ansible 002 連線被控端 inventory ansible.cfg ansible-adhoc ansible原理
ssh用普通使用者連線被控端
設定主機清單 (/etc/hosts域名解析為前提)
[root@workstation ansible]# cat hosts
servera
serverb
[root@workstation ansible]# pwd
/etc/ansible
[root@workstation ansible]#
建立免密
[root@workstation ansible]# ssh-keygen
使被控端建立使用者
[root@workstation ansible]# ansible all -m shell -a 'useradd ansible' -k
SSH password:
servera | CHANGED | rc=0 >>
serverb | CHANGED | rc=0 >>
[root@workstation ansible]# ansible all -m shell -a 'echo redhat | passwd --stdin ansible' -k
SSH password:
serverb | CHANGED | rc=0 >>
Changing password for user ansible.
passwd: all authentication tokens updated successfully.
servera | CHANGED | rc=0 >>
Changing password for user ansible.
passwd: all authentication tokens updated successfully.
設定與ansible使用者的免密
[root@workstation ansible]# ssh-copy-id ansible@servera
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
ansible@servera's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'ansible@servera'"
and check to make sure that only the key(s) you wanted were added.
[root@workstation ansible]# ssh-copy-id ansible@serverb
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
ansible@serverb's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'ansible@serverb'"
and check to make sure that only the key(s) you wanted were added.
[root@workstation ansible]#
[root@workstation ansible]# ansible all -m shell -a 'pwd' -k -u ansible
SSH password:
servera | CHANGED | rc=0 >>
/home/ansible
serverb | CHANGED | rc=0 >>
/home/ansible
