi,%eax
401731: 7f 09 jg 40173c <fun7+0x18>
401733: 75 14 jne 401749 <fun7+0x25>
401735: b8 00 00 00 00 mov $0x0,%eax
40173a: 5d pop %rbp
40173b: c3 retq
40173c: 48 8b 7f 08 mov 0x8(%rdi),%rdi
401740: e8 df ff ff ff callq 401724 <fun7>
401745: 01 c0 add %eax,%eax
401747: eb f1 jmp 40173a <fun7+0x16>
401749: 48 8b 7f 10 mov 0x10(%rdi),%rdi
40174d: e8 d2 ff ff ff callq 401724 <fun7>
401752: 8d 44 00 01 lea 0x1(%rax,%rax,1),%eax
401756: eb e2 jmp 40173a <fun7+0x16>
401758: b8 ff ff ff ff mov $0xffffffff,%eax
40175d: c3 retq
000000000040175e <secret_phase>:
40175e: 55 push %rbp
40175f: 48 89 e5 mov %rsp,%rbp
401762: 53 push %rbx
401763: 48 83 ec 08 sub $0x8,%rsp
401767: e8 32 02 00 00 callq 40199e <read_line>
40176c: 48 89 c7 mov %rax,%rdi
40176f: e8 cc f9 ff ff callq 401140 <atoi@plt>
401774: 89 c3 mov %eax,%ebx
401776: 8d 40 ff lea -0x1(%rax),%eax
401779: 3d e8 03 00 00 cmp $0x3e8,%eax
40177e: 77 27 ja 4017a7 <secret_phase+0x49>
401780: 89 de mov %ebx,%esi
401782: bf f0 50 40 00 mov $0x4050f0,%edi
401787: e8 98 ff ff ff callq 401724 <fun7>
40178c: 83 f8 05 cmp $0x5,%eax
40178f: 75 1d jne 4017ae <secret_phase+0x50>
401791: bf 88 31 40 00 mov $0x403188,%edi
401796: e8 c5 f8 ff ff callq 401060 <puts@plt>
40179b: e8 29 03 00 00 callq 401ac9 <phase_defused>
4017a0: 48 83 c4 08 add $0x8,%rsp
4017a4: 5b pop %rbx
4017a5: 5d pop %rbp
4017a6: c3 retq
4017a7: e8 94 01 00 00 callq 401940 <explode_bomb>
4017ac: eb d2 jmp 401780 <secret_phase+0x22>
4017ae: e8 8d 01 00 00 callq 401940 <explode_bomb>
4017b3: eb dc jmp 401791 <secret_phase+0x33>
0000000000401ac9 <phase_defused>:
401ac9: 83 3d 9c 3c 00 00 06 cmpl $0x6,0x3c9c(%rip) # 40576c <num_input_strings>
401ad0: 74 01 je 401ad3 <phase_defused+0xa>
401ad2: c3 retq
401ad3: 55 push %rbp
401ad4: 48 89 e5 mov %rsp,%rbp
401ad7: 48 83 ec 60 sub $0x60,%rsp
401adb: 4c 8d 45 b0 lea -0x50(%rbp),%r8
401adf: 48 8d 4d a8 lea -0x58(%rbp),%rcx
401ae3: 48 8d 55 ac lea -0x54(%rbp),%rdx
401ae7: be 69 33 40 00 mov $0x403369,%esi
401aec: bf 70 58 40 00 mov $0x405870,%edi
401af1: b8 00 00 00 00 mov $0x0,%eax
401af6: e8 15 f6 ff ff callq 401110 <__isoc99_sscanf@plt>
401afb: 83 f8 03 cmp $0x3,%eax
401afe: 74 0c je 401b0c <phase_defused+0x43>
401b00: bf a8 32 40 00 mov $0x4032a8,%edi
401b05: e8 56 f5 ff ff callq 401060 <puts@plt>
401b0a: c9 leaveq
401b0b: c3 retq
401b0c: be 72 33 40 00 mov $0x403372,%esi
401b11: 48 8d 7d b0 lea -0x50(%rbp),%rdi
401b15: e8 2a fd ff ff callq 401844 <strings_not_equal>
401b1a: 85 c0 test %eax,%eax
401b1c: 75 e2 jne 401b00 <phase_defused+0x37>
401b1e: bf 48 32 40 00 mov $0x403248,%edi
401b23: e8 38 f5 ff ff callq 401060 <puts@plt>
401b28: bf 70 32 40 00 mov $0x403270,%edi
401b2d: e8 2e f5 ff ff callq 401060 <puts@plt>
401b32: b8 00 00 00 00 mov $0x0,%eax
401b37: e8 22 fc ff ff callq 40175e <secret_phase>
401b3c: eb c2 jmp 401b00 <phase_defused+0x37>
後記
做了一遍挺痛苦,然後寫實驗報告梳理了一遍思路,還是挺有收穫的。
本文來自部落格園,作者:江水為竭,轉載請註明原文連結:https://www.cnblogs.com/Az1r/p/16769856.html