.NET 反向代理-YARP 部署Https(SSL)
YARP 作為反向代理中介軟體,那就無可避免需要使用到 Https 去部署專案,那 YARP 要怎麼去實現呢,本來以為 YARP 會有一套自己的實現,在翻閱了資料後發現,根本不是我想的那樣,按照 YARP 官方檔案的說法,是按照 .Net Core 原本的那一套去實現,好傢伙,真的沒想到啊,下面我貼出官方原文,大夥看一看,瞧一瞧
IIS就不多說了,這個畢竟只能在 windows 上使用,下面我說說 在 Kestrel 怎麼設定 Https 吧,按照我的慣例,直接貼組態檔
"Kestrel": { "Endpoints": { "MySniEndpoint": { "Url": "https://*:5209", "SslProtocols": [ "Tls11", "Tls12" ], "Sni": { "test1.ysmc.net.cn": { "Certificate": { "Path": "[path]\\test1.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } }, "test2.ysmc.net.cn": { "Certificate": { "Path": "[path]\\test2.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } } } } }, //,預設設定,當沒有設定的時候,預設回落到這個設定 "Certificates": { "Default": { "Path": "[path]\\test1.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } }
因為我們需要設定多個域名,所以使用到了 Sni,下面是官方對一 Sni 的部分介紹,感興趣的小夥伴可以過去看看,傳送門
SNI in configuration
Kestrel supports SNI defined in configuration. An endpoint can be configured with an object that contains a mapping between host names and HTTPS options. The connection host name is matched to the options and they are used for that connection.Sni
The following configuration adds an endpoint named that uses SNI to select HTTPS options based on the host name:MySniEndpoint
HTTPS options that can be overridden by SNI:
Certificateconfigures the certificate source.Protocolsconfigures the allowed HTTP protocols.SslProtocolsconfigures the allowed SSL protocols.ClientCertificateModeconfigures the client certificate requirements.
The host name supports wildcard matching:
- Exact match. For example, matches .
a.example.orga.example.org - Wildcard prefix. If there are multiple wildcard matches then the longest pattern is chosen. For example, matches and .
*.example.orgb.example.orgc.example.org - Full wildcard. matches everything else, including clients that aren't using SNI and don't send a host name.
*
The matched SNI configuration is applied to the endpoint for the connection, overriding values on the endpoint. If a connection doesn't match a configured SNI host name then the connection is refused.
下面一起看看設定後的效果吧,非常的完美
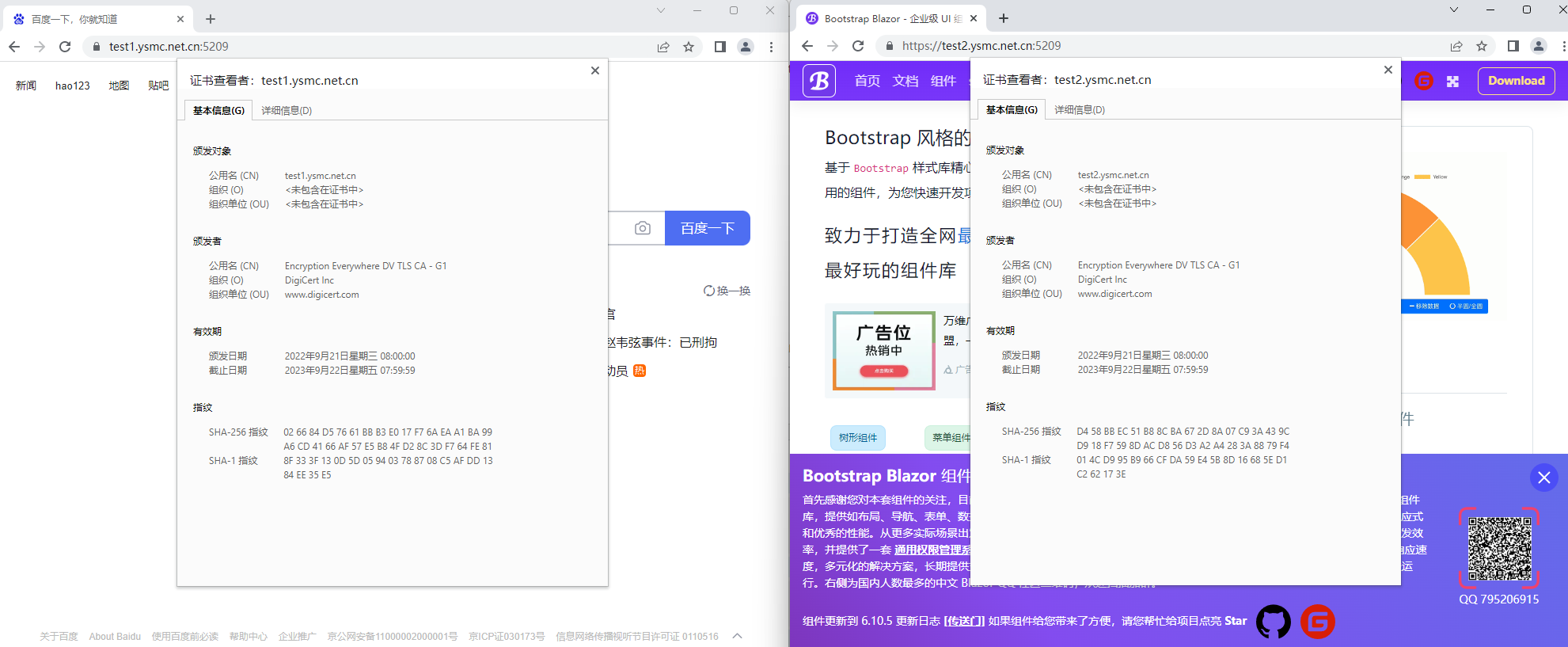
整個完整的組態檔我也貼出來吧,至於證書怎麼申請的,大家有域名的可以到域名服務商裡申請免費1年期的,沒有域名的話,可以自己改一下hosts 檔案 然後自己自簽名一個,都是可以的
appsettings.json
{ "Logging": { "LogLevel": { "Default": "Information", "Microsoft.AspNetCore": "Warning" } }, "Kestrel": { "Endpoints": { "MySniEndpoint": { "Url": "https://*:5209", "SslProtocols": [ "Tls11", "Tls12" ], "Sni": { "test1.ysmc.net.cn": { "Certificate": { "Path": "[path]\\test1.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } }, "test2.ysmc.net.cn": { "Certificate": { "Path": "[path]\\test2.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } } } } }, "Certificates": { "Default": { "Path": "[path]\\test1.ysmc.net.cn_server.pfx", "Password": "pfx密碼" } } }, "ReverseProxy": { "Routes": { "baidu": { "ClusterId": "baidu", "Match": { "Hosts": [ "test1.ysmc.net.cn" ], "Path": "{**catch-all}" } }, "blazor": { "ClusterId": "blazor", "Match": { "Hosts": [ "test2.ysmc.net.cn" ], "Path": "{**catch-all}" } } }, "Clusters": { "baidu": { "LoadBalancingPolicy": "RoundRobin", "Destinations": { "baidu": { "Address": "https://www.baidu.com/" } } }, "blazor": { "LoadBalancingPolicy": "RoundRobin", "Destinations": { "blazor": { "Address": "https://www.blazor.zone/" } } } } } }
原文連結:https://www.cnblogs.com/ysmc/p/16717580.html