[root@workstation ansible]#
預設改為ansible使用者連線
[root@workstation ansible]# ansible all -m shell -a 'pwd'
servera | CHANGED | rc=0 >>
/home/ansible
serverb | CHANGED | rc=0 >>
/home/ansible
[root@workstation ansible]#
設定被控端提權
[root@workstation ansible]# ansible all -m shell -a 'echo ansible ALL=\(ALL\) NOPASSWD: ALL > /etc/sudoers.d/ansible' -u root -k
SSH password:
servera | CHANGED | rc=0 >>
serverb | CHANGED | rc=0 >>
ansible這邊並沒有提權
[root@workstation ansible]# ansible all -m shell -a 'id'
servera | CHANGED | rc=0 >>
uid=1001(ansible) gid=1001(ansible) groups=1001(ansible) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
serverb | CHANGED | rc=0 >>
uid=1000(ansible) gid=1000(ansible) groups=1000(ansible) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@workstation ansible]#
修改組態檔
成功提權
[root@workstation ansible]# ansible all -m shell -a 'id'
servera | CHANGED | rc=0 >>
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
serverb | CHANGED | rc=0 >>
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@workstation ansible]#
[root@workstation ansible]# ansible all -m shell -a 'pwd'
servera | CHANGED | rc=0 >>
/home/ansible
serverb | CHANGED | rc=0 >>
/home/ansible
[root@workstation ansible]#
定義inventory
列出當前選擇的主機
[root@workstation ansible]# ansible servera --list-hosts
hosts (1):
servera
[root@workstation ansible]# ansible servera,serverb --list-hosts
hosts (2):
servera
serverb
[root@workstation ansible]# ansible httpd,mysql --list-hosts
hosts (3):
servera
serverb
abc
[root@workstation ansible]# cat hosts
[httpd]
servera
serverb
[mysql]
abc
[root@workstation ansible]#
這裡hosts為ini格式和那個yum差不多
不想加入組的使用者得寫在第一排。
[root@workstation ansible]# ansible ungrouped --list-hosts
hosts (1):
servere
[root@workstation ansible]# head -n3 hosts
servere
[httpd]
servera
[root@workstation ansible]#
servere不屬於任何組
組包含組
[root@workstation ansible]# vi hosts
[root@workstation ansible]# ansible web --list-hosts
hosts (3):
servera
serverb
abc
[root@workstation ansible]# cat hosts
servere
[httpd]
servera
serverb
[mysql]
abc
[web:children]
httpd
mysql #那麼這裡就只能寫組,不可以寫主機
[root@workstation ansible]#
[web:children]
httpd
mysql
[web]
fox #這樣才可以新增fox主機
ansible選擇了兩邊主機,ansible會自動去重。
支援萬用字元
組和主機都通配
[root@workstation ansible]# ansible 'server*' --list-hosts
hosts (3):
servere
servera
serverb
[root@workstation ansible]#
hosts也可以連續定義
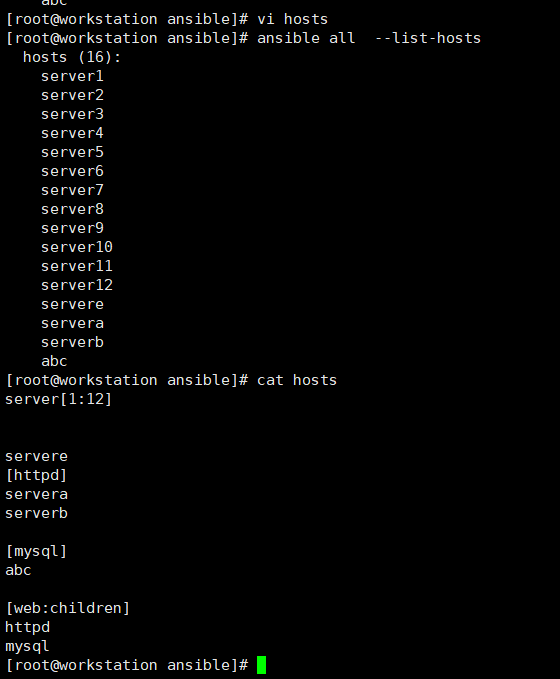
[root@workstation ansible]# ansible 'server*,!*server1' --list-hosts
hosts (14):
server2
server3
server4
server5
server6
server7
server8
server9
server10
server11
server12
servere
servera
serverb
[root@workstation ansible]#
唯獨不要server1
[root@workstation ansible]# ansible 'httpd,&mysql' --list-hosts
hosts (1):
server10
[root@workstation ansible]# cat hosts
server[1:12]
servere
[httpd]
servera
serverb
server10
[mysql]
abc
server10
[web:children]
httpd
mysql
[root@workstation ansible]#
既屬於web又屬於httpd
boston,londor,&prod,!lb
在boston與londor同時也在prod但是去除lb
正規表示式
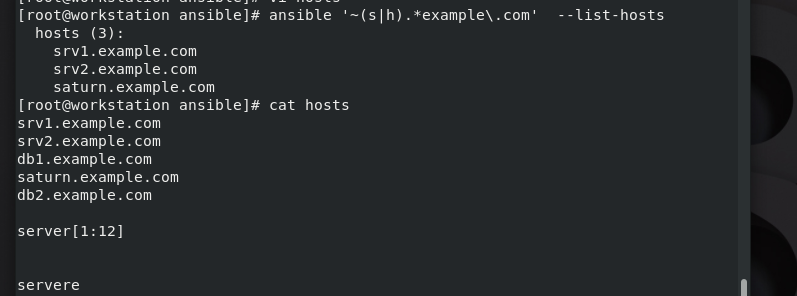
有s或h字母 尾巴為example.com的
沒帶^就不是開頭為s或h
另外指定新的主機清單。讀新的hosts
[root@workstation ansible]# echo servera > file
[root@workstation ansible]# ansible servera -i file --list-hosts
hosts (1):
servera
[root@workstation ansible]#
有關ansible常用引數
-m 指定模組
-a 指定模組引數
-u 指定被控端的連線使用者2
-k 密碼驗證,不指定就是祕鑰驗證
-i 指定主機清單 ansible servera -i file --list-hosts
--list-hosts 列出所選的主機
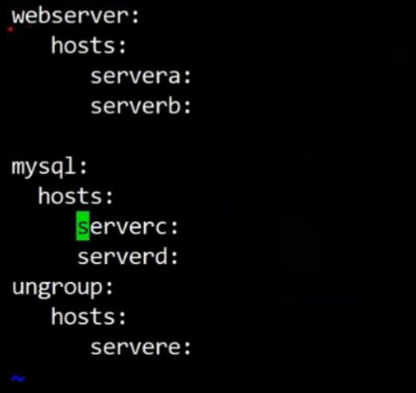
yaml格式定義主機清單
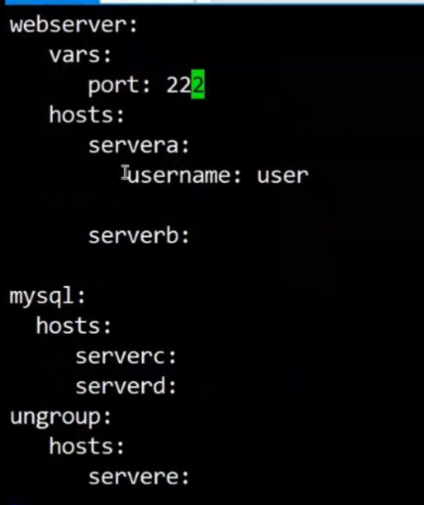
比較完整的yaml寫法
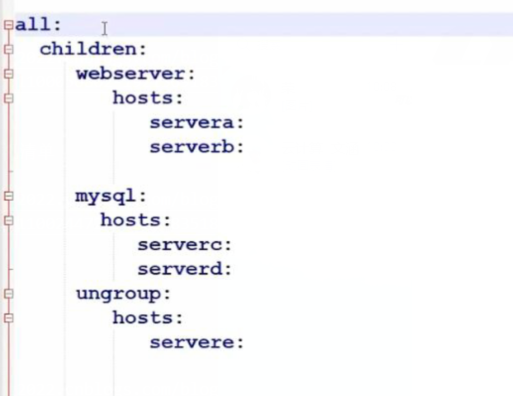
ini格式轉換yaml
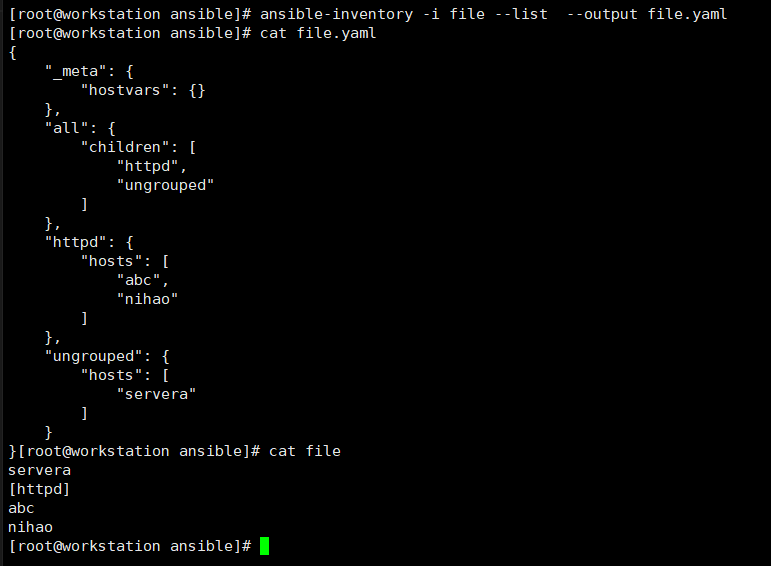
yaml語法對程式更友好
組態檔
預設組態檔位置
[root@workstation ansible]# pwd
/etc/ansible
[root@workstation ansible]# ls
ansible.cfg file file.yaml hosts roles
[root@workstation ansible]#
組態檔有優先順序讀取順序
ANSIBLE_CONFIG = /tmp/ansible.cfg
當前目錄下的ansible.cfg ./
家目錄 ~/.ansible.cfg
/etc/ansible/ansible.cfg
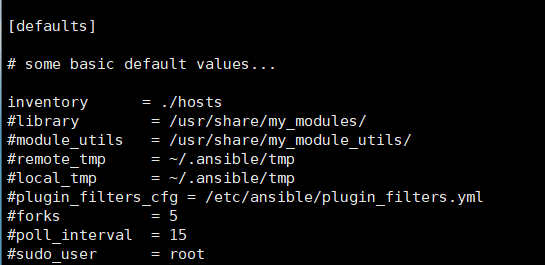
更改執行主機清單的路徑
ansible.cfg的引數
inventory = ./hosts
#library = /usr/share/my_modules/
#module_utils = /usr/share/my_module_utils/
#remote_tmp = ~/.ansible/tmp
#local_tmp = ~/.ansible/tmp
#plugin_filters_cfg = /etc/ansible/plugin_filters.yml
#forks = 5
inventory = ./hosts
#library = /usr/share/my_modules/
#module_utils = /usr/share/my_module_utils/
#remote_tmp = ~/.ansible/tmp 被控端路徑 py的臨時執行目錄的位置
#local_tmp = ~/.ansible/tmp 主控端臨時儲存目錄
#plugin_filters_cfg = /etc/ansible/plugin_filters.yml
#forks = 5 並行數 一次性連5臺,再連5臺
#poll_interval = 15 探測任務執行如何 每15秒探測
#ask_pass = True 密碼驗證 -k 預設false
#remote_port = 22 被控端,埠號
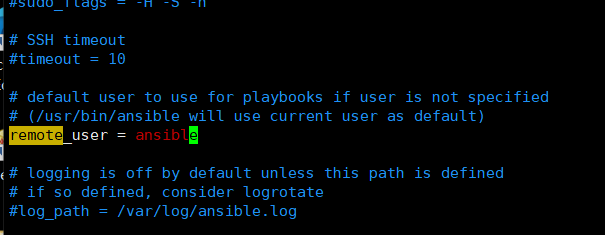
remote_user = ansible 遠端主機用什麼連
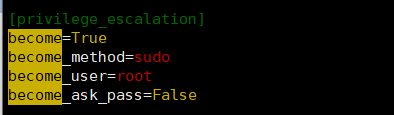
[privilege_escalation]
become=True 要提權
become_method=sudo
become_user=root 提權使用者
become_ask_pass=False 不問提權密碼
#host_key_checking = False 自動接受公鑰 (好用)
log_path=/var/log/ansible.log 普通使用者得改這個路徑
普通使用者寫不了var/log
module_name = command 不指定模組預設為command模組
ad-hoc指令
官方檔案
https://docs.ansible.com/
搜尋模組時搜尋builtin 內建模組
shell模組
優點:功能強大
缺點:無法保證冪等性
ansible servera -m shell -a '命令'
來自官方檔案的教誨(狗頭)
[root@workstation maosible]# ansible servera -m shell -a 'chdir=/tmp pwd'
servera | CHANGED | rc=0 >>
/tmp
[root@workstation maosible]#
[root@workstation maosible]# ansible servera -m shell -a 'creates=/tmp/file pwd'
servera | SUCCESS | rc=0 >>
skipped, since /tmp/file exists
[root@workstation maosible]#
檔案存在,則不執行pwd
removes相反
command模組為預設模組
ansible servera -a 'pwd'
command不允許 > < | 之類。 他會當成字串
raw模組就是被削弱的shell
script模組
讓指令碼在被控端執行
這個指令碼可以不需要執行許可權,因為他會被解析成py檔案,被控端通過執行py檔案執行指令碼
其他常用模組
authorized_keys 分發公鑰
[root@workstation .ssh]# ansible-galaxy collection install ansible.posix -vvv
ansible-galaxy 2.9.11
config file = /etc/ansible/ansible.cfg
configured module search path = ['/root/.ansible/plugins/modules', '/usr/share/ansible/plugins/modules']
ansible python module location = /usr/lib/python3.6/site-packages/ansible
executable location = /usr/bin/ansible-galaxy
python version = 3.6.8 (default, Mar 18 2021, 08:58:41) [GCC 8.4.1 20200928 (Red Hat 8.4.1-1)]
Using /etc/ansible/ansible.cfg as config file
Process install dependency map
Opened /root/.ansible/galaxy_token
Processing requirement collection 'ansible.posix'
Collection 'ansible.posix' obtained from server default https://galaxy.ansible.com/api/
Starting collection install process
Installing 'ansible.posix:1.4.0' to '/root/.ansible/collections/ansible_collections/ansible/posix'
Downloading https://galaxy.ansible.com/download/ansible-posix-1.4.0.tar.gz to /root/.ansible/tmp/ansible-local-5179_oikgerz/tmpqxvizmuo
2.9沒有此內建模組
那麼使用galaxy從網上下載
通過官方檔案發現名字為ansible.posix.authorized_key
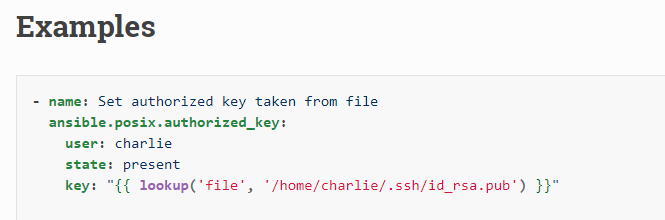
[root@workstation modules]# ansible all -m ansible.posix.authorized_key -a 'user=root key="ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCkQdrj0fMPRQiC7f+1I4N23k/OdwAqt0ONpNDmChbD/ehrJ5lrEspinVtolwBdR5lKnhnWpb9iC29QlR4epd0EdLrId1wRwZ1pMteZuAwR7IlfCCzzSo2ND6gBl1KSIPV4aZhigspFC1JyGAuoB4HIjeZ9NI6w1XP+U/hoGNLjKZtEhPK+H5ijXpb9pVMPvCa0uLYta0qqIMSpIkLlNFUQ1hNd4g4b+aj2y+BzBG/+kYS/7+vDuiBw0GoZ18zmY0ueQjeafg00RNLM/qU90soo29T9tRPc67PozFw20RB8z4LH8Iwe3jzOzGEOWFQ0frJyOg8CgOwDoqMTk4oNjwx4HEOSjv9SsaWYQGZxOkJ5iVZ3MLQt1MkEzhJjibCTMIDlQQ+Dj16hFTMRmM7EXc4AHq1gwURqRv96e0pvmC7RIAFWiPd9IvSSmt4HJB/qGmQjCmvvy84FAGddbEiYGOH2YShzoppBVpxQEsCbHxvZQXJbpwb0uAvn22Pxd5AsH6M= root@workstation" state=present'
參考檔案:https://docs.ansible.com/ansible/latest/collections/ansible/posix/authorized_key_module.html
可是2.9擁有authorized_key
[root@workstation modules]# ansible all -m authorized_key -a 'user=root key="ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCkQdrj0fMPRQiC7f+1I4N23k/OdwAqt0ONpNDmChbD/ehrJ5lrEspinVtolwBdR5lKnhnWpb9iC29QlR4epd0EdLrId1wRwZ1pMteZuAwR7IlfCCzzSo2ND6gBl1KSIPV4aZhigspFC1JyGAuoB4HIjeZ9NI6w1XP+U/hoGNLjKZtEhPK+H5ijXpb9pVMPvCa0uLYta0qqIMSpIkLlNFUQ1hNd4g4b+aj2y+BzBG/+kYS/7+vDuiBw0GoZ18zmY0ueQjeafg00RNLM/qU90soo29T9tRPc67PozFw20RB8z4LH8Iwe3jzOzGEOWFQ0frJyOg8CgOwDoqMTk4oNjwx4HEOSjv9SsaWYQGZxOkJ5iVZ3MLQt1MkEzhJjibCTMIDlQQ+Dj16hFTMRmM7EXc4AHq1gwURqRv96e0pvmC7RIAFWiPd9IvSSmt4HJB/qGmQjCmvvy84FAGddbEiYGOH2YShzoppBVpxQEsCbHxvZQXJbpwb0uAvn22Pxd5AsH6M= root@workstation" state=present'
所以沒必要去下載ansible.posix.authorized_key
但是可以顯示出參考檔案的重要性
那麼遇到問題,可以直接去尋找官方的英文檔案,會更有效率。
以下為轉載
https://cloud.tencent.com/developer/news/327468
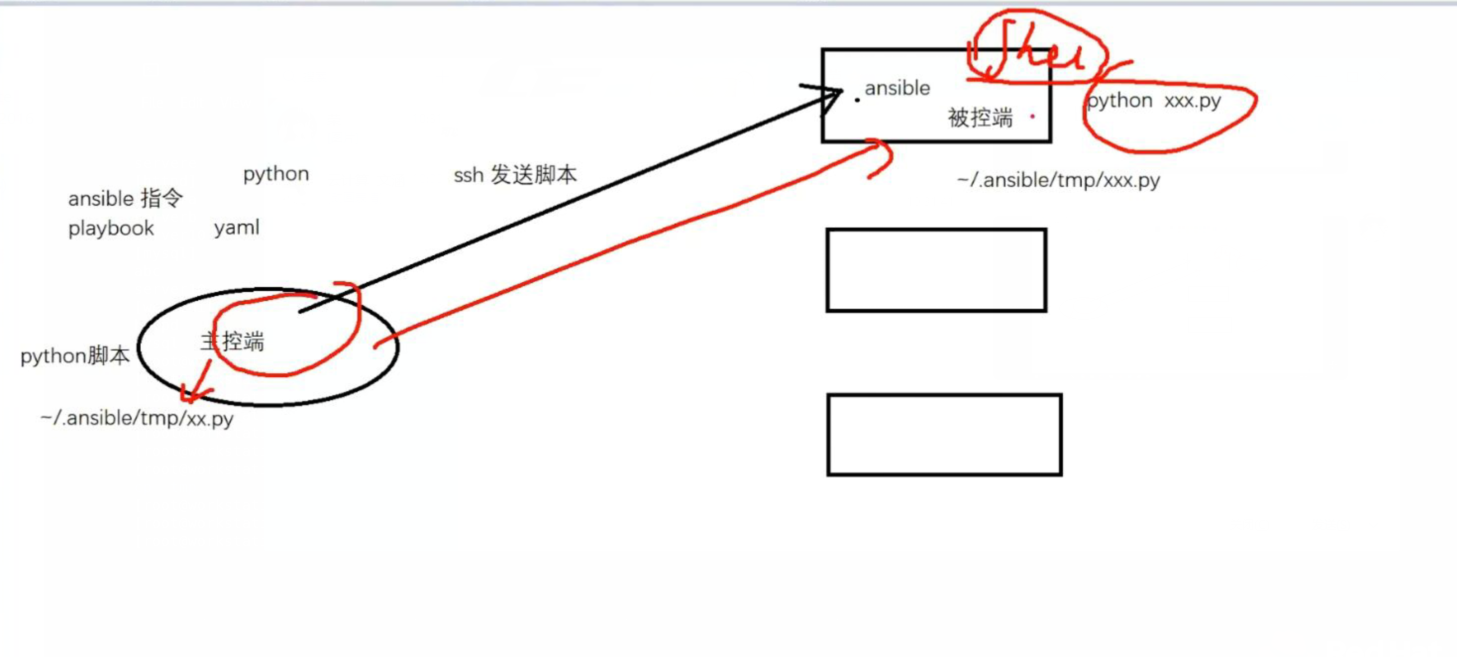
ansible原理
Ansible 是一個模型驅動的設定管理器,支援多節點發布、遠端任務執行。預設使用 SSH 進行遠端連線。無需在被管理節點上安裝附加軟體,可使用各種程式語言進行擴充套件。
一、Ansible基本架構
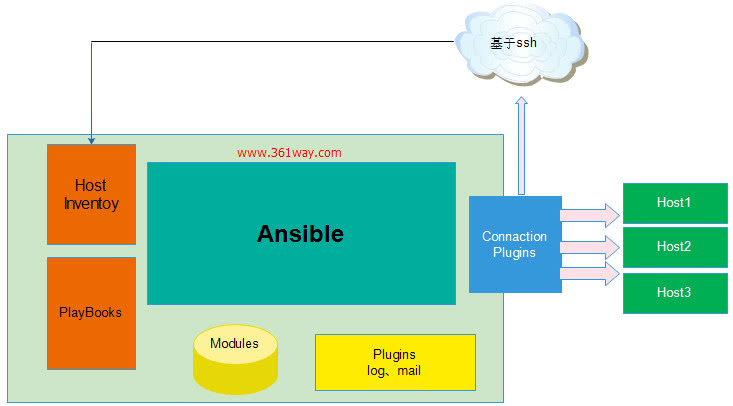
上圖為ansible的基本架構,從上圖可以瞭解到其由以下部分組成:
核心:ansible
核心模組(Core Modules):這些都是ansible自帶的模組
擴充套件模組(Custom Modules):如果核心模組不足以完成某種功能,可以新增擴充套件模組
外掛(Plugins):完成模組功能的補充
劇本(Playbooks):ansible的任務組態檔,將多個任務定義在劇本中,由ansible自動執行
連線外掛(Connectior Plugins):ansible基於連線外掛連線到各個主機上,雖然ansible是使用ssh連線到各個主機的,但是它還支援其他的連線方法,所以需要有連線外掛
主機群(Host Inventory):定義ansible管理的主機
二、Ansible工作原理
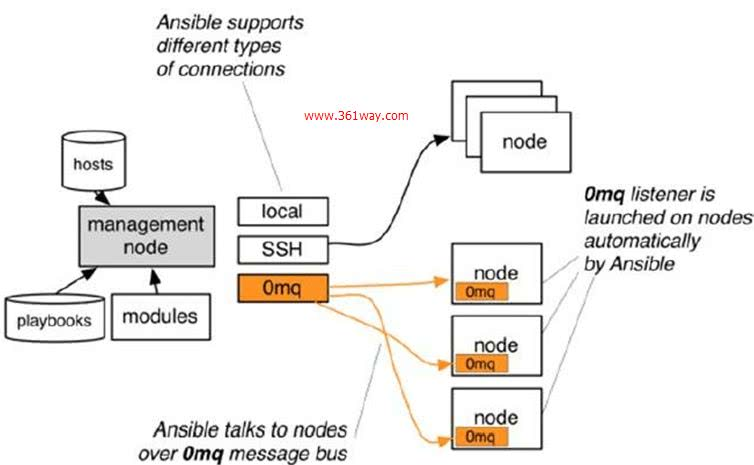
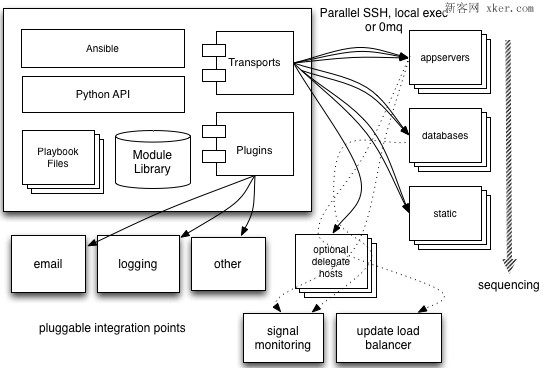
以上是從網上找到的兩張ansible工作原理圖,兩張圖基本都是在架構圖的基本上進行的拓展。從上面的圖上可以瞭解到:
1、管理端支援local 、ssh、zeromq 三種方式連線被管理端,預設使用基於ssh的連線---這部分對應基本架構圖中的連線模組;
2、可以按應用型別等方式進行Host Inventory(主機群)分類,管理節點通過各類模組實現相應的操作---單個模組,單條命令的批次執行,我們可以稱之為ad-hoc;
3、管理節點可以通過playbooks 實現多個task的集合實現一類功能,如web服務的安裝部署、資料庫伺服器的批次備份等。playbooks我們可以簡單的理解為,系統通過組合多條ad-hoc操作的組態檔 。